Recent Posts
Looking forward
- laura
- Apr 21, 2017
I had a number of very good talks with folks at the Email Innovations Summit earlier this week. I’m still digesting it all. It’s clear that getting to the inbox isn’t a solved problem. Around a decade ago I figured that the explosion of complaint feedback loops would make my job obsolete. That more data would mean anyone could manage delivery. That’s not the case for a couple reasons. The biggest is that filters don’t look just at complaints and there aren’t FBLs for all the other factors.
For whatever reason, many companies are still struggling with delivery.
Even more interesting is how changes in filters and inboxes are making it harder to measure delivery. In some ways I feel like we’re losing ground on inbox measurement. Filters changes and will keep changing, both to address emerging threats and to meet the needs and wants of subscribers. Gone are the days where Panels have their problems. Seed lists have their problems. There’s a longer blog post here, but it’s nearly the weekend and I’ve had a long week.
Hope you have something great planned.
Quick Vegas trip review
- laura
- Apr 20, 2017
Made it back from Vegas late last night. It was a great trip, even though I wasn’t officially attending the conference. I did get a chance to see old friends and meet some new people. The Women of Email board had our first in person meeting and we’re working on some exciting things over the next few months. Our mentor program is well underway and we have been placing speakers at various conferences.
I can hardly wait to share some of what we’re doing and our plans as they finally come together. We’ve made a difference even in stealth mode, and I’m so proud of my fellow board members. They’ve done great things already, and they’re only just getting started.
One of the high points of the trip for me was dinner with an amazing bunch of women in the space. Some I’ve known for a while, but many were new faces. It was great.
In two weeks I head to EEC to watch Steve talk about the subscription bombing problem and some of the lessons we’ve learned over the last few months.
The twilight of /8s
- steve
- Apr 20, 2017
A “/8” is a block of 16,777,214 usable IP addresses. That’s a big fraction of the entire IPv4 address space – about 1/224, in fact. Each one is all the addresses that begin with a given number: 10.0.0.0/8 is all the IP addresses that begin with “10.”, “184.0.0.0/8” (or “184/8” for short) is all the IP addresses that begin with “184.” and so on.
How are they used? You can see in this map of the entire IPv4 Internet as of 2006.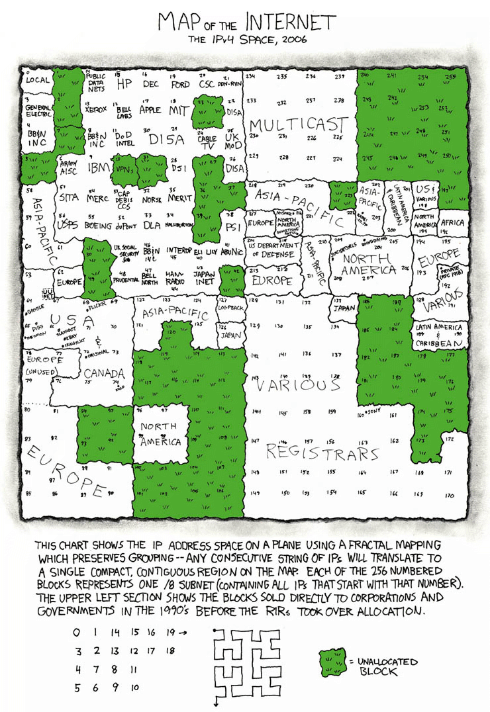
In the early days of the Internet /8s were given out directly to large organizations. If you look near the middle-top of the map, just left of “MULTICAST” and above “DISA” you can see “MIT”.
The Massachusetts Institute of Technology got into the Internet game pretty early. This is the first map I have where they appear, in June 1970: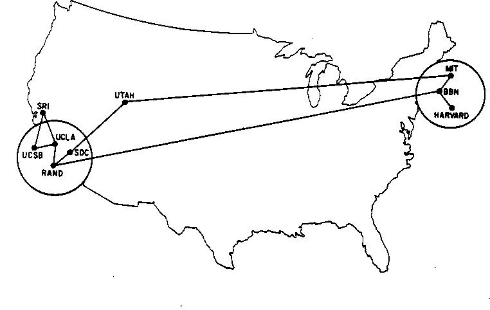
The Laboratory for Computer Science at MIT were assigned the 18.0.0.0/8 block sometime around 1977, according to RFC 739, though it looks like they may have been using it since at least 1976.
