You're kidding me
- steve
- May 17, 2017
- Best practices
All the authentication and DMARC in the world can’t save you from stupid.
I just got a survey request from my bank. Or, at least, it claimed to be from my bank.
From: Barclays International Banking Survey <internationalbanking@barclayssurveys.com>
The mail passed SPF (though the SPF record suggests this is being mailed from all over the place) and was validly DKIM signed for barclayssurveys.com. And that domain has a DMARC policy
But there’s nothing in any of that that tells me – or mail filters – that this has anything to do with Barclays Bank.
“barclayssurveys.com” is what’s know as a cousin domain in the phishing world. It’s a domain that has absolutely nothing to connect it to the legitimate domain of the phishing target, but which looks plausible to a recipient.
This one didn’t actually look that plausible, though. The website is hosted on a RackSpace VPS with no reverse DNS configured. The domain is registered by “chime.plc.uk” – whose website is just an Outlook Web Access instance: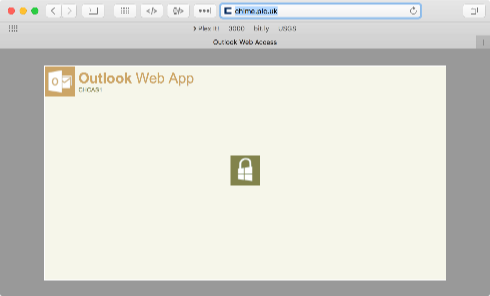
The survey it links to – the survey that is asking the recipient about their interaction with a financial institution – doesn’t use SSL. (The webserver it’s running on does speak SSL, so the issue is that they didn’t have a certificate for barclayssurveys.com). The URL it uses and the javascript it’s running suggests it was originally taken from Wix, the free website hosting platform. And it has references to several survey providers in the source that are hidden by CSS.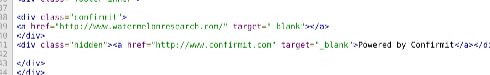
All of which would be suspicious enough if it came from my local dive bar, but this is coming from an international bank that’s big enough, rich enough and technically savvy enough that they own their own top level domain.
No institution can claim to care about phishing or account takeover as an issue when the legitimate email they send is less plausible than a typical phishing mail. This is just setting up their customers to fall for phishing mail.
And, yes, it’s from a legitimate survey firm. One that’s quite widely used in the United Kingdom and Éire. How do I know it’s widely used? Because the mail they send out leaks information about their customers:
X-Confirmit-FixedSenderDomain: factssurvey.co.uk, feedback-waveutilities.co.uk, feedback-anglianwaterbusiness.co.uk, npowersurveys.com, o2surveys.co.uk, gustosurveys.co.uk, customersatisfaction.rbs.co.uk, customersatisfaction.natwest.com, mail.customersatisfaction.rbs.co.uk, mail.customersatisfaction.natwest.com, panel.uk.com, virgintrainseastcoastsurveys.com, barclayssurveys.com, sunnyloanssurveys.com, sagafeedback.co.uk, boxcleversurveys.co.uk, surveys.ulsterbank.ie, sagafeedback.co.uk, barclays.com, titanfeedback.co.uk, barclaycardsurveys.com, aegonfeedback.co.uk, directionsurveys.co.uk
Just from the names I recognize that’s five major high street banks, a payday loan outfit, several utility companies, travel companies and a major cellphone company that are sending survey email that’s this badly done. And that’s probably just the ones that are being sent from this particular mailserver.
I went back and checked where my bank usually sent email from, and how their authentication was normally set up. The previous mail I got from them was a timely warning about “Phishing” and “Smishing” and “Vishing” warning me to be very careful about clicking on links in mail claiming to be from my bank, for fear of being phished.
It was addressed to “%first name%”.
