Recent Posts
… until it stops moving
Nothing is impossible to kill. It’s just that sometimes after you kill something you have to keep shooting it until it stops moving.Mira Grant, Feed
Read More
Compromising a Mail Client
Your entire work life is in your work mail client.
All the people you communicate with – co-workers, friends, family, vendors, customers, colleagues.
Every email you send. Every email you receive. Any files you attach or receive.
If someone can compromise your mail client, they can see all that.
They can save copies of all your emails, data-mine them and use them for whatever purpose they like. They can build a view of your social network, based on who you exchange emails with, and a model of who you are, based on what you talk about.
That companies like Google do this for “free”, advertising supported webmail shouldn’t be much of a surprise by now – but your corporate email system and your work email is secure, right?
What if an attacker were to set up a man-in-the-middle attack on your employees? Install malware on their iPhone, such that all traffic were transparently routed through a proxy server controlled by the attacker?
Or they could use a more email-centric approach, configuring the compromised mail client to fetch mail from an IMAP server controlled by the attacker that took the employees credentials and passed them through to their real corporate IMAP server – that would let the attacker completely control what the compromised user saw in their inbox. As well as being able to read all mail sent to that user, they could silently filter mail, they could deliver new mail to the users inbox directly, bypassing any mail filters or security. They could even modify the contents of email on-the-fly – adding tracking links, redirection URLs or injecting entirely new content into the message.
Similarly, the attacker could route all outbound mail through a man-in-the-middle smarthost that copied the users credentials and used them to send mail on to their real corporate smarthost. As well as being able to read and modify all mail sent the attacker could also use that access to send mail that masqueraded as coming from the user.
Sounds like the sort of thing you’d expect from criminal malware? Not quite. What I’ve just described is Intro, a new product from LinkedIn.
LinkedIn will be asking your users to click on a link to install a “security profile” to their iPhones. If they do, then LinkedIn will have total control over the phone, and will use that to inject their SMTP and IMAP proxies into your users mailstreams. The potential for abuse by LinkedIn themselves is bad enough – I’ve no doubt that they’ll be injecting adverts for themselves into the mailstream, and their whole business is based on monetizing information they acquire about employees and their employers. But LinkedIn have also been compromised in the past, with attackers stealing millions of LinkedIn user credentials – if they can’t protect their own users credentials, I wouldn’t trust them with your employees credentials.
You might want to monitor where your employees are logging in to your servers from – and suspend any accounts that log in from LinkedIn network space.
Edit: Bishop Fox has looked at Intro too, and come to similar conclusions. TechCrunch too.
The J.D. Falk award 2013
M3AAWG awarded the second J.D. Falk award today in Montreal. The winner was Gary Warner from the University of Alabama.
Gary has been involved in fighting abuse and online crime since the 1990s. He developed the Center for Information Assurance and Joint Forensics Research at the University. This is an education program that not only teaches students about online threats and how to fight them, but collaborates with both industry experts and law enforcement.
You can check out Gary at his blog or on twitter.
Experian selling data to identity thieves
If you’re not following or reading Brian Krebs, you should be. He does some of the best investigative reporting in the email, security and internet space. Today’s blog post is a disturbing look into the data selling and identity theft industries. Brian details evidence that shows Experian (yes, that Experian) has been selling consumer data to identity thieves.
Misdirected email
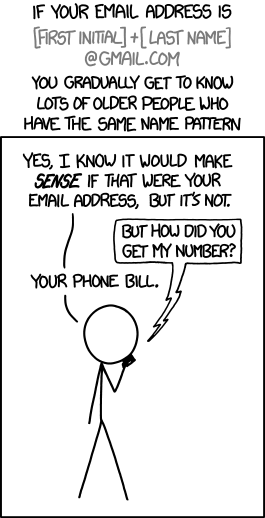
While this does seem to be more common with gmail addresses, it’s not solely limited to gmail. I’ve written about this frequently.