By 1983 (RFC 820) it belonged to the whole of MIT, rather just the CS Lab, though you have to wonder how long term that was supposed to be, given the block was named “MIT-TEMP” by 1983 (RFC 870). According to @fanf (who you should follow) it was still described as temporary until at least the 1990s.
But no longer. MIT is upgrading much of their network to IPv6, and they’ve found that fourteen million of their sixteen million addresses haven’t been used, so they’re consolidating their use and selling off eight million of them, half of their /8. Thanks, MIT.
Who else is still sitting on /8s? The military, mostly US, have 13. US Tech companies have 5. Telcos have 4. Ford and Daimler have one each. The US Post Office, Prudential Securities, and Societe Internationale de Telecommunications Aeronautiques each have one too.
One is set aside for use by amateur radio.
And two belong to you.
10.0.0.0/8 is set aside by RFC 1918 for private use, so you can use it – along with 192.168.0.0/16 and 172.160.0.0/12 – on your home network or behind your corporate NAT.
And the whole of 127.0.0.0/8 is set aside for the local address of your computer. You might use 127.0.0.1 most of the time for that, but there are 16,777,213 other addresses you could use instead if you want some variety. Go on, treat yourself, they’re all assigned to you.
A due diligence story
- steve
- Apr 18, 2017
due diligence
noun. research and analysis of a company or organization done in preparation for a business transaction
It’s a term that’s been around for five centuries or so. Originally it meant the effort that was necessary for something, but it evolved into a legal term for “the care that a reasonable person takes to avoid harm to other persons or their property“.
More recently it’s evolved to mean “the research that a company should perform before engaging in a financial transaction“.
One aspect of that is doing at least a bare minimum of research on a customer before you let them take advantage of your reputation.
I just got some SMS spam from a short code, advertising two domains – 29designx.us and customlogocoupon.us. It’s SMS spam, so there’s no hidden content, no affiliate tags, just the bare domains. One spam has both domains in it, the other has 29designx.us twice.
According to the company that operates the SMS gateway this is a dedicated short code, not a shared code. In ESP terms that’s kinda equivalent to a customer on a dedicated IP address rather than one sharing a pool. Except much more so – short codes are a scarcer resource than IP addresses, with the US having fewer short codes in total than some ESPs have IP addresses.
What would 60 seconds of due diligence have told the SMS provider about this customer?
Let’s start by looking at the two websites.
They’re clearly built from the same template. Same annoying animation, same fake sale countdown timers, same live chat window.
The live chat was answered by Harvey (who is a real person, one I managed to annoy by talking with him through multiple live chat windows on their different sites simultaneously). Different ‘phone numbers though – 1-866-212-2217 for the coupon site vs 1-619-942-5964.
Then lets look at whois for the domains:
Domain Name: 29DESIGNX.US
Registrant Name: Mildred Smith
Registrant Organization: 29designs
Registrant Address1: 1854 Valley View Drive (that’s in Kansas)
Registrant City: Boston
Registrant State/Province: MA (not Boston, Massachusetts)
Registrant Postal Code: DN3 6GB (see note)
Registrant Country: UNITED KINGDOM (nor the United Kingdom)
Registrant Country Code: GB
Registrant Phone Number: +92.3233000306 (nor Pakistan)
Registrant Email: rhiannon.desir@gmail.com (gmail? rhiannon != Mildred)
Registrant Application Purpose: P1 (= business registration)
Registrant Nexus Category: C11
and
Domain Name: CUSTOMLOGOCOUPON.US
Registrant Name: Antonio R. Flores
Registrant Organization: Oranges Records & Tapes (see note)
Registrant Address1: 4243 Marie Street Annapolis (doesn’t exist)
Registrant City: MD
Registrant State/Province: MD
Registrant Postal Code: 21401
Registrant Country: United States
Registrant Country Code: US
Registrant Phone Number: +1.4108498868
Registrant Email: mj9729395@gmail.com (seven digit number, huh?)
Registrant Application Purpose: P3 (= personal website)
Registrant Nexus Category: C11
That’d make me suspicious enough to put the customer on hold and maybe doing a little actual investigation of them before allowing them to send. That’s the due diligence an ESP or SMS provider should do.
Laura is in Las Vegas today, so I have a little spare time. Let’s do the next level of investigation to find a little more. Nothing fancy, just some creative use of Google.
