Complaints, contacts and consequences
Yesterday the CRM system Zoho suffered an unexpected outage when their registrar, TierraNet suspended their domain. According to TechCrunch, Zoho’s CEO says there was no notification to the company and that the company had only 3 complaints about phishing.
Based on the article, even as a Zoho customer, I am fully on the registrar’s side here. Every company, absolutely every company that provides service online has a responsibility, even an obligation, to minimise the harm through their service. I have zero doubt that this was an ongoing issue and that TierraNet attempted to contact Zoho multiple times. I also believe that Zoho never got the message.
Why? Too many companies run their abuse and security emails through the same filter that they use for employee emails These filters often block or spam folder reports that contain spam or phishing content. I’ve absolutely had issues where I talk to someone inside a company and then forward them an example of a problem email, only to have their filters eat the email.
But then we did some research. It seems Zoho does have a problem with customers phishing. BUT! They also have a functioning abuse address that acts on complaints.
Over the last 3 years, we’ve sent complaints to Zoho reporting phishing from a number of different customers. Since 2016, they consistently respond and disconnect the phishing site. Sure, the response is boilerplate, but the sites are disconnected.
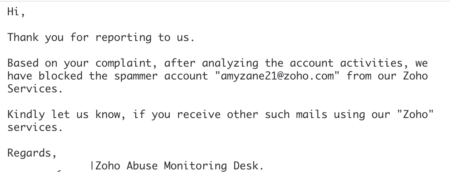
So the comment to TechCrunch from the CEO about only 3 complaints is confusing. We’ve sent more than that, and the abuse desk has acted on the complaints. Maybe the registrar doesn’t have up to date contact information, maybe Zoho thought they were too big to disconnect. In any case, Zoho does have customers using their site to send phishing mail, but they also appear to have a functional abuse desk that’s handling the complaints.
Alternatively, it’s possible TierraNet that has the non functional abuse desk. They wouldn’t be the first registrar to have horrible processes resulting in customers losing connectivity when they didn’t deserve it.
All of this is a good example of how challenging compliance is, and how complex managing networks can be.
Compliance is hard
The underlying moral here is that compliance is a vital part of offering any service online. Compliance is also hard and requires smart, engaged, empowered people with the right tools.
Nearly 20 years ago I wrote my first compliance desk process document. I was managing a team working at a very large provider. Some of our customers were companies you may have heard of: eBay, Hotmail, Geocities, Napster. Some of our customers were actually large providers themselves and had customers of their own.
As the compliance team our job was to minimize the abuse going through our network. But it wasn’t as simple as shutting down anyone we got complaints about. We had to investigate to see if the complaints were legitimate, did we have evidence that there was a violation here? If there was, we needed to take appropriate action. That action was rarely “shut the customer down.” Why? There were contracts and SLAs and millions of dollars of monthly revenue at stake.
I remember having a rather heated discussion with folks on the team. They thought we, as a contracted abuse desk, should have the power to shut down any customer at any time. There is no way you want an outside contractor with that type of power and lack of oversight. It simply was a bad business decision to allow us to shut down all of eBay because one of their users sent spam linking to an auction. It was a bad business decision to shut down a company as large as eBay without warning, period. We needed processes to make sure that we gave customers with their own customers the tools and information they needed to manage their abuse. Sure, we had the ability to force them to take action, as we could shut them down. But not every compliance relationship needs to be combative.
Communication is vital
Setting up good processes are vital. I’m working with multiple clients right now to help them work through how to set up their own compliance desks. These customers also have to make sure they stay in communication with their upstream compliance desk. Everyone has to have good contact information for each other. Maybe the Zoho / TierraNet problem was simply a Zoho employee moved on and everyone forgot to update their point of contact with the registrar. When the registrar sent the notifications, they may have gone to an empty mailbox (or a spamtrap!) or an employee who had no idea what to do with it.
Still, simply disconnecting a company as big as Zoho, with so many vital services running off it, was something that shouldn’t have been done lightly. And maybe it wasn’t. In any case, this ended up being bad publicity for TierraNet, a bad experience for Zoho and it didn’t really protect anyone. The consequence for poor compliance handling and poor communication is Zoho and all their customers are off the air. TierraNet looks bad and is likely to lose some customers. The travesty is that end users are no safer than they were before this whole thing happened.
What next?
I’m a big believer that every online service needs some sort of compliance desk. Yes, even if you are a CRM provider. Even if you are a small social networking site designed for certain types of clubs. If you provide services to third parties, you need to have some sort of way to make sure your customers don’t create problems online.
Providers that offer services to other providers need to make sure their compliance desk has a clear path of escalation. They can’t, and shouldn’t, take all compliance away from customers by default. But they should also have processes for disconnecting even the big customers.
Compliance is complicated. It’d be lovely if it could be automated, but there is no AI that can make the complex decisions required for an effective compliance desk. Sure, a lot of the work can be automated, a lot of the decisions can be automated even. But there will always be cases that need trained, experienced, smart people to navigate effectively.