Not a new thing, but a nice example just popped up in my inbox on my phone.
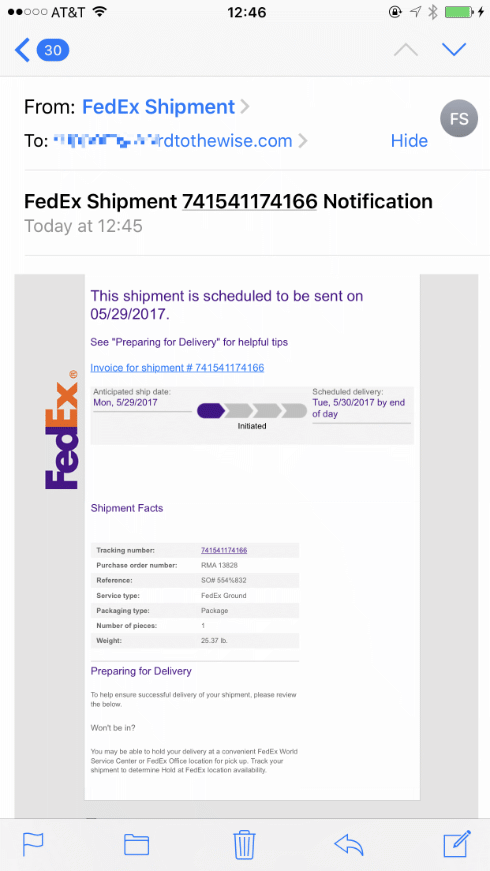
But FedEx solved their entire phishing problem when they published a strict p=reject DMARC record, right?
This didn’t come from fedex.com. It came from another domain that looks vaguely like fedex.com – what that domain is doesn’t matter, as the domain it’s sent from isn’t displayed to the user on my phone mail client. Nor is it displayed to the user by Mail.app on my desktop, unless you turn off Mail → Preferences … → Viewing → Use Smart Addresses.
That lookalike domain could pass SPF, it could be used as d= in DKIM signing, it could even be set up with DMARC p=reject. And the mail is pixel identical to real mail from fedex.com.
On my desktop client I can hover over the link and notice it looks suspicious – but it’s no more suspicious looking than a typical ESP link-tracking URL. And on mobile I don’t even get to do that.
SPF and DKIM and DMARC can temporarily inconvenience phishers to the extent that they have to change the domain they’re sending from, but it’ll have no effect on the vulnerability of most of your audience to being phished using your brand.
DMARC doesn't fix Phishing
D

 RSS - Posts
RSS - Posts
The phishing email surely had a better DMARC score than authentic Fedex shipping notifications. Their DKIM has been broken for over a year:
Received: from mta.message.fedex.com (mta.message.fedex.com [136.147.178.149])
by (envelope-from )
(8.15.2/8.15.2) with ESMTPS id
(version=TLSv1.2 cipher=ECDHE-RSA-AES256-GCM-SHA384 bits=256 verify=NO)
for ; Mon, 22 May 2017 15:08:45 -0400
Authentication-Results: ;
dkim=fail reason=”signature verification failed” (1024-bit key) header.d=fedex.com header.i=@fedex.com header.b=ZxmwEo52
Thank you for the tip on Outlook settings. I loath Outlook but am force to use it at work.