“DN3 6GB” is an interesting UK postcode. Not because Doncaster – the South Yorkshire town that “DN3” would imply – is particularly interesting, nor because of the fact that DN3 6GB doesn’t exist, despite being syntactically correct.
No. It’s interesting because it is the first postcode in a test suite for validating UK postcodes via regular expression so it’s all over developers forums and FAQs when people are talking about valid UK postcodes. Not only a fake, but a manually created fake.
“Orange’s Records and Tapes” is interesting too. It’s an odd looking business name to have attached to a logo design company. And the mention of “Tapes” looks rather dated. It seems to be a Chicago-based record store (or, possibly, small chain) that either went out of business or was bought out and the name abandoned quite some years ago. It’s still on some easily available lists of business names, though.
And it’s also in output from fakenamegenerator.com – a handy little site that generates fake names, email addresses, employer names, birth dates, credit card numbers and everything else you might want to have as test data. That makes me pretty sure that everything about customlogocoupon.us is fake.
Reverse whois search suggests that the same “Mildred Smith” also registered 29design.us, paperx.us, 99videos.us, 29designs.us and 99videoz.us. As well as the similarity in domain names, the sites that are up are using the same template as the first two sites and selling services in much the same style. And appear to use equally fake registration data.
We still have the ‘phone numbers published on the original sites…
The 866 number on customlogocoupon.us shows up in the contact information for logoventure.com and logoventure.net. They’re a small graphic design and flash animation company, consisting of Russell Bryant, Jessica Sandler, George Isaacson and Jason somebody. No Antonio R. Flores, and it’s a much more restrained site than the customlogocoupon.us hyperactivity.
The 619 number from 29designx.us shows up on animationsharks.com. Which is a little better designed, but still has the same live chat box manned by Harvey. (Hi, Harvey!). It’s been mentioned elsewhere in the SMS spam context too.
There’s no useful contact information on the site, and the domain registration data is falsified via Domains by Proxy (reasonable for a personal site, a bad sign on a business site).
My best guess is that animationsharks.com / 29designx.us / 29design.us / 29designns.com are the SMS spammers, while logoventure.com are a customer of theirs.
Hidden by CSS on the animationsharks.com site is a list of services, support and postal contact information that’s identical to that of a legitimate corporate animation studio based out of Boston. It’s possible that they just ripped off the site of another company, but it’s also possible it’s a side-job, something done by an ex-employee…
But that’s all I have time to look at now. Back to work.
Malicious email terms defined.
- laura
- Apr 17, 2017
Legitimate mailers need to distinguish themselves from spammers. One important piece of that is knowing what spammers do. SendGrid has put together some information on common scams and techniques spammers use to get email delivered.
Some of these terms, like doxxing and swatting, are not specifically email related. However, they are used against people who are fighting abuse on the Internet. People who are actively investigating darker portions of the internet face real danger. Brian Krebs has made some of the harassment he’s received public. I know other people in the space have been harassed but don’t make it so public.
I think it’s valuable for marketers to understand the malicious and criminal end of mail. It makes some filtering decisions less random when you know the types of bad traffic that the filters are trying to stop. The SendGrid document is a fantastic first stop to learn about them.
Responding to complaints
- laura
- Apr 13, 2017
I sent in a complaint to an ESP earlier today. This was mail from a major UK retailer to an address that is not used to sign up for mail. It’s part of an ongoing stream of spam related to UK services and products. I believe most of this is because one of the data selling companies has that address associated with someone who is not me.
I did explain I believed this was a purchased address but I’m wondering if I will get a response. The address isn’t one of those I regularly use so there isn’t a connection between “Laura, deliverability person” and “Laura, spam victim.” There are some industry folks who go out of their way to respond to my complaints. That’s always rewarding.
On a more theoretical level, I can make good arguments for responding and good arguments for not responding.
Vegas next week
- laura
- Apr 12, 2017
All of you attending the Email Innovations Summit in Vegas, I’ll be around during the conference. Not attending or speaking this year, but I have some meetings with folks scheduled. I will also be around for the session arranged by the Women of Email presents “Rumpelstiltskin Marketers”
Read MoreMore on the botnet arrest in Spain
- laura
- Apr 12, 2017
Yesterday I talked about Peter Yuryevich Levashov being arrested in Spain on a US warrant. That warrant and other accompanying docs are unsealed and available on the DOJ website. The arrest was also mentioned on the Rachel Maddow show last night (video).