Everything leaks eventually
We have a role address we use to receive support requests from users of our Abacus ticketing system – they’re typically abuse or security desk administrators at ISPs or ESPs, inside corporate firewalls and protected by multiple layers of security and malware protection.
We’ve been using it since around 1997, so we’ve had a good, spam-free run, but in the past few days it’s started receiving botnet originated malware.
If you give an email address to other people, eventually it’ll leak and start receiving spam and malware.
Looking for some experiences…
… with emailreg.org. A client of mine asked today if it was worth registering domains with emailreg.org as a whitelisting process. I’ve asked a few delivery folks for their feedback, but I was wondering what the broader email community thought. Does registering there help delivery to domains behind barracuda processes? Drop me a line on our contact page or add your experiences in the comments.
I normally reject comments with fake or forged email addresses. Because this may be sensitive and some commenters may want to be anonymous, I’ll let anonymous comments through if they’re clearly not forging someone else’s address.
Is it real or is it spam?
The wanted but unexpected email is one of the major challenges facing ISPs and filter developers. If there was never any need or desire for people to receive email from someone they don’t know, then mail clients could be locked down to only accept mail from addresses on a whitelist. It wouldn’t completely solve the spam problem, for a number of reasons, but it would lessen the problem, particularly for average email users.
But, we don’t live in a world where we know beforehand who will be sending us mail, so we can’t just whitelist correspondents and reject everything else. I think this is a good thing. Email can be used to meet new people, develop new relationships and introduce new opportunities.
While the “cold call” email isn’t much talked about I think it’s worth some discussion. What makes a good cold email? What makes a bad one? We can use two recent emails I received as examples.
Example 1:
No, I'm really not Christine
Got this to one of my accounts recently.
Congratulations and welcome to emailinform.
Read MoreSORBS – back soon
If you’ve tried to get an address delisted from SORBS this week you’ll have found that their site is degraded, and there’s no way to request delisting.
They’ve been dealing with some very nasty database / hardware problems and while they’re fixing those the externally visible SORBS services are running in a read-only mode (where the list is published, but IP addresses can’t be added or removed).
The migration to new infrastructure is going well, and unless something unexpected happens I’d guess they’ll be running normally some time tomorrow.
Categories
Tags
- 2010
- 2016
- 2fa
- 419
- 4xx
- 554
- 5xx
- @
- Aarp
- Abacus
- Abandoned
- Aboutmyemail
- Abuse
- Abuse Desk
- Abuse Enforcement
- Abuse Prevention
