Recent Posts
Anatomy of a successful phishing attempt
Earlier this year the Exploratorium was the victim of a phishing attack. They’ve posted an article on what happened and how they discovered and dealt with the issue.
But they didn’t just report on the attack, they dissected it. And, as is appropriate for a organization with a mission of education, they mapped out what they discovered during the investigation.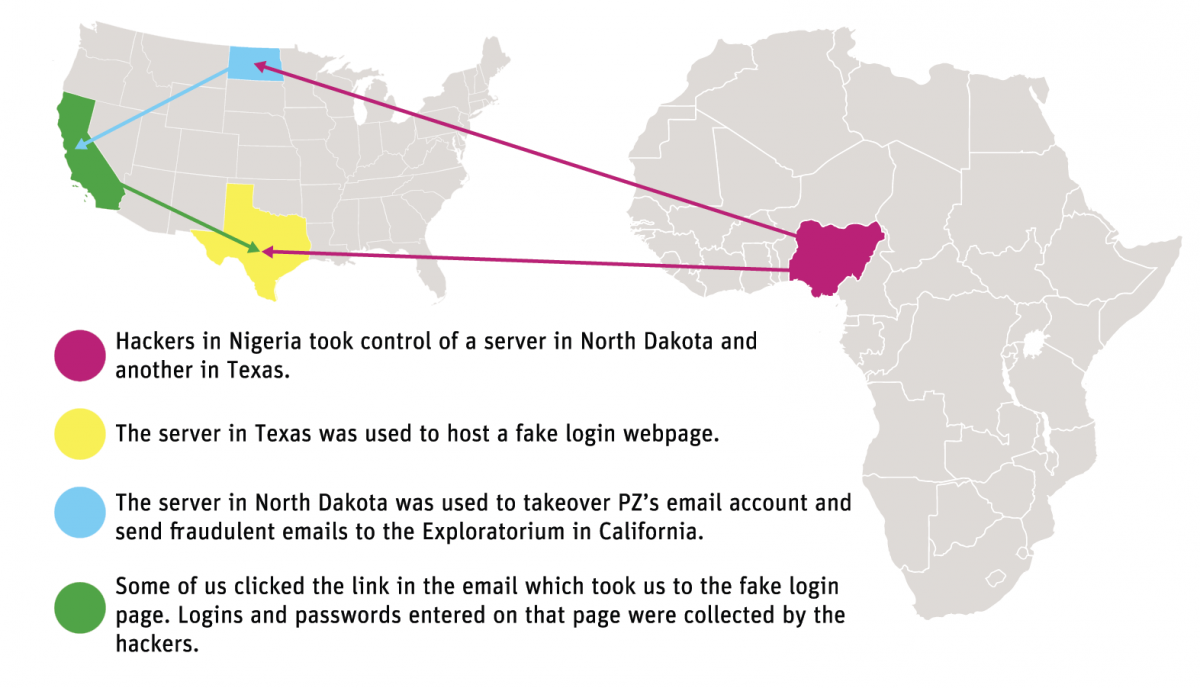
There are a couple of things that stand out to me about this attack. One is that of the more interesting pieces to me is that there was a delay between the compromise and the start of the attack. The Exploratorium calls it “the pivot” and describes it as the hacker deciding what to do next. The second is that the phisher actively interacted with the victim’s account. All new mail was sent to the trash automatically so she wouldn’t see incoming mail. Some mail was actively replied to so more people would click on the message. The phisher took steps to retain access to the account for as long as possible.
One thing that the Exploratorium didn’t see was any actual access to Exploratorium files or information. That may be because the Exploratorium itself wasn’t the target. Once a phisher / hacker has access to the email account, they have access to almost everything in your online life: calendars, bank accounts, credit accounts, the list goes on. Email addresses are our online identity and getting access to the address can open access to so much more.
Quite frankly it can happen to any of us. Earlier this week we received a phishing message that looked very plausible. It came from a law firm, mentioned a subpoena and even had an attachment personalized to our company. The attachment wasn’t opened so we were fine, but I can see how that kind of email might trick someone into getting infected.