There are quite a few people, including Rachel Maddow, speculating that this is somehow related to the Russian interference in the recent US elections. As many have pointed out, Levashov and his botnet were involved in spreading fake news during the 2012 elections in Russia.
I don’t know. There may be some connection, it does appear botnets were involved in some of the fake news events during the past election season. None of the docs presented by the Justice Department mention the election. We know that the DOJ investigates botnets, particularly those doing more than just spread spam. This isn’t the first time they’ve taken action against someone running a botnet. It could just be that they finally knew he was in a country that would act on a US warrant. It could be it was just time.
Or, this botnet could be part of the election investigation. I don’t think we really have enough information to go either way.
Botnet herder / spam kingpin arrested
- laura
- Apr 10, 2017
Via Krebs on Security, a russian named Pyotr Levashov has been arrested in Spain. According to news reports (NY Times, Reuters) the arrest happened in response to a warrant issued by the US, but no details were given as to what he was being charged with. The DoJ says the case is currently under seal and will not comment on charges.
There is widespread agreement that this person is involved in major spamming operations. He’s one of Spamhaus’ Top 10 spammers (ROKSO listing). He’s been implicated in fraud during the 2012 elections in Russia. Some reports are speculating that he was involved in the hacking of the 2016 elections here in the US, but there’s no current evidence that’s true.
March 2017: The Month in Email
- laura
- Apr 7, 2017
It’s that time again… here’s a look at our last month of blog posts. We find it useful to recap each month, both to track trends and issues in email delivery and to provide a handy summary for those who aren’t following along breathlessly every single day. Let us know if you find it useful too!
As always, I wrote about email filters. It’s so important to recognize that filters aren’t arbitrary — they’re detailed instructions that help meet specific user needs, and the more you are cognizant of that, the better you’ll be able to work with them. Additionally, filters aren’t perfect and likely never will be. False positives and false negatives are frustrating, but as long as spam is still a viable business for spammers, they’ll continue to figure out how to work around filters. As such, we can’t expect filters to be 100% accurate in determining what constitutes wanted and unwanted mail.
Part of this, of course, is due to the problem of fraudulent signups. Companies aren’t particularly vigilant about address acquisition and hygiene, and as a result, they’ll claim you “signed up” for their email when you did not. Some people believe that a confirmed opt-in (COI) will solve this problem, but our experience is companies are reluctant to leave revenue on the table, and that they will continue to mail to addresses that have not confirmed.
Address sharing and co-reg is also part of the problem. As we saw in the extensive RCM data breach, many major brands continue to work with third-party senders to send mail in ways that are quite clearly spam. And in more criminal activity, I looked at the rise of botnets and how some of those criminals were brought to justice. In other justice news, there’s been an indictment in the Yahoo breach and another CASL enforcement action.
I wrote a post about bounce handling and “relaying denied” error messages, which are quite rare. It’s useful to have an understanding of these and other error messages, since bounces are sometimes indicative of a larger technical issue, such as when AOL accidentally bounced all messages for a short period last week. Speaking of AOL, we noted that there’s no official timeline for the move from Verizon addresses to AOL addresses following the 2015 acquisition, but it may be worth considering asking your customers to update their addresses.
Spam and filters aren’t the only factors of course. It can be challenging to figure out the multiple factors that make up the black box of delivery. And of course, the most important part of delivery continues to be engagement, engagement, engagement.
I wrote a few posts this month on why I do what I do, and why it’s so important to me. First, I wrote about A Day Without A Woman, and my choice not to participate in offering advice and guidance for that day. The truth is that I enjoy sharing what I know and helping people solve problems. I was honored to be named one of 11 Innovators in Email, and I know that my volunteer work in the industry and my unpaid blogging work is a big part of that. It may sound corny, but I really do believe we are on the front lines of the fight of good vs. evil online, and despite the distractions of politics and world events, we must all continue to do our part.
