A brief DMARC primer
DMARC stands for Domain-based Message Authentication, Reporting and Conformance. What DMARC does is allow domain owners to publish policy statements in DNS telling receiver domains what to do with messages that do not authenticate. In addition, DMARC introduces the concept of “domain alignment.” What this means is that the authentication has to be from the same domain (or a sub-domain) as the address in the header-from: line. The idea behind DMARC is that organizational owners can use SPF and DKIM authentication to authenticate their actual domain in the header-from line. This moves authentication from a important but behind the scenes technology out to an end user visible technology.
What does alignment mean?
Alignment means that the authenticating domain is related to the domain in the header-from address. There are two kinds of alignment: strict and relaxed. Strict alignment means that the domains are identical, relaxed alignment means that the domains are subdomains of one another.
It’s probably easiest to look at example headers.
In this example we can see a few different things. Visible headers shown in the mail 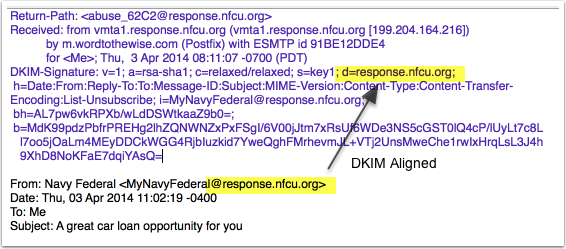 client are in black, headers not normally shown in the client are shown in blue. Highlighted we have the header-from address and the d= value. Both these values are identical, meaning the message passes DMARC with strict alignment. If the header-from was @nfcu.org and d=response.nfcu.org that would pass DMARC with relaxed alignment.
client are in black, headers not normally shown in the client are shown in blue. Highlighted we have the header-from address and the d= value. Both these values are identical, meaning the message passes DMARC with strict alignment. If the header-from was @nfcu.org and d=response.nfcu.org that would pass DMARC with relaxed alignment.
Shouldn’t all mail align?
Not necessarily. In this other example, we see a header-from of @mncompanionrabbit.org but authentication coming from Constant Contact. 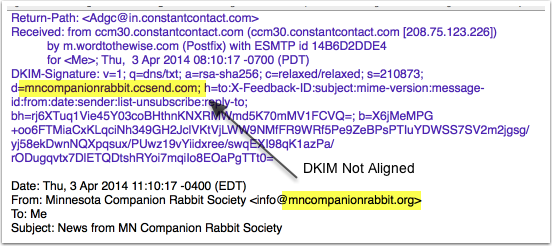 Perfectly legitimate use of the email address in a newsletter, but there is no DMARC alignment as is. Could they create a DMARC alignment? Sure, by signing with a d=mncompanionrabbit.org or
Perfectly legitimate use of the email address in a newsletter, but there is no DMARC alignment as is. Could they create a DMARC alignment? Sure, by signing with a d=mncompanionrabbit.org or by publishing a SPF text record containing Constant Contact’s IP addresses (Corrected because I got this bit very wrong). But there’s not a lot of reason to do that as far as I can see.
Why bring this up now?
Yahoo has recently started publishing a DMARC record with p=reject. This means ISPs checking DMARC records (like yahoo, hotmail, and gmail) and following p= recommendations are now bouncing mail from @yahoo.com addresses that is not sent through Yahoo servers (SPF alignment) or signed with a Yahoo DKIM key (DKIM alignment). This means any mail from Yahoo users not using the Yahoo SMTP servers directly. This is affecting a couple different kinds of Yahoo users, making mail bounce.
Why would Yahoo do this?
There’s been an ongoing attack against Yahoo users attempting to compromise their accounts and then send email from that Yahoo user to their contacts. Yahoo has managed to block this spam coming out through Yahoo’s servers. The attackers have modified their attacks and are now sending mail from Yahoo users to their contacts through other servers. By publishing a p=reject record, Yahoo is telling other systems to not accept mail from Yahoo users if it doesn’t come through Yahoo controlled servers. This includes the mail from the attackers, but also mail from regular Yahoo users that use another SMTP server, including bulk mail sent through ESPs, and individual mail sent to mailing lists.
Will Yahoo change their DMARC record back?
It’s unclear. One of the other features of DMARC is that receivers can report back to senders when there is an authentication failure. Yahoo has these reports so they know exactly how much email is affected by this setting of p=reject. It could be this is a temporary measure until the attackers move on. But this may be a longer term setting because the attacks may be ongoing.
Can I just tell someone to whitelist my mail?
No. This is not an actual block. Mail is being rejected because Yahoo is saying that other companies should reject mail from @yahoo.com addresses that doesn’t come from Yahoo’s servers.
This breaks everything! Who can fix this?
The only people who can change this are Yahoo, no one else is responsible for this. The correct place to complain is support@yahoo. Gmail, Hotmail, anyone else following DMARC, nor the folks at dmarc.org can help you. You need to talk to Yahoo.
What can I do to send mail?
Right now the only way to send mail from @yahoo.com addresses to domains checking DMARC is to send mail using the Yahoo SMTP servers. You can do this by using the web interface, or by using the Yahoo SMTP server to send outbound mail. The only real fix for bulk mail through an ESP is to change your header-from address to something that isn’t Yahoo. I’d also suggest avoiding other free mail domains (like gmail and hotmail).