We all need to be careful online. Email is a wonderful thing, but it’s insecure. It’s a great way for criminals to get into our space and wreck havoc on our computers and our lives.
2016 J.D. Falk Award
André Leduc received the 2016 J.D. Falk award this week at the Paris meeting of M3AAWG. He was recognized for spearheading two distinct projects.
The first was the Operation Safety Net – Best Practices to Address Online, Mobile, and Telephony Threats This 76 page report was written by global security experts. One of the major goals of the report was to discuss security in language accessible to policy makers and management. The report, newly updated in 2015, is available at the M3AAWG website. Making technical language accessible is, to my mind, one of the most important parts of getting security recommendations implemented.
In addition to his work in making security recommendations accessible, André was the lead architect behind the Canadian Anti-Spam Legislation. This legislation has greatly reduced the amount of spam received by Canadians. According to Leduc, CASL has improved permission practices by senders outside of Canada.
Congratulations to André.
And… we're back from London
The Email Innovations Summit in London was a good conference. Much smaller than Vegas, but with a number of very interesting talks. I got to meet a number of folks I’ve only known online and we had some interesting conversations at the conference and at the pub-track in the evenings.
I had so many grand plans for doing some work while in London. So many plans. And then I actually mostly disconnected and ignored anything I “should” be doing. Instead, Steve and I did some touristing, some relaxing, some family time and some connecting with his college friends. We also (over)heard a lot of conversations about the US Election. One night at dinner every table around us was talking about our candidates and what they thought of them. It’s always interesting to hear what non-Americans think about our country.
In addition to missing two debates, it seems we missed some online news, too. I think the biggest thing was another large DDoS attack against that took out many major websites. I’m starting to see some comments that spam levels were down during the attack, too, but haven’t dug into that yet.
I did have an article published in the Only Influencers newsletter last week: Marketers Can’t Learn from Spam. All too often marketers think spammers are better at unboxing because they see spam in their inbox. But spammers are just more criminal and spend a lot of effort trying to bypass filters. These aren’t lessons marketers can learn from.
Unfortunately, due to our London trip, we are going to miss M3AAWG in Paris, which starts today. Two weeks between conferences was exactly the wrong time for going to both. Never fear, many folks will be tweeting what they can using #m3aawg38.
We’re both slowly getting back into the swing (and timezone!) of back to work. Blogging will pick up over the next few days. And I have new castle pictures to share.
Yahoo disabled forwarding
Al posted about this over on his blog earlier this week. Yahoo has disabled the ability to forward email from one Yahoo account to an email account on a different system.
There is, of course, all sorts of speculation as to why forwarding has been disabled including speculation this has to do with holding on to accounts during the Verizon purchase. It’s certainly possible this is the case.
However, forwarding email is hard. Forwarding email on a large scale can result in spam blocks and delivery problems. It’s such an issue M3AAWG published a forwarding best practices document. It’s possible that Yahoo is making some changes on the back end to better implement the best practice recommendations. I don’t know, but it’s possible that Yahoo is telling the truth that they’re improving technology.
Email Innovations Summit next week
I’m headed to London this weekend to speak at the Email Innovations summit next Thursday. It will be an updated version of “How to Talk Tech for Marketers” that I debuted in Vegas earlier this year.
Expect blogging to be light for the next 2 weeks while I’m gone. There are a few things I have to post, but I’m going to try and unplug and for part of the time I’m out of town.
September 2016: The month in email
Happy October, everyone. As we prepare to head to London for the Email Innovations Summit, we’re taking a look back at our busy September. As always, we welcome your feedback, questions, and amusing anecdotes. Seriously, we could use some amusing anecdotes. Or cat pictures.

We continued to discuss the ongoing abuse and the larger issues raised by attacks across the larger internet infrastructure. It’s important to note that even when these attacks aren’t specifically targeting email senders, security issues affect all of us. It’s important for email marketers to understand that increased attacks do affect how customers view the email channel, and senders must take extra care to avoid the appearance of spam, phishing, or other fraudulent activity. I summarized some of the subscription form abuse issues that we’re seeing across the web, and noted responses from Spamhaus and others involved in fighting this abuse. We’re working closely with ESPs and policy groups to continue to document, analyze and strategize best practices to provide industry-wide responses to these attacks.