- Academia
- Accreditation
- Acme
- Acquisition
- Address Book
- Addresses
- Administrivia
- Adsp
- Advanced Delivery
- Advertiser
- Advertising
- Advice
- Affiliate
- Affiliates
- After the Email
- Alerts
- Algorithm
- Alice
- Alignment
- Allcaps
- Alt Text
- AMA
- Amazon
- Amp
- Amsterdam
- Analysis
- Anecdotes
- Anti-Spam
- Anti-Spam Laws
- Anti-Spammers
- Antwort
- AOL
- Appeals
- Appearances
- Appending
- Apple
- Arc
- Arf
- Arrest
- Arrests
- Ascii
- Asides
- Ask Laura
- Askwttw
- Assertion
- Assumptions
- ATT
- Attacks
- Attention
- Attrition
- Audit
- Authentication
- Authentication. BT
- Autonomous
- Award
- B2B
- B2C
- Backhoe
- Backscatter
- Banks
- Barracuda
- Barry
- Base64
- Base85
- Bcp
- Bear
- Bears
- Behaviour
- Benchmark
- BESS
- Best Practices
- Bgp
- Bimi
- Bit Rot
- Bitly
- Bizanga
- Black Friday
- Blackfriday
- Blacklist
- Blacklists
- Blast
- Blo
- Block
- Blockin
- Blocking
- Blocklist
- Blocklisting
- Blocklists
- Blocks
- Blog
- Blog Links
- Blogroll
- Blogs
- Bob
- Boca
- Bofa
- Book Review
- Bot
- Botnet
- Botnets
- Bots
- Bounce
- Bounce Handling
- Bounces
- Branding
- Brands
- Breach
- Breaches
- Breech
- Bronto
- Browser
- Bsi
- Bucket
- Bulk
- Bulk Folder
- Bulk Mail
- Business
- Business Filters
- Buying Leads
- Buying Lists
- C-28
- CA
- Caa
- Cache
- Cadence
- CAH
- California
- Campaign
- CAN SPAM
- Canada
- Candy
- Candycandycandy
- Canonicalization
- Canspam
- Captcha
- Career Developmnent
- Careers at WttW
- Cargo Cult
- Case Law
- Cases
- CASL
- Cat
- Cbl
- CDA
- Cert
- Certification
- CFL
- Change
- Charter
- Cheat
- Cheese
- Choicepoint
- Choochoo
- Christmas
- Chrome
- Cidr
- Cisco
- Civil
- Clear.net
- Clearwire.net
- Cli
- Click
- Click Through
- Click Tracking
- Clicks
- Clickthrough
- Client
- Cloudflare
- Cloudmark
- Cname
- Co-Reg
- Co-Registration
- Cocktail
- Code
- COI
- Comcast
- Comments
- Commercial
- Communication
- Community
- Comodo
- Comparison
- Competitor
- Complaint
- Complaint Rates
- Complaints
- Compliancce
- Compliance
- Compromise
- Conference
- Conferences
- Confirmation
- Confirmed (Double) Opt-In
- Confirmed Opt-In
- Congress
- Consent
- Conservatives
- Consistency
- Constant Contact
- Consultants
- Consulting
- Content
- Content Filters
- Contracts
- Cookie
- Cookie Monster
- COPL
- Corporate
- Cost
- Court Ruling
- Cox
- Cox.net
- Cpanel
- Crib
- Crime
- CRM
- Crowdsource
- Crtc
- Cryptography
- CS&M
- CSRIC
- CSS
- Curl
- Customer
- Cyber Monday
- Czar
- Data
- Data Hygiene
- Data Security
- Data Segmentation
- Data Verification
- DBL
- Dbp
- Ddos
- Dea
- Dead Addresses
- Dedicated
- Dedicated IPs
- Defamation
- Deferral
- Definitions
- Delays
- Delisting
- Deliverability
- Deliverability Experts
- Deliverability Improvement
- Deliverability Summit
- Deliverability Week
- Deliverability Week 2024
- Deliverabiltiy
- DeliverabiltyWeek
- Delivery Blog Carnival
- Delivery Discussion
- Delivery Emergency
- Delivery Experts
- Delivery Improvement
- Delivery Lore
- Delivery News
