Mailbox tools are a security risk
On Sunday the NYTimes published an article about Uber’s CEO. One of the pieces of information that came out of that article is services like unroll.me sell information they scrape out of emails sent to their users.
Uber devoted teams to so-called competitive intelligence, purchasing data from an analytics service called Slice Intelligence. Using an email digest service it owns named Unroll.me, Slice collected its customers’ emailed Lyft receipts from their inboxes and sold the anonymized data to Uber. […]
Slice confirmed it sells anonymized data (meaning that customers’ names are not attached) based on ride receipts from Uber and Lyft, but declined to disclose who buys the information.
Unroll.me is a service that takes user’s commercial email and “rolls it up” into an easy to digest email. Basically users give unroll.me access to their mailboxes, and the company digs through the mail you’ve received in order to organize it. I wrote about them back in 2015 because they were mishandling unsubscribe requests. The issue then was they were not sending unsubscribe requests if the List-Unsubscribe header was a mailto: link. They noticed and then flooded ESPs with requests all at once, causing many people to question if these were legitimate unsubscribes.
What I didn’t realize at the time is that using unroll.me means you are granting a 3rd party application access to your entire mailbox. Their FAQ claims you’re agreeing to “limited access.”
The signup process is quick and easy. Here’s how it works: Click on the “Signup” button on the homepage. Type in your email address. Unroll.me will ask for limited access to your email address using OAuth for Gmail or username/password for all of the other services. After granting limited access, Unroll.me scans your inbox and compiles a list of your email subscriptions.This can take a few moments. Once the scanning process is complete, a list of your email subscriptions will be presented to you. You’ll be able to edit them right away. That’s it! Once you’re done, begin enjoying the Unroll.me experience!
What does that “limited” access look like? This is how Google describes the access unroll.me wants: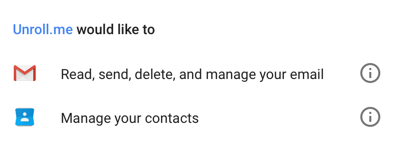
Unroll me has unrestricted access to read, send delete and manage your email. What Google doesn’t know or say is that you are also giving unroll.me permission to sell information and data about your commercial and transactional emails (as defined in CAN SPAM).
We may collect, use, transfer, sell, and disclose non-personal information for any purpose. […] we may collect data from and about the “commercial electronic mail messages” and “transactional or relationship messages” (as such terms are defined in the CAN-SPAM Act (15 U.S.C. 7702 et. seq.) that are sent to your email accounts. […]
We may disclose, distribute, transfer, and sell such messages and the data that we collect from or in connection with such messages; […] all personal information contained in such messages will be removed prior to any such disclosure. […]
We may collect and use your commercial transactional messages and associated data to build anonymous market research products and services with trusted business partners.
Unroll.me isn’t the only provider to access your inbox and sell the data. Boxbe, owned by eDataSource, and Otherinbox, owned by Return Path both access mailboxes to collect user data. That is the “panel data” so many of my readers use to measure deliverability.
The biggest problems with these services is that an email address is more than simply a mailbox. Email addresses are the keys to our online identity. Giving companies like unroll.me, or Return Path or eDataSource access to your mailbox allows those companies access to private data and other online services associated with that email account.
Make a purchase from an online retailer? That receipt is a commercial electronic message. Register an account for an online service? The email with your registration information is a commercial electronic message. Give an app an email address? Any email from that app is a commercial electronic message. Receive bank statements? That email is a commercial electronic message. Use your email account to make an appointment at your doctor’s office? The confirmation email is a commercial electronic message. Reset your password on your iCloud account? The reset email is a commercial electronic message.
Just because a message is commercial does not make it non-personal. Some very personal emails come through commercial services. Emails a lot of people might not want to be public, even aggregated and anonymized.
But it’s not just the commercial messages that are an issue. The services have access to the email account. I looked through all 3 services to figure out if they are looking at all the mail and just taking data from commercial mail, or if they’re just looking at commercial mail. Best I can tell is that they’re reading all mail coming into the account, but only saving data from commercial mail. Or so they say.
For instance, unroll.me claims they do not keep copies of any emails sent to their users. But according to a post on yCombinator, unroll.me is keeping copies of every mail sent to and sent from accounts associated with unroll.me.
I worked for a company that nearly acquired unroll.me. At the time, which was over three years ago, they had kept a copy of every single email of yours that you sent or received while a part of their service. Those emails were kept in a series of poorly secured S3 buckets. A large part of Slice buying unroll.me was for access to those email archives. Specifically, they wanted to look for keyword trends and for receipts from online purchases. karlkatzke
If this is true, there are major issues here. Why are they saving outbound mail? This has nothing to do with incoming commercial mail and tracking trends. There’s no reason to save the outbound messages as it has nothing to do with what commercial email companies are sending. How secure are these S3 buckets?
Notice, too, that the services never discuss how they are identifying commercial messages. They just say they’re only monitoring commercial messages. But what criteria identifies a message as commercial vs. one that identifies a message as personal? I can think of a couple ways to ID commercial messages, but all of them are fraught with false negatives and false positives. Of course, the services fall back on “commercial” and rely on users believing that the service has a magic way to avoid identifying personal email as commercial.
The main takeaway from this is that if you give a third-party access to your mailbox you’re giving them the keys to the kingdom. If you care about your privacy or the security of your personal information you need to be aware of what their actual business model is – that it’s “selling data based on the email you receive” not “cleaning up your mailbox”, for instance. You also need to convince yourself that you completely trust the third party with your data – not just their stated use of it, but also their operational competence and dedication to data security.
Note: Return Path has commented with a statement on how they inform users about info collection and what they do to protect user privacy.