I was pleased to note that Google is stepping up with a new program, Project Shield, to help journalists and others who are being targeted by these attacks by providing hosting and DDoS protections.
I’m also delighted to see some significant improvements in email client interactions and user experiences. I wrote a bit about some of those here, and I added my thoughts to Al’s discussion of a new user interaction around unsubscribing in the iOS 10 mail client, and I’ll be curious to see how this plays out across other mail clients.
For our best practices coverage, Steve wrote about global suppression lists, and the ways these are used properly and improperly to prevent mail to certain addresses. I wrote about using the proper pathways and workflows to report abuse and get help with problems. I also wrote about the ways in which incentivizing address collection leads to fraud. This is something we really need to take seriously — the problem is more significant than some bad addresses cluttering up your lists. It contributes to the larger landscape of fraud and abuse online, and we need to figure out better ways to build sustainable email programs.
Is there such a thing as a perfect email? I revisited a post from 2011 and noted, as always, that a perfect email is less about technology and more about making sure that the communication is wanted and expected by the recipient. I know I sound like a broken record on this point (or whatever the 21st century equivalent metaphor of a broken record is….) but it’s something that bears repeating as marketers continue to evolve email programs.
We had a bit of a discussion about how senders try to negotiate anti-spam policies with their ESPs. Is this something you’ve experienced, either as a sender or an ESP?
In Ask Laura, I covered shared IP addresses and tagged email addresses, questions I get fairly frequently from marketers as they enhance their lists and manage their email infrastructures. As always, we welcome your questions on all things email delivery related.
Yahoo collaborating with US intelligence agencies
Today it was revealed that Yahoo has been scanning people’s email for the federal government.
Read MoreAffiliates can be liable for fraud
An article popped up on LinkedIn about a recent 2nd court of appeals ruling that I thought was interesting.
Back in 2011, the FTC and the state of Connecticut filed suit against a company called LeanSpa and their affiliate marketer called LeadClick. LeanSpa sold various diet products through negative option marketing. LeadClick was the affiliate company they used to help drive traffic and customers to their websites.
LeadClick and their parent company was included in the suit because the FTC alleged that they were aware of and facilitated the false claims made by their affiliates. The case went to court and LeadClick lost. They appealed to the 2nd Circuit court. Last week the 2nd Circuit Court upheld the trial court’s finding of liability for LeadClick.
In its press release for the case, the FTC says:
Vague reports of Yahoo problems
A number of people, on different forums, have been asking if anyone is seeing a higher bounce rate than usual with Yahoo. Not sure exactly what’s going on here. As I understand it, folks are talking with Yahoo about it. If I hear anything more, I’ll share.
For now, though, if you’re seeing a small increase in Yahoo bounces (or other weirdnesses) others are seeing something odd, too.
