Comparing DKIM keys
Sometimes we have a client who has done something wrong when setting up authentication. Their DKIM signing fails due to something being wrong with the public key they’ve published.
The published key looks fine, by eye. It’s got all the fields it should have, but diagnostic tools give inscrutable error messages.
If you’re lucky, “This doesn’t seem to be a valid RSA public key: RSA.xs:194: OpenSSL error: too long”.
Or, if you’re not, “key syntax error: asn1: structure error: tags don’t match”.
But we gave them the TXT record to use. Where did it go wrong? Time to show off your unix commandline skills.
First, lets get the DKIM TXT record the client has published:
% dig +short selector._domainkey.client.com txt | tr -d '"' >badkey.txtCode language: JavaScript (javascript)And paste the TXT record we gave them into a file. If we’re on a mac and it’s in our clipboard we can use pbpaste.
% pbpaste >goodkey.txtCode language: CSS (css)Or we can use echo and paste the key into the terminal. Handy if we need to copy and paste out of a web interface a chunk at a time.
% echo -n "v=DKIM1; ... DAQAB" >goodkey.txtCode language: PHP (php)Take a quick look at the two files, to make sure they both look vaguely like a DKIM record, and they’re in roughly the same format – no stray double quotes or whitespace.
Then we can use diff to compare the two files.
diff goodkey.txt badkey.txtCode language: CSS (css)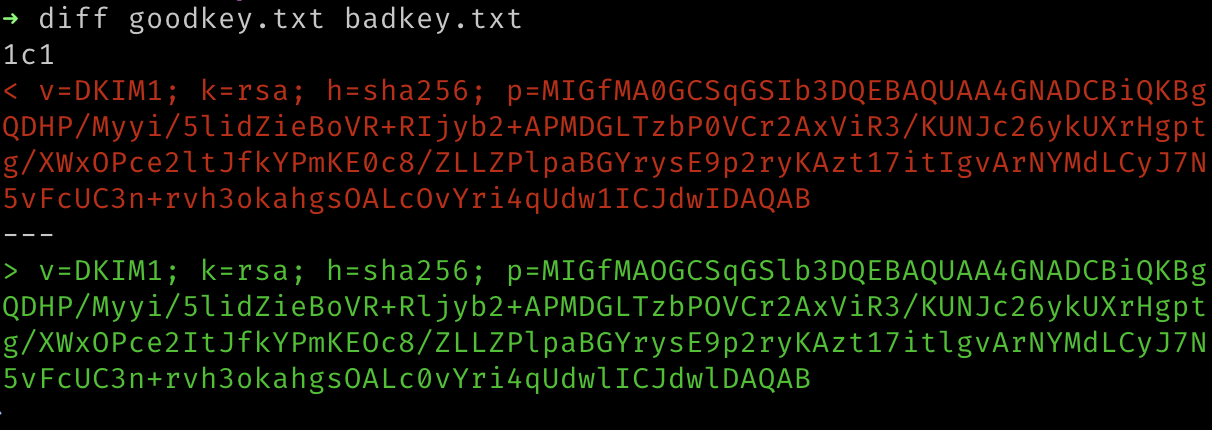
Well, OK. That tells us they’re different. If they were identical diff wouldn’t have printed anything. (Try diff goodkey.txt goodkey.txt if you want to check that).
diff only compares files line-by-line, so if the file is only one line long it doesn’t give any useful details. So we want to convert them to multiline files that we can diff more easily. We’re going to use an old-school tool to do that, “od“.
od is usually used for printing binary files as something readable. Today we’re going to use “od -c” which displays a file showing printable ascii bytes as their characters.
% od -c goodkey.txt >good-od.txt
% od -c badkey.txt >bad-od.txtCode language: CSS (css)
“od -c” puts 16 bytes of the input file on to each line of it’s output, starting with the offset (in hexadecimal) within the file.
Let’s try diff again.

Better. We can see where in the file there are differences. The red and green output are from the two files we’re comparing. Looking at the first red and green lines we can see they’re nearly identical, but the third character in the chunk is a zero in one file and a capital O in the other. And the 10th is an upper case I in one file and a lower case L in the other. Looking at other chunks we can see they’ve confused L and one and I, and O and zero in several places.
So there’s your problem. The client typed the DKIM record you gave them into their DNS management interface by hand rather than copying and pasting.
Can we do better? Sure. There are lots of tools that are like diff but with useful extra features. If you have “git” installed you can use it’s diff tool:
git diff --word-diff=color --word-diff-regex=. --no-index goodkey.txt badkey.txt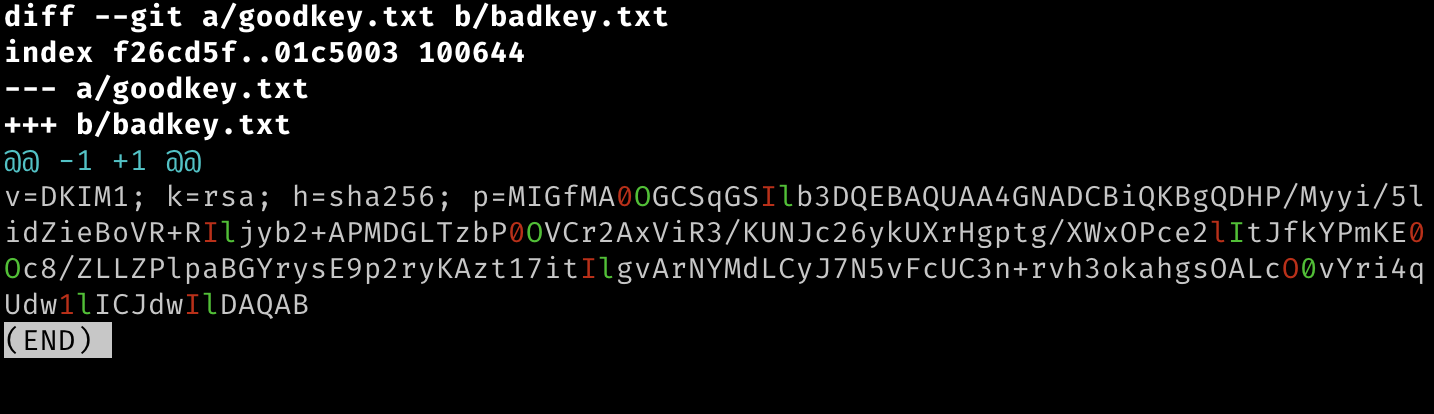
This shows the two keys with just the differences highlighted in green and red. It makes it easy to see that the two are nearly identical but have a smattering of one character errors.
Hopefully you won’t need this often, but when you do it’s a useful set of tools to have in your toolbox.