October 2014 – The Month in Email
October was action-packed at WttW. We wrapped up some big and interesting client projects (look for some case studies soon!), attended another great M³AAWG conference, and made an exciting announcement that we’re hiring a deliverability specialist. The combination of these frees up some more of my time for blogging, which I’ve really missed. Look for more from me in November and December.
In industry news, we’re watching the new Gmail Inbox with interest. We’ll have more to say on this as we play with it and see how different kinds of email interactions occur in the system. As Business Insider noted in their coverage of Forrester’s research on email marketing, consumers are finding good email marketing more and more effective and interesting. Inbox will likely go a long way to help consumers connect with this wanted email and avoid unwanted email. We also revisited an old post on ISP filters and looked at new ways users can control what gets their attention in the inbox.
Steve contributed a few posts this month on technical issues, including a recommendation for SWAKS, the “Swiss Army Knife” of SMTP testing, and a very detailed look at obscure DNS bugs.
In the world of spam, we looked at the first investigative report to come out since the passage of CASL, which suggests that CRTC, the agency responsible for oversight, is being thoughtful in how it addresses complaints. We’ll definitely be keeping an eye on this as the complaints come in. As we discuss in this post (and our other CASL posts), the most interesting piece of this will be in 2017, when individuals can begin to exercise private rights of action.
We also looked at a specific piece of spam we received (ostensibly from Pizza Hut) and used it to talk a bit about spam, phishing and malware. With all of the industry discussion about DMARC as a magic bullet, it’s important to take a good look at the limits of technology and where spammers and bad actors will continue to find ways to work around those limits.
Our most-commented-upon post of the month was about a question we get asked regularly: Does Volume Cause Blocking? (Short answer: no, but a change in volume very well might…)
Finally, we looked at various best practices for email use and administration:
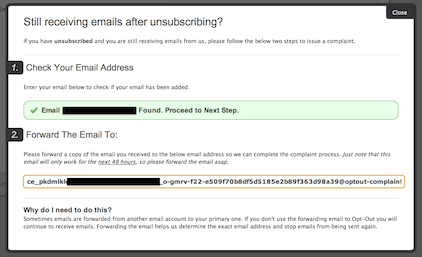
Using disposable addresses to track how your contact information gets used and abused.