Make Mail.app work for you
Mark Nottingham (@mnot) posted a good idea to twitter:
Highlight e-mails that your MTA receives with TLS. Make sure to include your mail server’s name in the value (here to the left of what’s shown)
Mail.app has client support for mail routing rules. Out of the box all they’re configured to do is highlight mail from Apple, but Mark is adding a rule to passively keep an eye on how mail is being sent to you.
Mark is using it to see who is sending mail over opportunistic TLS – he’s looking for the “with ESMTPS” string that an MTA will add to a Received line when it receives mail sent over TLS. To check that your mailserver records it in the same way, find a recent email sent to you from gmail (who are encrypting everything) and look at the raw source of the mail with View [icon name=”long-arrow-right” class=””] Message [icon name=”long-arrow-right” class=””] Raw Source (or Alt-Command-U) and look for the Received line where your mailserver accepted the mail. The Received line you’re looking for will have “by your.mailserver.name” in it.
Mine looks like this:
Received: from malur.postgresql.org (malur.postgresq
by mx.wordtothewise.com (Postfix) with ESMTPS id
for <steve@blighty.com>; Wed, 10 Sep 2014 21:56:
So I need to set up a rule that looks for a Received header that contains the string “by mx.wordtothewise.com (Postfix) with ESMTPS” and does something with it. You’ll need to do something slightly different, depending on how your mailserver generates Received headers.
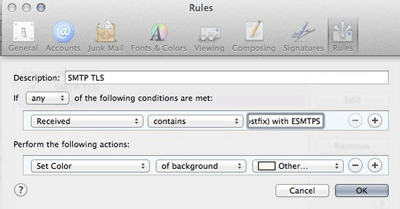
If you go to Mail [icon name=”long-arrow-right” class=””] Preferences… [icon name=”long-arrow-right” class=””] Rules [icon name=”long-arrow-right” class=””] Add Rule you’ll get to this dialog for adding a new rule:
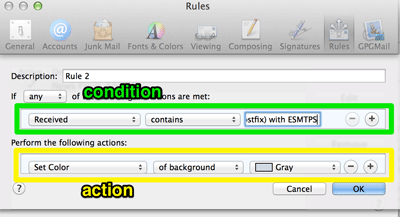
This has two main sections – the upper lets you set a a list of conditions to check incoming mail against, the lower lets you tell Mail.app what actions to take for mails that match.
This is a fairly simple rule with one condition (there’s a received header that contains this string) and one action (highlight this mail in the inbox).
Set the condition as it’s shown above “Received” “contains” “by your.mailserver.name (Postfix) with ESMTPS“. (If there isn’t an option for “Received” in the first combobox you need to select “Edit Header List…” in that combobox to add it first). Then set the action as it’s shown above, to highlight mails that match the condition.
Click OK, and you should be highlighting new mails that match the rule as they arrive. You’ll be able to see who is sending mail via TLS, and who isn’t.
There are lots of other things you could use the same approach to check for. Check the Authentication-Results header for “dkim=pass” (and maybe highlight different key lengths in different colours). Check X-Spam-Status to look for particular SpamAssassin rules firing. Use the contents of the List-ID header to route mail sent to mailing lists to it’s own mailbox reliably. Have Mail.app beep and bounce it’s icon when you receive mail from your boss or your customer, so you can respond promptly even when you’re slacking off on a Friday afternoon …