Categories
Tags
- 2010
- 2016
- 2fa
- 419
- 4xx
- 554
- 5xx
- @
- Aarp
- Abacus
- Abandoned
- Aboutmyemail
- Abuse
- Abuse Desk
- Abuse Enforcement
- Abuse Prevention
- Academia
- Accreditation
- Acme
- Acquisition
- Address Book
- Addresses
- Administrivia
- Adsp
- Advanced Delivery
- Advertiser
- Advertising
- Advice
- Affiliate
- Affiliates
- After the Email
- Alerts
- Algorithm
- Alice
- Alignment
- Allcaps
- Alt Text
- AMA
- Amazon
- Amp
- Amsterdam
- Analysis
- Anecdotes
- Anti-Spam
- Anti-Spam Laws
- Anti-Spammers
- Antwort
- AOL
- Appeals
- Appearances
- Appending
- Apple
- Arc
- Arf
- Arrest
- Arrests
- Ascii
- Asides
- Ask Laura
- Askwttw
- Assertion
- Assumptions
- ATT
- Attacks
- Attention
- Attrition
- Audit
- Authentication
- Authentication. BT
- Autonomous
- Award
- B2B
- B2C
- Backhoe
- Backscatter
- Backus-Naur Form
- Banks
- Barracuda
- Barry
- Base64
- Base85
- Bcc
- Bcp
- Bear
- Bears
- Behaviour
- Benchmark
- BESS
- Best Practices
- Bgp
- BIMI
- Bit Rot
- Bitly
- Bizanga
- Black Friday
- Blackfriday
- Blacklist
- Blacklists
- Blast
- Blo
- Block
- Blockin
- Blocking
- Blocklist
- Blocklisting
- Blocklists
- Blocks
- Blog
- Blog Links
- Blogroll
- Blogs
- Bob
- Boca
- Bofa
- Book Review
- Bot
- Botnet
- Botnets
- Bots
- Bounce
- Bounce Handling
- Bounces
- Branding
- Brands
- Breach
- Breaches
- Breech
- Bronto
- Browser
- Bsi
- Bucket
- Bulk
- Bulk Folder
- Bulk Mail
- Business
- Business Filters
- Buying Leads
- Buying Lists
- C-28
- CA
- Caa
- Cabbage
- Cache
- Cadence
- CAH
- California
- Campaign
- CAN SPAM
- Canada
- Candy
- Candycandycandy
- Canonicalization
- Canspam
- Captcha
- Career Developmnent
- Careers at WttW
- Cargo Cult
- Case Law
- Cases
- CASL
- Cat
- Cbl
- CDA
- Cert
- Certification
- CFL
- CFWS
- Change
- Charter
- Cheat
- Cheese
- Choicepoint
- Choochoo
- Christmas
- Chrome
- Cidr
- Cisco
- Civil
- Clear.net
- Clearwire.net
- Cli
- Click
- Click Through
- Click Tracking
- Clicks
- Clickthrough
- Client
- Cloudflare
- Cloudmark
- Cname
- Co-Reg
- Co-Registration
- Cocktail
- Code
- COI
- Comcast
- Comments
- Commercial
- Communication
- Community
- Comodo
- Comparison
- Competitor
- Complaint
- Complaint Rates
- Complaints
- Compliancce
- Compliance
- Compromise
- Conference
- Conferences
- Confirmation
- Confirmed (Double) Opt-In
- Confirmed Opt-In
- Congress
- Consent
- Conservatives
- Consistency
- Constant Contact
- Consultants
- Consulting
- Content
- Content Filters
- Contracts
- Cookie
- Cookie Monster
- COPL
- Corporate
- Cost
- Court Ruling
- Cox
- Cox.net
- Cpanel
- Crib
- Crime
- CRM
- Crowdsource
- Crtc
- Cryptography
- CSRIC
- CSS
- Curl
- Customer
- Cyber Monday
- Czar
- Data
- Data Hygiene
- Data Security
- Data Segmentation
- Data Verification
- DBL
- Dbp
- Ddos
- Dea
- Dead Addresses
- Dedicated
- Dedicated IPs
- Defamation
- Deferral
- Definitions
- Delays
- Delisting
- Deliverability
- Deliverability Experts
- Deliverability Improvement
- Deliverability Summit
- Deliverability Week
- Deliverability Week 2024
- Deliverabiltiy
- DeliverabiltyWeek
- Delivery Blog Carnival
