Dead addresses tell us things
- laura
- March 21, 2019
- Delivery improvement
There was confirmation this week that the increase in “user unknown” messages from Yahoo is actually Yahoo cleaning out abandoned accounts. At the same time a Yahoo is sending out notifications to folks to log into mail.

The first thing every sender should do is remove all these Yahoo addresses from their lists. They’re done, kaput. Gone.
There are some other things worth doing with them, though. Some of these things are informative, they will help help you understand your subscribers and list lifecycle better. Others are protective, they will improve your data hygiene over the long term.
We know that Yahoo disabled a bunch of email addresses that have not been in use for at least a year. There are some other bits of information we have that give us a broader picture of what is happening.
- About a year ago, this same thing happened. There was an increase in the number of user unknowns at Yahoo (Thanks, Tara, for noticing I wrote about it last year). It’s possible that they’re scheduling address purges on a yearly basis.
- I mentioned reports of an increase in user unknowns from Yahoo in April 2013.
- Yahoo is sending mail to users alerting them that if they don’t log into their mail accounts they’ll lose access to mail – I got one of these to the address tied to my flickr account.
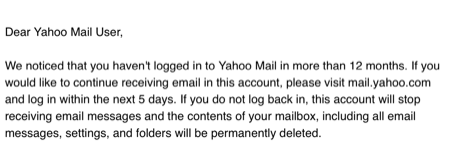
Based on this information, I presuppose the following.
- Yahoo has an process for reviewing and disabling accounts that happens in the early spring and has done for at least 5 years.
- The addresses that started bouncing recently are accounts that have been not logged into for between 12 and 23 months. 12 because this is what the re-engagement campaigns are indicating. 23 because we can assume that some addresses were at 11 months for the disabling a year ago.
We have a known population of yahoo.com addresses that we can assume were abandoned between April 2017 and March 2018. Now you know how many Yahoo addresses go bad in a 11 – 12 month period.
We can ask questions about those addresses that will give us more insight into our subscriber list and how we should handle expiring addresses and data hygiene.
- When did those addresses join your list?
- When was the last open? click?
- Is that address associated with an active login or purchasing account?
With a known population of freemail addresses and some certainty on when the recipients stopped logging into their accounts we can develop data hygiene rules that make sense for our business. It’s not just picking a certain period of time to stop mailing. We can model the behaviour of freemail users knowing when they abandoned their accounts and make sensible policies.