Categories
Tags
- 2010
- 2016
- 2fa
- 419
- 4xx
- 554
- 5xx
- @
- Aarp
- Abacus
- Abandoned
- Aboutmyemail
- Abuse
- Abuse Desk
- Abuse Enforcement
- Abuse Prevention
- Academia
- Accreditation
- Acme
- Acquisition
- Address Book
- Addresses
- Administrivia
- Adsp
- Advanced Delivery
- Advertiser
- Advertising
- Advice
- Affiliate
- Affiliates
- After the Email
- Alerts
- Algorithm
- Alice
- Alignment
- Allcaps
- Alt Text
- AMA
- Amazon
- Amp
- Amsterdam
- Analysis
- Anecdotes
- Anti-Spam
- Anti-Spam Laws
- Anti-Spammers
- Antwort
- AOL
- Appeals
- Appearances
- Appending
- Apple
- Arc
- Arf
- Arrest
- Arrests
- Ascii
- Asides
- Ask Laura
- Askwttw
- Assertion
- Assumptions
- ATT
- Attacks
- Attention
- Attrition
- Audit
- Authentication
- Authentication. BT
- Autonomous
- Award
- B2B
- B2C
- Backhoe
- Backscatter
- Banks
- Barracuda
- Barry
- Base64
- Base85
- Bcp
- Bear
- Bears
- Behaviour
- Benchmark
- BESS
- Best Practices
- Bgp
- Bimi
- Bit Rot
- Bitly
- Bizanga
- Black Friday
- Blackfriday
- Blacklist
- Blacklists
- Blast
- Blo
- Block
- Blockin
- Blocking
- Blocklist
- Blocklisting
- Blocklists
- Blocks
- Blog
- Blog Links
- Blogroll
- Blogs
- Bob
- Boca
- Bofa
- Book Review
- Bot
- Botnet
- Botnets
- Bots
- Bounce
- Bounce Handling
- Bounces
- Branding
- Brands
- Breach
- Breaches
- Breech
- Bronto
- Browser
- Bsi
- Bucket
- Bulk
- Bulk Folder
- Bulk Mail
- Business
- Business Filters
- Buying Leads
- Buying Lists
- C-28
- CA
- Caa
- Cache
- Cadence
- CAH
- California
- Campaign
- CAN SPAM
- Canada
- Candy
- Candycandycandy
- Canonicalization
- Canspam
- Captcha
- Career Developmnent
- Careers at WttW
- Cargo Cult
- Case Law
- Cases
- CASL
- Cat
- Cbl
- CDA
- Cert
- Certification
- CFL
- Change
- Charter
- Cheat
- Cheese
- Choicepoint
- Choochoo
- Christmas
- Chrome
- Cidr
- Cisco
- Civil
- Clear.net
- Clearwire.net
- Cli
- Click
- Click Through
- Click Tracking
- Clicks
- Clickthrough
- Client
- Cloudflare
- Cloudmark
- Cname
- Co-Reg
- Co-Registration
- Cocktail
- Code
- COI
- Comcast
- Comments
- Commercial
- Communication
- Community
- Comodo
- Comparison
- Competitor
- Complaint
- Complaint Rates
- Complaints
- Compliancce
- Compliance
- Compromise
- Conference
- Conferences
- Confirmation
- Confirmed (Double) Opt-In
- Confirmed Opt-In
- Congress
- Consent
- Conservatives
- Consistency
- Constant Contact
- Consultants
- Consulting
- Content
- Content Filters
- Contracts
- Cookie
- Cookie Monster
- COPL
- Corporate
- Cost
- Court Ruling
- Cox
- Cox.net
- Cpanel
- Crib
- Crime
- CRM
- Crowdsource
- Crtc
- Cryptography
- CS&M
- CSRIC
- CSS
- Curl
- Customer
- Cyber Monday
- Czar
- Data
- Data Hygiene
- Data Security
- Data Segmentation
- Data Verification
- DBL
- Dbp
- Ddos
- Dea
- Dead Addresses
- Dedicated
- Dedicated IPs
- Defamation
- Deferral
- Definitions
- Delays
- Delisting
- Deliverability
- Deliverability Experts
- Deliverability Improvement
- Deliverability Summit
- Deliverability Week
- Deliverability Week 2024
- Deliverabiltiy
- DeliverabiltyWeek
- Delivery Blog Carnival