- Delivery Problems
- Dell
- Design
- Desks
- Dhs
- Diagnosis
- Diff
- Dig
- Direct Mag
- Direct Mail
- Directives
- Discounts
- Discovery
- Discussion Question
- Disposable
- Dk
- DKIM
- Dkimcore
- DMA
- Dmarc
- Dns
- Dnsbl
- Dnssec
- Docs
- Doingitright
- Domain
- Domain Keys
- Domain Reputation
- DomainKeys
- Domains
- Domains by Proxy
- Dontpanic
- Dot Stuffing
- Dotcom
- Double Opt-In
- Dublin
- Dyn
- Dynamic Email
- E360
- Earthlink
- Ec2
- Ecoa
- Economics
- ECPA
- Edatasource
- Edns0
- Eec
- Efail
- Efax
- Eff
- Election
- Email Address
- Email Addresses
- Email Change of Address
- Email Client
- Email Design
- Email Formats
- Email Marketing
- Email Verification
- Emailappenders
- Emailgeeks
- Emails
- Emailstuff
- Emoji
- Emoticon
- Encert
- Encryption
- End User
- Endusers
- Enforcement
- Engagement
- Enhanced Status Code
- Ennui
- Entrust
- Eol
- EOP
- Epsilon
- Esp
- ESPC
- ESPs
- EU
- Ev Ssl
- Evaluating
- Events
- EWL
- Exchange
- Excite
- Expectations
- Experience
- Expires
- Expiring
- False Positives
- FAQ
- Fathers Day
- Fbl
- FBL Microsoft
- FBLs
- Fbox
- FCC
- Fcrdns
- Featured
- Fedex
- Feds
- Feedback
- Feedback Loop
- Feedback Loops
- Fiction
- Filter
- Filter Evasion
- Filtering
- Filterings
- Filters
- Fingerprinting
- Firefox3
- First Amendment
- FISA
- Flag Day
- Forensics
- Format
- Formatting
- Forms
- Forwarding
- Fraud
- Freddy
- Frequency
- Friday
- Friday Spam
- Friendly From
- From
- From Address
- FTC
- Fussp
- Gabbard
- Gdpr
- Geoip
- Gevalia
- Gfi
- Git
- Giveaway
- Giving Up
- Global Delivery
- Glossary
- Glyph
- Gmail
- Gmails
- Go
- Godaddy
- Godzilla
- Good Email Practices
- Good Emails in the Wild
- Goodmail
- Google Buzz
- Google Postmaster Tools
- Graphic
- GreenArrow
- Greylisting
- Greymail
- Groupon
- GT&U
- Guarantee
- Guest Post
- Guide
- Habeas
- Hack
- Hacking
- Hacks
- Hall of Shame
- Harassment
- Hard Bounce
- Harvesting
- Harvey
- Hash
- Hashbusters
- Headers
- Heartbleed
- Hearts
- HELO
- Help
- Henet
- Highspeedinternet
- Hijack
- History
- Holiday
- Holidays
- Holomaxx
- Hostdns4u
- Hostile
- Hostname
- Hotmail
- How To
- Howto
- Hrc
- Hsts
- HTML
- HTML Email
- Http
- Huey
- Humanity
- Humor
- Humour
- Hygiene
- Hypertouch
- I18n
- ICANN
- Icloud
- IContact
- Identity
- Idiots
- Idn
- Ietf
- Image Blocking
- Images
- Imap
- Inbox
- Inbox Delivery
- Inboxing
- Index
- India
- Indiegogo
- Industry
- Infection
- Infographic
- Information
- Inky
- Inline
- Innovation
- Insight2015
- Integration
- Internationalization
- Internet
- Intuit
- IP
- IP Address
- Ip Addresses
- IP Repuation
- IP Reputation
- IPhone
- IPO
- Ipv4
- Ipv6
- Ironport
- Ironport Cisco
- ISIPP
- ISP
- ISPs
- J.D. Falk Award
- Jail
- Jaynes
- JD
- Jobs
- Json
- Junk
- Juno/Netzero/UOL
- Key Rotation
- Keybase
- Keynote
- Kickstarter
- Kraft
- Laposte
- Lavabit
- Law
- Laws
- Lawsuit
- Lawsuits
- Lawyer
- Layout
- Lead Gen
- Leak
- Leaking
- Leaks
- Legal
- Legality
- Legitimate Email Marketer
- Letsencrypt
- Letstalk
- Linked In
- Links
