Anatomy of a successful phishing attempt
Earlier this year the Exploratorium was the victim of a phishing attack. They’ve posted an article on what happened and how they discovered and dealt with the issue.
But they didn’t just report on the attack, they dissected it. And, as is appropriate for a organization with a mission of education, they mapped out what they discovered during the investigation.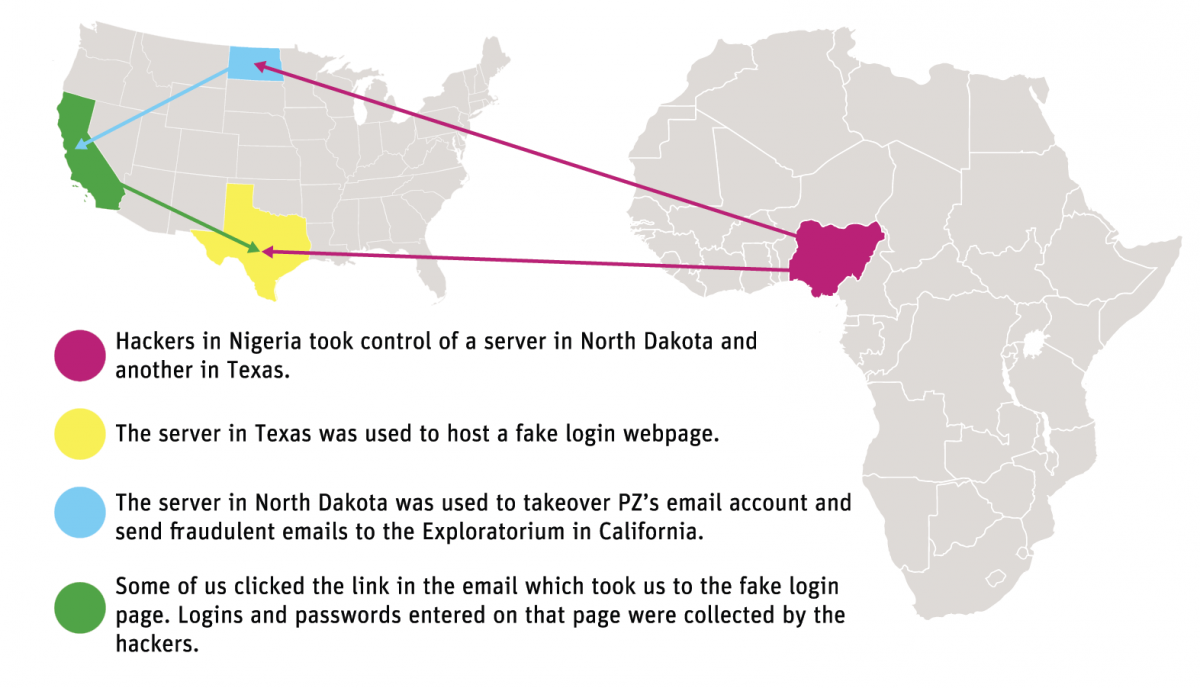
There are a couple of things that stand out to me about this attack. One is that of the more interesting pieces to me is that there was a delay between the compromise and the start of the attack. The Exploratorium calls it “the pivot” and describes it as the hacker deciding what to do next. The second is that the phisher actively interacted with the victim’s account. All new mail was sent to the trash automatically so she wouldn’t see incoming mail. Some mail was actively replied to so more people would click on the message. The phisher took steps to retain access to the account for as long as possible.
One thing that the Exploratorium didn’t see was any actual access to Exploratorium files or information. That may be because the Exploratorium itself wasn’t the target. Once a phisher / hacker has access to the email account, they have access to almost everything in your online life: calendars, bank accounts, credit accounts, the list goes on. Email addresses are our online identity and getting access to the address can open access to so much more.
Quite frankly it can happen to any of us. Earlier this week we received a phishing message that looked very plausible. It came from a law firm, mentioned a subpoena and even had an attachment personalized to our company. The attachment wasn’t opened so we were fine, but I can see how that kind of email might trick someone into getting infected.
We all need to be careful online. Email is a wonderful thing, but it’s insecure. It’s a great way for criminals to get into our space and wreck havoc on our computers and our lives.