- Delivery Discussion
- Delivery Emergency
- Delivery Experts
- Delivery Improvement
- Delivery Lore
- Delivery News
- Delivery Problems
- Dell
- Design
- Desks
- Dhs
- Diagnosis
- Diff
- Dig
- Direct Mag
- Direct Mail
- Directives
- Discounts
- Discovery
- Discussion Question
- Disposable
- Dk
- DKIM
- Dkimcore
- DMA
- Dmarc
- Dns
- Dnsbl
- Dnssec
- Docs
- Doingitright
- Domain
- Domain Keys
- Domain Reputation
- DomainKeys
- Domains
- Domains by Proxy
- Dontpanic
- Dot Stuffing
- Dotcom
- Double Opt-In
- Dublin
- Dyn
- Dynamic Email
- E360
- Earthlink
- Ec2
- Ecoa
- Economics
- ECPA
- Edatasource
- Edns0
- Eec
- Efail
- Efax
- Eff
- Election
- Email Address
- Email Addresses
- Email Change of Address
- Email Client
- Email Design
- Email Formats
- Email Marketing
- Email Verification
- Emailappenders
- Emailgeeks
- Emails
- Emailstuff
- Emoji
- Emoticon
- Encert
- Encryption
- End User
- Endusers
- Enforcement
- Engagement
- Enhanced Status Code
- Ennui
- Entrust
- Eol
- EOP
- Epsilon
- Esp
- ESPC
- ESPs
- EU
- Ev Ssl
- Evaluating
- Events
- EWL
- Exchange
- Excite
- Expectations
- Experience
- Expires
- Expiring
- False Positives
- FAQ
- Fathers Day
- Fbl
- FBL Microsoft
- FBLs
- Fbox
- FCC
- Fcrdns
- Featured
- Fedex
- Feds
- Feedback
- Feedback Loop
- Feedback Loops
- Fiction
- Filter
- Filter Evasion
- Filtering
- Filterings
- Filters
- Fingerprinting
- Firefox3
- First Amendment
- FISA
- Flag Day
- Forensics
- Format
- Formatting
- Forms
- Forwarding
- Fraud
- Freddy
- Frequency
- Friday
- Friday Spam
- Friendly From
- From
- From Address
- FTC
- Fussp
- Gabbard
- Gdpr
- Geoip
- Gevalia
- Gfi
- Git
- Giveaway
- Giving Up
- Global Delivery
- Glossary
- Glyph
- Gmail
- Gmails
- Go
- Godaddy
- Godzilla
- Good Email Practices
- Good Emails in the Wild
- Goodmail
- Google Buzz
- Google Postmaster Tools
- Graphic
- GreenArrow
- Greylisting
- Greymail
- Groupon
- GT&U
- Guarantee
- Guest Post
- Guide
- Habeas
- Hack
- Hacking
- Hacks
- Hall of Shame
- Harassment
- Hard Bounce
- Harvesting
- Harvey
- Hash
- Hashbusters
- Headers
- Heartbleed
- Hearts
- HELO
- Help
- Henet
- Highspeedinternet
- Hijack
- History
- Holiday
- Holidays
- Holomaxx
- Hostdns4u
- Hostile
- Hostname
- Hotmail
- How To
- Howto
- Hrc
- Hsts
- HTML
- HTML Email
- Http
- Huey
- Humanity
- Humor
- Humour
- Hygiene
- Hypertouch
- I18n
- ICANN
- Icloud
- IContact
- Identity
- Idiots
- Idn
- Ietf
- Image Blocking
- Images
- Imap
- Inbox
- Inbox Delivery
- Inboxing
- Index
- India
- Indiegogo
- Industry
- Infection
- Infographic
- Information
- Inky
- Inline
- Innovation
- Insight2015
- Integration
- Internationalization
- Internet
- Intuit
- IP
- IP Address
- Ip Addresses
- IP Repuation
- IP Reputation
- IPhone
- IPO
- Ipv4
- Ipv6
- Ironport
- Ironport Cisco
- ISIPP
- ISP
- ISPs
- J.D. Falk Award
- Jail
- Jaynes
- JD
- Jobs
- Json
- Junk
- Juno/Netzero/UOL
- Key Rotation
- Keybase
- Keynote
- Kickstarter
- Kraft
- Laposte
- Lavabit
- Law
- Laws
- Lawsuit
- Lawsuits
- Lawyer
- Layout
- Lead Gen
- Leak
- Leaking
- Leaks
- Legal
