The Problem With Affiliates (2)
On Friday I mentioned spam coming from a BarkBox affiliate programme.
The original email is here. It’s not terribly exciting, it’s rather typical spam of the sort sent by professional spammers.
It’s validly DKIM and SPF authenticated, and DMARC-aligned. It includes invisible white-on-white padding text so that it doesn’t look like image-only spam to naive filters (using text from the BarkBox wikipedia page). It’s sent from a throwaway CentOS host on a second tier VPS provider. That is a single (templated) machine that handles sending the spam and serves the images and does the clickthrough handling – meaning that there is no reference in the spam to anything other than the throwaway host. And so there’s not really any way to track who the spammer is without subpoena power other than by following the money.
Let’s follow the money.
I’m assuming that the spammer and his associates aren’t using any particularly clever defensive measures against tracking (and if they are, meh, all I’ll have lost is some blog content). So I’m using a simpler approach than I’d use in an actual case, one that’s easier to demonstrate. I’m fetching each link manually with the curl command, and looking at the result manually.
“curl -D- http://example.com” is a really useful curl idiom. By default curl will fetch the page you give it and print out the content. If you add the flag “-D-” it will print the headers of the response as well as the body. That’s particularly important for looking at clickthrough links as in a normal “302 redirect” the destination URL is provided in the Location: header.
The full trace of me checking the chain of redirection links is here.
Hitting the long http://mindpowrr.bid/… link in the email it 302 redirects to https://seenior.bid/aa/bbp3/. seenior.bid feels like it’s probably owned by the same spammer as mindpowrr.bid, just from the misspelling and choice of TLD. It’s hosted on cloudflare, so the hosting is bulletproof and the TLS certificate is useless. The “bbp3” at the end of the URL is suggestive of it being a manually assigned tag for BarkBox promotions.
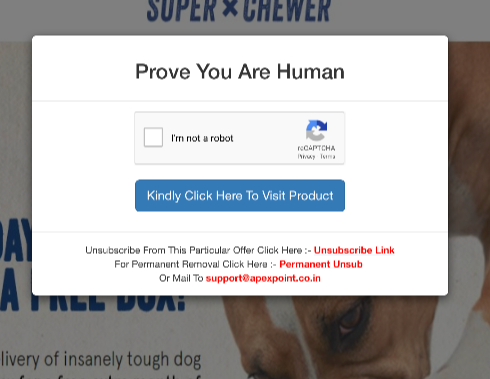
Fetching the seenior.bid URL shows a different way to redirect, a rather creative one. It uses a bootstrap modal component to display a “fake” dialog box with an html form containing a google recaptcha. Clever. People are used to having to click on those to continue, but any automated analysis isn’t going to click on the form submit button.
Clever. (Note those unsubscription links – I’ll come back to them later).
The spammer didn’t bother checking the response from the recaptcha when you submit the form, that’s not what it’s there for. In fact, they don’t even see the form results as the form posts to https://tinyurl.com/yalfp3x9 – and tinyurl is a commercial link redirector, not something that handles forms.
I know tinyurl don’t care whether I send it a GET or a POST, so I just use the same curl command , and tinyurl 302 redirect me to http://trkpaper.com/?a=21966&c=62394&s1=5702BBP3.
trkpaper.com is abovealloffers – an affiliate network. Marketers pay abovealloffers for clicks, abovealloffers pay anyone who provides them with clicks. Because the core of their business is distributing money for clicks it’s critical that abovealloffers keep track of who is sending them traffic. Looking at the URL it’s nicely transparent. “a=21966” is probably the identity of the affiliate (spammer). “s1=5702BBP3” has the same “bbp3” identifier in it, and is probably how abovealloffers are describing the particular campaign BarkBox is paying for. “c=62394”? Not sure, I’d guess it’s a client identifier.
Clicking on the trkpaper.com URL 302 redirects to a URL at https://aboveallurl.com/…, including all the parameters that were passed above.
