Did the algorithm change?
When faced with unexplained deliverability changes one of the first questions many folks ask is “Did the algorithm change.” In many ways this is an meaningless question. Why? Because there are two obvious answers to the question.
A1: Of course it didn’t.
A2: Of course it did.
Both answers are correct, but they’re answering different underlying questions. When we understand how two diametrically opposed answers are both correct, we understand much more about filtering.
What is an algorithm?
When we’re talking about spam filtering the algorithm is the process or rules to follow.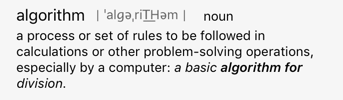
Basically, an algorithm is a computer program that is set up to filter spam to the bulk folder and filter wanted mail into the inbox. This algorithm doesn’t change. It can’t.
In the case of many (most?) spam filters, the filters incorporate features of machine learning. 
This means the algorithm is constantly changing, learning more and more about what is spam and what is wanted mail based on user interactions.
Algorithms don’t change
Overall, the algorithms don’t change that frequently. They are fed data (lots of data) on a continual basis. They take feedback from recipients (spam / not spam buttons) and developers (new data sets of known bad and known good mail) to learn what good mail looks like and what bad mail looks like. But the underlying code doesn’t change very frequently.
Results change
Machine learning algorithms are only as good as the data they’re fed. In the case of spam filters, the input data is constantly changing. So the output results change. Sometimes an email that was not-spam one day is spam the next because the algorithm caught up with a new threat or new behavior. 
Delivery is still in your control
This machine learning and reliance on end users to help tune filters may make it seem like spam filtering is completely out of the senders’ control. That there is nothing a sender can do to get into or out of the bulk folder. The good news is, the underlying algorithms are pretty simple: wanted mail goes to the inbox, unwanted mail goes to the bulk folder. As with everything, details matter. Senders who are focused on recipients usually don’t have a difficult time reaching the inbox. Companies that focus on themselves and try gimmicks find it much harder to consistently reach the inbox.