- Legality
- Legitimate Email Marketer
- Letsencrypt
- Letstalk
- Linked In
- Links
- List Hygiene
- List Management
- List Purchases
- List the World
- List Usage
- List-Unsubscribe
- Listing
- Listmus
- Lists
- Litmus
- Live
- Livingsocial
- London
- Lookup
- Lorem Ipsum
- Lycos
- Lyris
- M3AAWG
- Maawg
- MAAWG2007
- Maawg2008
- MAAWG2012
- MAAWGSF
- Machine Learning
- Magill
- Magilla
- Mail Chimp
- Mail Client
- MAIL FROM
- Mail Privacy Protection
- Mail Problems
- Mail.app
- Mail.ru
- Mailboxes
- Mailchimp
- Mailgun
- Mailing Lists
- Mailman
- Mailop
- Mainsleaze
- Maitai
- Malicious
- Malicious Mail
- Malware
- Mandrill
- Maps
- Marketer
- Marketers
- Marketing
- Marketo
- Markters
- Maths
- Mcafee
- Mccain
- Me@privacy.net
- Measurements
- Media
- Meh
- Meltdown
- Meme
- Mentor
- Merry
- Messagelabs
- MessageSystems
- Meta
- Metric
- Metrics
- Micdrop
- Microsoft
- Milter
- Mime
- Minimal
- Minshare
- Minute
- Mit
- Mitm
- Mobile
- Models
- Monitoring
- Monkey
- Monthly Review
- Mpp
- MSN/Hotmail
- MSN/Hotmail
- MTA
- Mua
- Mutt
- Mx
- Myths
- Myvzw
- Netcat
- Netsol
- Netsuite
- Network
- Networking
- New Year
- News
- News Articles
- Nhi
- NJABL
- Now Hiring
- NTP
- Nxdomain
- Oath
- Obituary
- Office 365
- Office365
- One-Click
- Only Influencers
- Oops
- Opaque Cookie
- Open
- Open Detection
- Open Rate
- Open Rates
- Open Relay
- Open Tracking
- Opendkim
- Opens
- Openssl
- Opt-In
- Opt-Out
- Optonline
- Oracle
- Outage
- Outages
- Outblaze
- Outlook
- Outlook.com
- Outrage
- Outreach
- Outsource
- Ownership
- Owning the Channel
- P=reject
- Pacer
- Pander
- Panel
- Password
- Patent
- Paypal
- PBL
- Penkava
- Permission
- Personalities
- Personalization
- Personalized
- Pgp
- Phi
- Philosophy
- Phish
- Phishers
- Phishing
- Phising
- Photos
- Pii
- PIPA
- PivotalVeracity
- Pix
- Pluscachange
- Podcast
- Policies
- Policy
- Political Mail
- Political Spam
- Politics
- Porn
- Port25 Blocking
- Postfix
- Postmaster
- Power MTA
- Practices
- Predictions
- Preferences
- Prefetch
- Preview
- Primers
- Privacy
- Privacy Policy
- Privacy Protection
- Private Relay
- Productive Mail
- Promotions
- Promotions Tab
- Proofpoint
- Prospect
- Prospecting
- Protocols
- Proxy
- Psa
- PTR
- Public Suffix List
- Purchased
- Purchased Lists
- Purchases
- Purchasing Lists
- Questions
- Quoted Printable
- Rakuten
- Ralsky
- Rant
- Rate Limiting
- Ray Tomlinson
- Rc4
- RDNS
- Read
- Ready to Post
- Readytopost
- Real People
- Realtime Address Verification
- Recaptcha
- Received
- Receivers
- Recipient
- Recipients
- Redirect
- Redsnapper
- Reference
- Registrar
- Registration
- Rejection
- Rejections
- Rejective
- Relationship
- Relevance
- Relevancy
- Removals
- Render Rate
- Rendering
- Repost
- Repudiation
- Reputation
- Requirements
- Research
- Resources
- Responsive
- Responsive Design
- Responsys
- Retail
- Retired Domains
- Retro
- Return Path
- Return Path Certified
- ReturnPath
- Reunion.com
- Reverse Dns
- Rfc
- RFC2047
- RFC2821/2822
- RFC5321/5322
- RFC5322
- RFC8058
- RFC821/822
- RFCs