- Delivery Discussion
- Delivery Emergency
- Delivery Experts
- Delivery Improvement
- Delivery Lore
- Delivery News
- Delivery Problems
- Dell
- Design
- Desks
- Dhs
- Diagnosis
- Diff
- Dig
- Direct Mag
- Direct Mail
- Directives
- Discounts
- Discovery
- Discussion Question
- Disposable
- Dk
- DKIM
- Dkimcore
- DMA
- DMARC
- DNS
- Dnsbl
- Dnssec
- Docs
- Doingitright
- Domain
- Domain Keys
- Domain Reputation
- DomainKeys
- Domains
- Domains by Proxy
- Dontpanic
- Dot Stuffing
- Dotcom
- Double Opt-In
- Dublin
- Dyn
- Dynamic Email
- E360
- Earthlink
- Ec2
- Ecoa
- Economics
- ECPA
- Edatasource
- Edns0
- Eec
- Efail
- Efax
- Eff
- Election
- Email Address
- Email Addresses
- Email Change of Address
- Email Client
- Email Design
- Email Formats
- Email Marketing
- Email Strategy
- Email Verification
- Emailappenders
- Emailgeeks
- Emails
- Emailstuff
- Emoji
- Emoticon
- Encert
- Encryption
- End User
- Endusers
- Enforcement
- Engagement
- Enhanced Status Code
- Ennui
- Entrust
- Eol
- EOP
- Epsilon
- Esp
- ESPC
- ESPs
- EU
- Ev Ssl
- Evaluating
- Events
- EWL
- Exchange
- Excite
- Expectations
- Experience
- Expires
- Expiring
- False Positives
- FAQ
- Fathers Day
- Fbl
- FBL Microsoft
- FBLs
- Fbox
- FCC
- Fcrdns
- Featured
- Fedex
- Feds
- Feedback
- Feedback Loop
- Feedback Loops
- Fiction
- Filter
- Filter Evasion
- Filtering
- Filterings
- Filters
- Fingerprinting
- Firefox3
- First Amendment
- FISA
- Flag Day
- Forensics
- Format
- Formatting
- Forms
- Forwarding
- Fraud
- Freddy
- Frequency
- Friday
- Friday Spam
- Friendly From
- From
- From Address
- FTC
- Fussp
- Gabbard
- GDPR
- Geoip
- Gevalia
- Gfi
- Git
- Giveaway
- Giving Up
- Global Delivery
- Glossary
- Glyph
- Gmail
- Gmails
- Go
- Godaddy
- Godzilla
- Good Email Practices
- Good Emails in the Wild
- Goodmail
- Google Buzz
- Google Postmaster Tools
- Graphic
- GreenArrow
- Greylisting
- Greymail
- Groupon
- GT&U
- Guarantee
- Guest Post
- Guide
- Habeas
- Hack
- Hacking
- Hacks
- Hall of Shame
- Harassment
- Hard Bounce
- Harvesting
- Harvey
- Hash
- Hashbusters
- Headers
- Heartbleed
- Hearts
- HELO
- Help
- Henet
- Highspeedinternet
- Hijack
- History
- Holiday
- Holidays
- Holomaxx
- Hostdns4u
- Hostile
- Hostname
- Hotmail
- How To
- Howto
- Hrc
- Hsts
- HTML
- HTML Email
- Http
- Huey
- Humanity
- Humor
- Humour
- Hygiene
- Hypertouch
- I18n
- ICANN
- Icloud
- IContact
- Identity
- Idiots
- Idn
- Ietf
- Image Blocking
- Images
- Imap
- Inbox
- Inbox Delivery
- Inboxing
- Index
- India
- Indiegogo
- Industry
- Infection
- Infographic
- Information
- Inky
- Inline
- Innovation
- Insight2015
- Integration
- Internationalization
- Internet
- Intuit
- IP
- IP Address
- Ip Addresses
- IP Repuation
- IP Reputation
- IPhone
- IPO
- IPv4
- IPv6
- Ironport
- Ironport Cisco
- ISIPP
- ISP
- ISPs
- J.D. Falk Award
- Jail
- Jaynes
- JD
- Jobs
- Json
- Junk
- Juno/Netzero/UOL
- Key Rotation
- Keybase
- Keynote
- Kickstarter
- Kraft
- Laposte
- Lavabit
- Law
- Laws
- Lawsuit
- Lawsuits
- Lawyer
- Layout
- Lead Gen
- Leak
- Leaking
- Leaks
- Legal
- Legality