- List Hygiene
- List Management
- List Purchases
- List the World
- List Usage
- List-Unsubscribe
- Listing
- Listmus
- Lists
- Litmus
- Live
- Livingsocial
- London
- Lookup
- Lorem Ipsum
- Lycos
- Lyris
- M3AAWG
- Maawg
- MAAWG2007
- Maawg2008
- MAAWG2012
- MAAWGSF
- Machine Learning
- Magill
- Magilla
- Mail Chimp
- Mail Client
- MAIL FROM
- Mail Privacy Protection
- Mail Problems
- Mail.app
- Mail.ru
- Mailboxes
- Mailchimp
- Mailgun
- Mailing Lists
- Mailman
- Mailop
- Mainsleaze
- Maitai
- Malicious
- Malicious Mail
- Malware
- Mandrill
- Maps
- Marketer
- Marketers
- Marketing
- Marketo
- Markters
- Maths
- Mcafee
- Mccain
- Me@privacy.net
- Measurements
- Media
- Meh
- Meltdown
- Meme
- Mentor
- Merry
- Messagelabs
- MessageSystems
- Meta
- Metric
- Metrics
- Micdrop
- Microsoft
- Milter
- Mime
- Minimal
- Minshare
- Minute
- Mit
- Mitm
- Mobile
- Models
- Monitoring
- Monkey
- Monthly Review
- Mpp
- MSN/Hotmail
- MSN/Hotmail
- MTA
- Mua
- Mutt
- Mx
- Myths
- Myvzw
- Netcat
- Netsol
- Netsuite
- Network
- Networking
- New Year
- News
- News Articles
- Nhi
- NJABL
- Now Hiring
- NTP
- Nxdomain
- Oath
- Obituary
- Office 365
- Office365
- One-Click
- Only Influencers
- Oops
- Opaque Cookie
- Open
- Open Detection
- Open Rate
- Open Rates
- Open Relay
- Open Tracking
- Opendkim
- Opens
- Openssl
- Opt-In
- Opt-Out
- Optonline
- Oracle
- Outage
- Outages
- Outblaze
- Outlook
- Outlook.com
- Outrage
- Outreach
- Outsource
- Ownership
- Owning the Channel
- P=reject
- Pacer
- Pander
- Panel
- Password
- Patent
- Paypal
- PBL
- Penkava
- Permission
- Personalities
- Personalization
- Personalized
- Pgp
- Phi
- Philosophy
- Phish
- Phishers
- Phishing
- Phising
- Photos
- Pii
- PIPA
- PivotalVeracity
- Pix
- Pluscachange
- Podcast
- Policies
- Policy
- Political Mail
- Political Spam
- Politics
- Porn
- Port25 Blocking
- Postfix
- Postmaster
- Power MTA
- Practices
- Predictions
- Preferences
- Prefetch
- Preview
- Primers
- Privacy
- Privacy Policy
- Privacy Protection
- Private Relay
- Productive Mail
- Promotions
- Promotions Tab
- Proofpoint
- Prospect
- Prospecting
- Protocols
- Proxy
- Psa
- PTR
- Public Suffix List
- Purchased
- Purchased Lists
- Purchases
- Purchasing Lists
- Questions
- Quoted Printable
- Rakuten
- Ralsky
- Rant
- Rate Limiting
- Ray Tomlinson
- Rc4
- RDNS
- Read
- Ready to Post
- Readytopost
- Real People
- Realtime Address Verification
- Recaptcha
- Received
- Receivers
- Recipient
- Recipients
- Redirect
- Redsnapper
- Reference
- Registrar
- Registration
- Rejection
- Rejections
- Rejective
- Relationship
- Relevance
- Relevancy
- Removals
- Render Rate
- Rendering
- Repost
- Repudiation
- Reputation
- Requirements
- Research
- Resources
- Responsive
- Responsive Design
- Responsys
- Retail
- Retired Domains
- Retro
- Return Path
- Return Path Certified
- ReturnPath
- Reunion.com
- Reverse Dns
- Rfc
- RFC2047
- RFC2821/2822
- RFC5321/5322
- RFC5322
- RFC8058
- RFC821/822
- RFCs
- Roadr
- RoadRunner
- Rodney Joffe