- Roadr
- RoadRunner
- Rodney Joffe
- ROKSO
- Role Accounts
- Rollout
- RPost
- RPZ
- Rule 34
- Rules
- Rum
- Rustock
- S.1618
- SaaS
- Sales
- Salesforce
- Sass
- SBCGlobal
- Sbl
- Scam
- Scammers
- Scams
- Scanning
- Scraping
- Screamer
- Screening
- Script
- Sec
- Secure
- Security
- Segmentation
- Selligent
- Send
- Sender
- Sender Score
- Sender Score Certified
- Senderbase
- Senderid
- Senders
- Senderscore
- Sendgrid
- Sending
- Sendy
- Seo
- Service
- Services
- Ses
- Seth Godin
- SFDC
- SFMAAWG2009
- SFMAAWG2010
- SFMAAWG2014
- Shared
- Shell
- Shouting
- Shovel
- Signing
- Signups
- Silly
- Single Opt-In
- Slack
- Slicing
- Smarthost
- Smiley
- Smime
- SMS
- SMTP
- Snds
- Snowshoe
- Soa
- Socia
- Social Media
- Social Networking
- Soft Bounce
- Software
- Sony
- SOPA
- Sorbs
- Spam
- Spam Blocking
- Spam Definition
- Spam Filtering
- Spam Filters
- Spam Folder
- Spam Law
- Spam Laws
- Spam Reports
- Spam Traps
- Spam. IMessage
- Spamarrest
- Spamassassin
- Spamblocking
- Spamcannibal
- Spamcon
- Spamcop
- Spamfiltering
- Spamfilters
- Spamfolder
- Spamhaus
- Spamhause
- Spammer
- Spammers
- Spammest
- Spamming
- Spamneverstops
- Spamresource
- Spamtrap
- Spamtraps
- Spamza
- Sparkpost
- Speaking
- Special Offers
- Spectre
- Spf
- Spoofing
- SproutDNS
- Ssl
- Standards
- Stanford
- Starttls
- Startup
- State Spam Laws
- Statistics
- Storm
- Strategy
- Stunt
- Subject
- Subject Lines
- Subscribe
- Subscriber
- Subscribers
- Subscription
- Subscription Process
- Success Stories
- Suing
- Suppression
- Surbl
- Sureclick
- Suretymail
- Survey
- Swaks
- Syle
- Symantec
- Tabbed Inbox
- Tabs
- Tagged
- Tagging
- Target
- Targeting
- Techincal
- Technical
- Telnet
- Template
- Tempo
- Temporary
- Temporary Failures
- Terminology
- Testing
- Text
- Thanks
- This Is Spam
- Throttling
- Time
- Timely
- TINS
- TLD
- Tlp
- TLS
- TMIE
- Tmobile
- Too Much Mail
- Tool
- Tools
- Toomuchemail
- Tor
- Trademark
- Traffic Light Protocol
- Tragedy of the Commons
- Transactional
- Transition
- Transparency
- Traps
- Travel
- Trend/MAPS
- Trend Micro
- Trend/MAPS
- Trigger
- Triggered
- Troubleshooting
- Trustedsource
- TWSD
- Txt
- Types of Email
- Typo
- Uce
- UCEprotect
- Unblocking
- Uncategorized
- Unexpected Email
- Unicode
- Unroll.me
- Unsolicited
- Unsubcribe
- Unsubscribe
- Unsubscribed
- Unsubscribes
- Unsubscribing
- Unsubscription
- Unwanted
- URIBL
- Url
- Url Shorteners
- Usenet
- User Education
- Utf8
- Valentine's Day
- Validation
- Validity
- Value
- Valueclick
- Verification
- Verizon
- Verizon Media
- VERP
- Verticalresponse
- Vetting
- Via
- Video
- Violence
- Virginia
- Virtumundo
- Virus
- Viruses
- Vmc
- Vocabulary
- Vodafone
- Volume
- Vzbv
- Wanted Mail
- Warmup
- Weasel
- Webinar
- Webmail
- Weekend Effect
- Welcome Emails
- White Space
- Whitelisting
- Whois
- Wiki
- Wildcard
- Wireless
- Wiretapping
- Wisewednesday
- Women of Email
- Woof
- Woot
- Wow
- Wtf
- Wttw in the Wild
- Xbl
- Xfinity
- Xkcd
- Yahoo
- Yahoogle
- Yogurt
- Zoidberg
- Zombie
- Zombies
- Zoominfo
- Zurb