Following the https://aboveallurl.com/… link does a simple 302 redirect to http://superchewer.barkbox.com/aao/?AFID=21966 – and that’s the advertiser. The AFID shows me that it’s an affiliate programme run by BarkBox rather than anything custom to abovealloffers.
Those unsubscription links are both using bit.ly as a link shortener. I love when people do that, as you can add a “+” on the end of any bit.ly URL to get the tracking metrics. The first one isn’t terribly interesting – it goes to a bland, EC2 hosted generic unsubscription form at “optout-pljz.net”, and has been clicked on three times.
The second one is their global unsub request. It’s been used a bunch of times, and it redirects to a page hosted on apexpoint.co.in. The path of the page is /unsub.php, and it only shows an unsubscription form if passed the right parameters. That tells me that this server is under the control of the spammer, and may belong to the spammer. That support@apexpoint.co.in is used as an alternate unsubscription route means it’s the latter. (And, to sum up just how the spammer approaches things, the unsubscription form doesn’t actually do anything at all if you try and use it).
So … apexpoint.co.in … The whoispocalypse has apparently affected Indian domains, so no help from whois. The website has been locked down, so the root page just throws a (broken) error. It’s hosted on a lower end US provider who’d be responsive to a subpoena but won’t be a source of information without one.
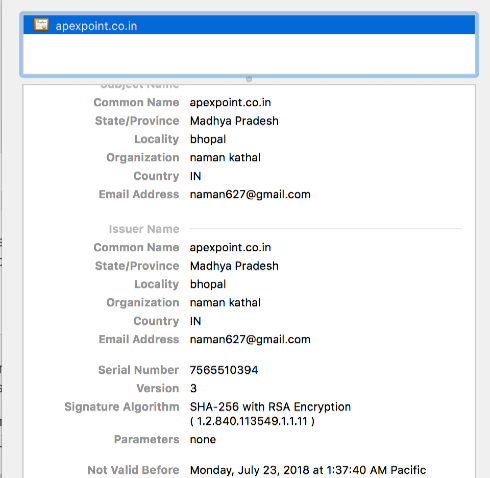
But it’s running a TLS webserver with a self-signed certificate:
Naman Kathal – naman627 – out of Bhopal, Madhya Pradesh province, India.
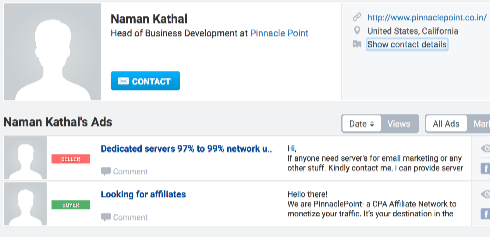
Searching for naman627 finds Naman’s twitter account and several member profiles on affiliate / spammer bulletin boards:
Dedicated servers 97% to 99% network uptime guarantee…
Hi,
If anyone need server’s for email marketing or any other stuff. Kindly contact me, I can provide server with Best Quality and Best Price with 24/7 quality support. You can also contact me on skype ID :- naman.kathal1 for more details.
Thanks
The company mentioned in Naman’s bio is the same one the only Naman Kathal on LinkedIn claims to own. And it’s in Bhopal. And it lists apexpoint.co.in as a project. And it’s website is on the same IP address as apexpoint.co.in. They’re one and the same.
Namal claims to be a CPA affiliate network (what abovealloffers actually is) but I suspect that’s aspirational and the spammer is either Namal himself, or maybe someone he sells his “server’s for email marketing” to.
So what most likely happened is that AboveAllOffers signs up for the BarkBox affiliate programme. BarkBox pay AboveAllOffers for clicks. AboveAllOffers pay anyone who’ll drive traffic to them, including spammers. Neither of them ask too many questions about where the traffic comes from.
BarkBox don’t really advertise their affiliate programme, rather they’ve mentioned it on social media and asked people to contact them via email to sign up for it, but I’ve seen affiliate networks talking about BarkBox promotions offering rates of $16 or 27% of the purchase. Definitely enough to be worthwhile if you’re sending enough email or you’re based out of India. Or both.
And that’s why Indian spammers are pumping out spam advertising BarkBox.