Cryptography with Alice and Bob
Untrusted Communication Channels
This is a story about Alice and Bob.
Alice wants to send a private message to Bob, and the only easy way they have to communicate is via postal mail.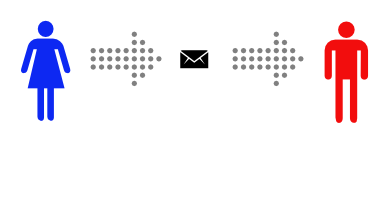
Unfortunately, Alice is pretty sure that the postman is reading the mail she sends.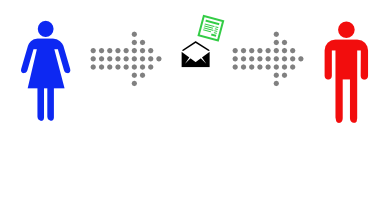
That makes Alice sad, so she decides to find a way to send messages to Bob without anyone else being able to read them.
Symmetric-Key Encryption
Alice decides to put the message inside a lockbox, then mail the box to Bob. She buys a lockbox and two identical keys to open it. But then she realizes she can’t send the key to open the box to Bob via mail, as the mailman might open that package and take a copy of the key.
Instead, Alice arranges to meet Bob at a nearby bar to give him one of the keys. It’s inconvenient, but she only has to do it once.
After Alice gets home she uses her key to lock her message into the lockbox. Then she sends the lockbox to Bob. The mailman could look at the outside, or even throw the box away so Bob doesn’t get the message – but there’s no way he can read the message, as he has no way of opening the lockbox.
Then she sends the lockbox to Bob. The mailman could look at the outside, or even throw the box away so Bob doesn’t get the message – but there’s no way he can read the message, as he has no way of opening the lockbox.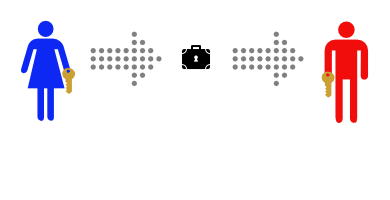
Bob can use his identical key to unlock the lockbox and read the message.
This works well, and now that Alice and Bob have identical keys Bob can use the same method to securely reply.
Meeting at a bar to exchange keys is inconvenient, though. It gets even more inconvenient when Alice and Bob are on opposite sides of an ocean.
Public-Key Encryption
This time, Alice and Bob don’t ever need to meet. First Bob buys a padlock and matching key.
Then Bob mails the (unlocked) padlock to Alice, keeping the key safe.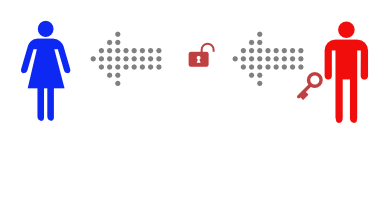
Alice buys a simple lockbox that closes with a padlock, and puts her message in it.
Then she locks it with Bob’s padlock, and mails it to Bob.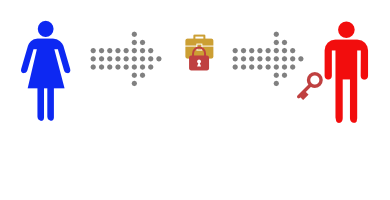
She knows that the mailman can’t read the message, as he has no way of opening the padlock. When Bob receives the lockbox he can open it with his key, and read the message.
This only works to send messages in one direction, but Alice could buy a blue padlock and key and mail the padlock to Bob so that he can reply.
Or, instead of sending a message in the padlock-secured lockbox, Alice could send Bob one of a pair of identical keys.
Then Alice and Bob can send messages back and forth in their symmetric-key lockbox, as they did in the first example.
This is how real world public-key encryption is often done.
- Bob generates a key pair, consisting of his public key (red padlock) and private key (red key).
- Bob then publishes his public key, and Alice fetches it (Bob mails his padlock to Alice).
- Alice then generates a temporary symmetric key (the pair of orange keys) and uses Bob’s public key (red padlock) to securely send it to Bob.
- Bob then uses his private key (red key) to unlock his copy of the symmetric key (orange key).
- Bob and Alice can then use those symmetric keys to securely send messages back and forth.
Each time you click on an SSL link or connect to your mailserver this story plays out. Your browser or mail client plays the part of Alice and the server you’re connecting to plays Bob.