I’ve never met a spammer that claims to be a spammer. Most that I’ve met claim to be legitimate marketers (or high volume email deployers). But there are things spammers do that I never expect to see a legitimate marketer doing.
I’ve written about these things throughout the blog (tag: TWSD), but it’s probably time to actually pull them together into a single post.
Use Hashbusters.
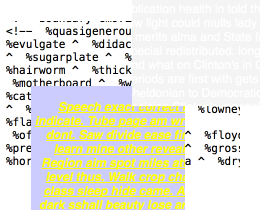
Wikipedia defines a hash as “any function that can be used to map digital data of arbitrary size to digital data of fixed size.” Email filters use hashes as a way of comparing content. Hashbusters are random words and text added to break filters.
Spammers use hash busters to minimize the effectiveness of these techniques by inserting random words or sentences at the end of the email. This text makes differentiates one spam from another, complicating the process of fingerprinting an spam message: it is more difficult for automated analysis to spot a spam message when the messages are no longer identical. The hash buster is sometimes visible to the recipient, while in an HTML email, it can be tagged as white text on a white background so it is essentially invisible to the user. Sophos Security Blog.
Use Many Domains for One Campaign
Related to rotating domains and pulling them out of DNS when a spam run is over is the practice of using many domains for a single campaign. For instance, I received three copies of a spam in one day, each with similar content, but all pointing to different domains. The emails all had the same CAN SPAM address but used the domains householders.biz, prossjelloroda.us, and roffaspcalz.us.
Use Privacy Protection Services to Hide Domain Ownership.
There is no legitimate reason to use privacy protection on a domain used in commercial email. Every commercial email is expected to have a physical address in it, hiding the whois information behind privacy protection is meaningless. What hiding behind privacy protection does do is complicate investigation and hinder people’s ability to see just how many domains a particular company owns.
Rotate Domains or IPs.
Spammers have all sorts of techniques to rotate through IPs and domains. There was a period of time where spammers were using domain tasting to spam free domains. Domain tasting is now legal, but spammers register dozens or thousands of domains and hold on to them. They’ll publish a domain in DNS for 24 – 48 hours, enough for a spam run and to collect some responses, and then they’ll pull the DNS for the domain.
Spammers will also use hundreds of little IP blocks scattered around the web to snowshoe.
Hide CAN SPAM Addresses from Filters.
CAN SPAM requires a postal address to be included in all commercial electronic emails. Spammers who comply with CAN SPAM are at a disadvantage as they have a choice to break the law or get filtered. Some of them have used creative punctuation to break up their CAN SPAM required address to avoid filters. Others decide to use images for CAN SPAM required information. Legitimate companies don’t need to use either technique to hide their CAN SPAM data from filters.
All of these things are things spammers do. Some of these things are things legitimate mailers do (like use domain privacy services). But there are a few things no legitimate mailer will ever do.
- Hashbusters. Using hash busters is a deliberate act to confuse filters. Companies that do this are not sending legitimate mail. Legitimate mailers do not do this.
- Using many domains in a single campaign. There is no benefit to using multiple domains in a single campaign. It’s bad marketing and it’s bad mailing. Legitimate mailers don’t do this.
- Pulling domains out of DNS. This one is actually a CAN SPAM violation, as unsubscribes must be collected for 30 days after a mailing. Legitimate mailers don’t do this.
- Hide CAN SPAM addresses behind images or with strange punctuation. Legitimate mailers don’t do this.

 RSS - Posts
RSS - Posts
Legitimate mailers do use Hashbusters but they call it personalization. The ever growing Filter-Bubble forces hash busting like changes on every mail a legitimate brand sends out and we regularly see blockings because of this.
Tobias, I’m pretty sure that personalization isn’t what Laura means by hash-busting. These changes are minor to the overall document (message body) and don’t disrupt fuzzy hashers much.
A thousand random words added into a HTML comment block however, just screams “Hey, I’m trying to provide more content in this block of BS than the actual marketing copy so as to specifically throw off any fuzzy hashers” … That in itself just screams “Hey, this message is spam,” and I don’t think than many researchers that see this sort of activity really bother with attempting to identify consent or purpose of the message… It’s spam, only spammers do this sort of garbage.
A variation of what Laura said is illegal, using remote images for CAN-SPAM addresses. See ZooBuh, Inc. v. Better Broadcasting, LLC 2013 U.S. Dist.
LEXIS 77033 *22 n. 29 (D. Utah May 31, 2013.)
Also, using hash busters, rotating IP addresses, rotating domain names to bypass spam filers could be considered violations of California Penal Code Section 502. I would say the Computer Fraud and Abuse Act too, but that requires a minimum of $5,000 per year in damages.