- Legitimate Email Marketer
- Letsencrypt
- Letstalk
- Linked In
- Links
- List Hygiene
- List Management
- List Purchases
- List the World
- List Usage
- List-Unsubscribe
- Listing
- Listmus
- Lists
- Litmus
- Live
- Livingsocial
- London
- Lookup
- Lorem Ipsum
- Lycos
- Lyris
- M3AAWG
- Maawg
- MAAWG2007
- Maawg2008
- MAAWG2012
- MAAWGSF
- Machine Learning
- Magill
- Magilla
- Mail Chimp
- Mail Client
- MAIL FROM
- Mail Privacy Protection
- Mail Problems
- Mail.app
- Mail.ru
- Mailboxes
- Mailchimp
- Mailgun
- Mailing Lists
- Mailman
- Mailop
- Mainsleaze
- Maitai
- Malicious
- Malicious Mail
- Malware
- Mandrill
- Maps
- Marketer
- Marketers
- Marketing
- Marketo
- Markters
- Maths
- Mcafee
- Mccain
- Me@privacy.net
- Measurements
- Media
- Meh
- Meltdown
- Meme
- Mentor
- Merry
- Message-ID
- Messagelabs
- MessageSystems
- Meta
- Metric
- Metrics
- Micdrop
- Microsoft
- Milter
- Mime
- Minimal
- Minshare
- Minute
- Mit
- Mitm
- Mobile
- Models
- Monitoring
- Monkey
- Monthly Review
- Mpp
- MSN/Hotmail
- MSN/Hotmail
- MTA
- Mua
- Mutt
- Mx
- Myths
- Myvzw
- Needs Work
- Netcat
- Netsol
- Netsuite
- Network
- Networking
- New Year
- News
- News Articles
- Nhi
- NJABL
- Now Hiring
- NTP
- Nxdomain
- Oath
- Obituary
- Office 365
- Office365
- One-Click
- Only Influencers
- Oops
- Opaque Cookie
- Open
- Open Detection
- Open Rate
- Open Rates
- Open Relay
- Open Tracking
- Opendkim
- Opens
- Openssl
- Opt-In
- Opt-Out
- Optonline
- Oracle
- Outage
- Outages
- Outblaze
- Outlook
- Outlook.com
- Outrage
- Outreach
- Outsource
- Ownership
- Owning the Channel
- P=reject
- Pacer
- Pander
- Panel
- Password
- Patent
- Paypal
- PBL
- Penkava
- Permission
- Personalities
- Personalization
- Personalized
- Pgp
- Phi
- Philosophy
- Phish
- Phishers
- Phishing
- Phising
- Photos
- Pii
- PIPA
- PivotalVeracity
- Pix
- Pluscachange
- Podcast
- Policies
- Policy
- Political Mail
- Political Spam
- Politics
- Porn
- Port25 Blocking
- Postfix
- Postmaster
- Power MTA
- Practices
- Predictions
- Preferences
- Prefetch
- Preview
- Primers
- Privacy
- Privacy Policy
- Privacy Protection
- Private Relay
- Productive Mail
- Promotions
- Promotions Tab
- Proofpoint
- Prospect
- Prospecting
- Protocols
- Proxy
- Psa
- PTR
- Public Suffix List
- Purchased
- Purchased Lists
- Purchases
- Purchasing Lists
- Questions
- Quoted Printable
- Rakuten
- Ralsky
- Rant
- Rate Limiting
- Ray Tomlinson
- Rc4
- RDNS
- Re-Engagement
- Read
- Ready to Post
- Readytopost
- Real People
- Realtime Address Verification
- Recaptcha
- Received
- Receivers
- Recipient
- Recipients
- Redirect
- Redsnapper
- Reference
- Registrar
- Registration
- Rejection
- Rejections
- Rejective
- Relationship
- Relevance
- Relevancy
- Removals
- Render Rate
- Rendering
- Replay
- Repost
- Repudiation
- Reputation
- Requirements
- Research
- Resources
- Responsive
- Responsive Design
- Responsys
- Retail
- Retired Domains
- Retro
- Return Path
- Return Path Certified
- ReturnPath
- Reunion.com
- Reverse Dns
- RFC
- RFC2047
- RFC2821/2822
- RFC5321/5322
- RFC5322
- RFC8058
- RFC821/822