- ROKSO
- Role Accounts
- Rollout
- RPost
- RPZ
- Rule 34
- Rules
- Rum
- Rustock
- S.1618
- SaaS
- Sales
- Salesforce
- Sass
- SBCGlobal
- Sbl
- Scam
- Scammers
- Scams
- Scanning
- Scraping
- Screamer
- Screening
- Script
- Sec
- Secure
- Security
- Segmentation
- Selligent
- Send
- Sender
- Sender Score
- Sender Score Certified
- Senderbase
- Senderid
- Senders
- Senderscore
- Sendgrid
- Sending
- Sendy
- Seo
- Service
- Services
- Ses
- Seth Godin
- SFDC
- SFMAAWG2009
- SFMAAWG2010
- SFMAAWG2014
- Shared
- Shell
- Shouting
- Shovel
- Signing
- Signups
- Silly
- Single Opt-In
- Slack
- Slicing
- Smarthost
- Smiley
- Smime
- SMS
- SMTP
- Snds
- Snowshoe
- Soa
- Socia
- Social Media
- Social Networking
- Soft Bounce
- Software
- Sony
- SOPA
- Sorbs
- Spam
- Spam Blocking
- Spam Definition
- Spam Filtering
- Spam Filters
- Spam Folder
- Spam Law
- Spam Laws
- Spam Reports
- Spam Traps
- Spam. IMessage
- Spamarrest
- Spamassassin
- Spamblocking
- Spamcannibal
- Spamcon
- Spamcop
- Spamfiltering
- Spamfilters
- Spamfolder
- Spamhaus
- Spamhause
- Spammer
- Spammers
- Spammest
- Spamming
- Spamneverstops
- Spamresource
- Spamtrap
- Spamtraps
- Spamza
- Sparkpost
- Speaking
- Special Offers
- Spectre
- Spf
- Spoofing
- SproutDNS
- Ssl
- Standards
- Stanford
- Starttls
- Startup
- State Spam Laws
- Statistics
- Storm
- Strategy
- Stunt
- Subject
- Subject Lines
- Subscribe
- Subscriber
- Subscribers
- Subscription
- Subscription Process
- Success Stories
- Suing
- Suppression
- Surbl
- Sureclick
- Suretymail
- Survey
- Swaks
- Syle
- Symantec
- Tabbed Inbox
- Tabs
- Tagged
- Tagging
- Target
- Targeting
- Techincal
- Technical
- Telnet
- Template
- Tempo
- Temporary
- Temporary Failures
- Terminology
- Testing
- Text
- Thanks
- This Is Spam
- Throttling
- Time
- Timely
- TINS
- TLD
- Tlp
- TLS
- TMIE
- Tmobile
- Too Much Mail
- Tool
- Tools
- Toomuchemail
- Tor
- Trademark
- Traffic Light Protocol
- Tragedy of the Commons
- Transactional
- Transition
- Transparency
- Traps
- Travel
- Trend/MAPS
- Trend Micro
- Trend/MAPS
- Trigger
- Triggered
- Troubleshooting
- Trustedsource
- TWSD
- Txt
- Types of Email
- Typo
- Uce
- UCEprotect
- Unblocking
- Uncategorized
- Unexpected Email
- Unicode
- Unroll.me
- Unsolicited
- Unsubcribe
- Unsubscribe
- Unsubscribed
- Unsubscribes
- Unsubscribing
- Unsubscription
- Unwanted
- URIBL
- Url
- Url Shorteners
- Usenet
- User Education
- Utf8
- Valentine's Day
- Validation
- Validity
- Value
- Valueclick
- Verification
- Verizon
- Verizon Media
- VERP
- Verticalresponse
- Vetting
- Via
- Video
- Violence
- Virginia
- Virtumundo
- Virus
- Viruses
- Vmc
- Vocabulary
- Vodafone
- Volume
- Vzbv
- Wanted Mail
- Warmup
- Weasel
- Webinar
- Webmail
- Weekend Effect
- Welcome Emails
- White Space
- Whitelisting
- Whois
- Wiki
- Wildcard
- Wireless
- Wiretapping
- Wisewednesday
- Women of Email
- Woof
- Woot
- Wow
- Wtf
- Wttw in the Wild
- Xbl
- Xfinity
- Xkcd
- Yahoo
- Yahoogle
- Yogurt
- Zoidberg
- Zombie
- Zombies
- Zoominfo
- Zurb
