What kind of mail do filters target?
- laura
- April 24, 2018
- Delivery improvement
All to often we think of filters as a linear scale. There’s blocking on one end, and there’s an inbox on the other. Every email falls somewhere on that line.![]() Makes sense, right? Bad mail is blocked, good mail goes to the inbox. The bulk folder exists for mail that’s not bad enough to block, but isn’t good enough to go to the inbox.
Makes sense, right? Bad mail is blocked, good mail goes to the inbox. The bulk folder exists for mail that’s not bad enough to block, but isn’t good enough to go to the inbox.
Once we get to that model, we can think of filters as just different tolerances for what is bad and good. Using the same model, we can see aggressive filters block more mail and send more mail to bulk, while letting less into the inbox. There are also permissive filters that block very little mail and send most mail to the inbox.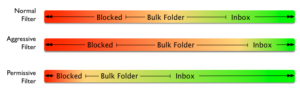 That’s a somewhat useful model, but it doesn’t really capture the full complexity of filters. There isn’t just good mail and bad mail. Mail isn’t simply solicited or unsolicited. Filters take into account any number of factors before deciding what to do with mail.
That’s a somewhat useful model, but it doesn’t really capture the full complexity of filters. There isn’t just good mail and bad mail. Mail isn’t simply solicited or unsolicited. Filters take into account any number of factors before deciding what to do with mail.
What kinds of factors?
There are five broad questions I think about when guiding clients through their email programs.
- Is the mail safe?
- Is the mail solicited?
- Is the mail targeted?
- Is the mail wanted?
- Is the mail productive?
Different filters have different weights for the categories. Those weights explain why delivery can range so widely across domains and email providers.
Let’s look at each set of factors and talk about who might care more about those factors than others.
Is it safe?
Does the message contain malware, phishing, anything that could harm the recipient’s computer or the network as a whole? These filters are widespread and heavily weighted by most people. Safe doesn’t typically come into it for legitimate mail, but the filters are still there and still sniff at our mail.
Is it solicited?
Alternatively, did the user ask to receive mail from the sender? Many blocklists, including Spamhaus, specifically set out to block unsolicited email. They don’t really care about what the email is. They simply want to make sure that the recipients are receiving mail they asked for.
Confirmed opt-in is a way to ensure that mail is solicited. The folks behind many of the blocklists simply want users to receive mail they asked for. Senders who can demonstrate the mail is solicited get removed from the list.
At ISPs, solicited is somewhat important, but the signs of solicited mail overlap with signs of wanted mail. When ISPs measure unknown users and complaints, part of what they’re trying to determine is if the mail is solicited by their user.
Is it targeted?
Does the user understand why they’re receiving the mail? As a small business owner, I get a lot of targeted email. Random companies buy addresses and target me as someone who might want their service. The mail is targeted, so some filters, particularly those at ISPs, might not block or spam folder the mail.
But just because mail is targeted doesn’t mean the user wants it.
Is it wanted?
Does the user want the mail? Sometimes they do, sometimes they don’t. The big webmail providers (Oath, Microsoft, Gmail) heavily weight wanted. They don’t care so much if the message is solicited or targeted, although both things will increase the likelihood that the mail is wanted. At these ISPs, filters really focus on signs that the user is engaged with the message as part of the delivery process. Wanted mail gets into the inbox, unwanted mail not so much.
But just because the mail is wanted doesn’t mean it will make it to the inbox.
Is it productive?
This filter only really comes into effect when we’re talking about mailing into businesses. Email is a tool for businesses and they often want employees to be working while at work. Even if an employee solicits and email a business might decide it’s not productive for the business and they block that source of email. Likewise, businesses will block targeted and wanted messages simply because they’re unproductive.
What’s it all mean?
Effectively addressing delivery problems means understanding why a message isn’t reaching the inbox. Improving engagement isn’t going to help senders reach employee mailboxes if the mail is unproductive. Better targeting won’t help if the block is due to the mail being unsolicited. Using confirmed opt-in won’t magically get malware into the inbox.
It used to be that deliverability recommendations would work across the range of filters. Mail that made it to the inbox at an ISP like Gmail was likely to make it into the inbox almost anywhere. But as Gmail (and Oath and Microsoft) focus more and more on custom delivery for every recipient, recommendations that work there aren’t always going to work elsewhere.
Reaching the inbox outside of webmail providers means taking a lot more into account than just if the recipient is engaged with your mail.