- RFCs
- Roadr
- RoadRunner
- Rodney Joffe
- ROKSO
- Role Accounts
- Rollout
- RPost
- RPZ
- Rule 34
- Rules
- Rum
- Rustock
- S.1618
- SaaS
- Sales
- Salesforce
- Sass
- SBCGlobal
- Sbl
- Scam
- Scammers
- Scams
- Scanning
- Scraping
- Screamer
- Screening
- Script
- Sec
- Secure
- Security
- Segmentation
- Selligent
- Send
- Sender
- Sender Score
- Sender Score Certified
- Senderbase
- Senderid
- Senders
- Senderscore
- Sendgrid
- Sending
- Sendy
- Seo
- Service
- Services
- Ses
- Seth Godin
- SFDC
- SFMAAWG2009
- SFMAAWG2010
- SFMAAWG2014
- Shared
- Shell
- Shouting
- Shovel
- Signing
- Signups
- Silly
- Single Opt-In
- Slack
- Slicing
- Smarthost
- Smiley
- Smime
- SMS
- SMTP
- Snds
- Snowshoe
- Soa
- Socia
- Social Media
- Social Networking
- Soft Bounce
- Software
- Sony
- SOPA
- Sorbs
- Spam
- Spam Blocking
- Spam Definition
- Spam Filtering
- Spam Filters
- Spam Folder
- Spam Law
- Spam Laws
- Spam Reports
- Spam Traps
- Spam. IMessage
- Spamarrest
- Spamassassin
- Spamblocking
- Spamcannibal
- Spamcon
- Spamcop
- Spamfiltering
- Spamfilters
- Spamfolder
- Spamhaus
- Spamhause
- Spammer
- Spammers
- Spammest
- Spamming
- Spamneverstops
- Spamresource
- Spamtrap
- Spamtraps
- Spamza
- Sparkpost
- Speaking
- Special Offers
- Spectre
- SPF
- Spoofing
- SproutDNS
- Ssl
- Standards
- Stanford
- Starttls
- Startup
- State Spam Laws
- Statistics
- Storm
- Strategy
- Stunt
- Subject
- Subject Lines
- Subscribe
- Subscriber
- Subscribers
- Subscription
- Subscription Process
- Success Stories
- Suing
- Suppression
- Surbl
- Sureclick
- Suretymail
- Survey
- Swaks
- Syle
- Symantec
- Tabbed Inbox
- Tabs
- Tagged
- Tagging
- Target
- Targeting
- Techincal
- Technical
- Telnet
- Template
- Tempo
- Temporary
- Temporary Failures
- Terminology
- Testing
- Text
- Thanks
- This Is Spam
- Throttling
- Time
- Timely
- TINS
- TLD
- Tlp
- TLS
- TMIE
- Tmobile
- Too Much Mail
- Tool
- Tools
- Toomuchemail
- Tor
- Trademark
- Traffic Light Protocol
- Tragedy of the Commons
- Transactional
- Transition
- Transparency
- Traps
- Travel
- Trend/MAPS
- Trend Micro
- Trend/MAPS
- Trigger
- Triggered
- Troubleshooting
- Trustedsource
- TWSD
- Txt
- Types of Email
- Typo
- Uce
- UCEprotect
- Unblocking
- Uncategorized
- Undisclosed Recipients
- Unexpected Email
- Unicode
- Unroll.me
- Unsolicited
- Unsubcribe
- Unsubscribe
- Unsubscribed
- Unsubscribes
- Unsubscribing
- Unsubscription
- Unwanted
- URIBL
- Url
- Url Shorteners
- Usenet
- User Education
- Utf8
- Valentine's Day
- Validation
- Validity
- Value
- Valueclick
- Verification
- Verizon
- Verizon Media
- VERP
- Verticalresponse
- Vetting
- Via
- Video
- Violence
- Virginia
- Virtumundo
- Virus
- Viruses
- Vmc
- Vocabulary
- Vodafone
- Volume
- Vzbv
- Wanted Mail
- Warmup
- Weasel
- Webinar
- Webmail
- Weekend Effect
- Welcome Emails
- White Space
- Whitelisting
- Whois
- Wiki
- Wildcard
- Wireless
- Wiretapping
- Wisewednesday
- Women of Email
- Woof
- Woot
- Wow
- Wtf
- Wttw in the Wild
- Xbl
- Xfinity
- Xkcd
- Yahoo
- Yahoogle
- Yogurt
- Zoidberg
- Zombie
- Zombies
- Zoominfo
- Zurb