Data Hygiene
What Spamtraps Tell Us
Many blocklists use spamtraps to detect poor sending practices and will cite spamtrap hits as the reason for the blocks. Senders legitimately fear spamtraps showing up on their lists because of this. If spamtraps weren’t used by blocklists no one would really care about them. They’re just another kind of bad address.
Read MoreCleaning old lists
There comes a time in many marketers’ lives where they are faced with and old, stale database and a management chain that wants to mail those addresses. Smart marketers know that delivery problems will arise if they just reactivate all those users. They also know that mailing older addresses can affect current and engaged addresses as well. Still, many executives think there is no downside to mailing old addresses.
Read MoreAddress verification doesn’t fix any real problem
Would you trust an address verification company that used twitter spam to advertise their product?
Read MoreIdentifying domains that don’t accept or send email
A couple folks have asked me recently about MX records that they don’t understand. These records consist of a single . or they contain localhost or they are 127.0.0.1.
Read MoreDead addresses tell us things
There was confirmation this week that the increase in “user unknown” messages from Yahoo is actually Yahoo cleaning out abandoned accounts. At the same time a Yahoo is sending out notifications to folks to log into mail.
Email verification vendor leaking marketer data
I’ve been waiting for this to happen. An email verification vendor has left their database of 800 million email addresses along with detailed individual data. unprotected on the internet. Bob Diachenko reported the discovery yesterday on his blog. Wired also ran an article (An Email Marketing Company Left 809 Million Records Exposed Online) based on his findings.
Read MoreSpamtraps on the brain
I really dislike whomever it was that coined the term pristine spamtraps. I get what they were trying to do, explain the different kinds of spamtraps and how different traps get on your list in different ways. Except… any type of trap can end up on your list in any way.
Read MoreRecycled spamtraps
Spamtraps strike fear into the heart of senders. They’ve turned into this monster metric that can make or break a marketing program. They’ve become a measure and a goal and I think some senders put way too much emphasis on spamtraps instead of worrying about their overall data accuracy.
Read MoreMetric Monetization
As a digital channel, email provides a lot of different metrics for marketers to use. Not only can marketers measure things like open and click rates, but they can tie these numbers back to a particular recipient. This treasure trove of information leads to obsessing over making the numbers look good. For good deliverability senders want low bounce rates, low spamtrap rates, and high engagement rates.
These metrics are important because they’re some of the things that filters look at when making delivery decisions. We care about this data because the receiver ISPs care about the data. The ISPs care about this data because they are characteristics of wanted and/or opt in email.
Over the past few years a number of companies sell services selling good metrics.
Not fooling anyone…
A question came up on the Women of Email Facebook page about sending cold B2B emails. This is one of those areas I have strong opinions about, mostly because I am so tired of getting deceptive and unending messages from folks.
Realistically, cold emailing isn’t going to stop just because recipients hate receiving it. We haven’t wiped out spam in 20+ years, we’re not going to manage it for this one tiny piece. But I do think there are things senders can do to minimize the amount of frustration their spam creates.
10 things every mailer must do
A bit of a refresh of a post from 2011: Six best practices for every mailer. I still think best practices are primarily technical and that how senders present themselves to recipients is more about messaging and branding than best practices. These 6 best practices from 2011 are no longer best, these days, they’re the absolute minimum practices for senders.
If you can’t manage to do these, then find someone who can.
Equifax compromise and their insecure response
Today it was announced that someone infiltrated Equifax earlier this year and stole 143,000,000 identities. These identities include names, birthdates, and addresses, at a minimum. Details are available at your favorite news site.
What I want to talk about is the website they’ve put up to address the issue. This website is Yet Another Example of how the financial services industry trains users to be phishing victims.
Equifax set up a website for people concerned about the possibility of identity theft after this major data leak. The URL, as distributed by the press and linked to from Equifax’s own website is https://www.equifaxsecurity2017.com.
When I was first sent to the site, I thought it was a phishing site because there is absolutely no way to confirm this site is owned and managed by Equifax. Zero. In fact, there’s a lot of evidence that the site isn’t owned by Equifax. And most of the rest of the evidence relies on trusting that the hackers still don’t have some level of access to Equifax systems.
Mike might be spamming, but why?
I’ve been talking a lot about ongoing B2B spam. That is, where senders drop your address into some sort of automation, that sends mail from gmail or amazon and just spams and spams and spams. This is what my mailbox looked like this morning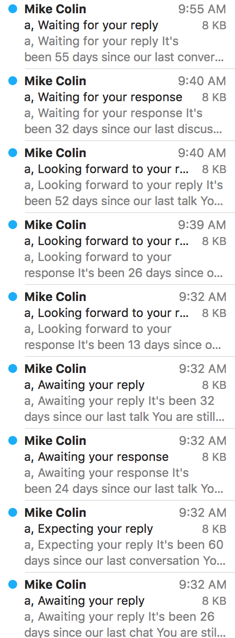
Yes, every one of those emails is sent to the same address. “you are still using the address laura-info@…” Well, no, actually. That was the original address I used as part of our contact on the first iteration of the WttW website. I stopped using that address somewhere around 2002? 3? It’s been a very long time in any case.
Folks, B2B spam is still spam. It doesn’t matter if you register a new domain and use Gmail as your outbounds as a way to avoid filters.
It doesn’t matter…
5 answers you need before mailing old addresses.
From the archives: Mailing old addresses: 5 questions to ask first
James asked the question on twitter:
Disappearing domains
On May 31, British broadband provider EE discontinued service for a number of email domains: Orange.net, Orangehome.co.uk, Wanadoo.co.uk, Freeserve.co.uk, Fsbusiness.co.uk, Fslife.co.uk, Fsmail.net, Fsworld.co.uk, and Fsnet.co.uk.
These domains were acquired by EE as part of multiple mergers and acquisitions. On their help page, EE explains that the proliferation of free email services with advanced functionality has led to a decrease in email usage at these domains.
Yesterday, Terra.co.br announced they were discontinuing email to a number of their free domains as of June 30, 2017: terra.com, terra.com.ar, mi.terra.cl, terra.com.co, terra.com.mx, terra.com.pe, terra.com.ve, and terra.com.ec.
I’m not surprised to see these domains going away and I think we’ll see more of it going forward. The reasons are pretty simple. Mail is not an easy service to run. Mail doesn’t bring in a lot of money. Dedicated mailbox providers do a great job and the addresses from them are portable.
Poor delivery at Gmail but no where else
I’ve mentioned before that I can often tell what ISP is making filter changes by what my calls are about. The last few weeks it’s been Gmail where folks are struggling to get to the inbox. One of the things most clients and potential clients have mentioned is that they’re not having any problems at the other major ISPs.
Read MoreIncentivizing incites fraud
There are few address acquisition processes that make me cringe as badly as incentivized point of sale collection. Companies have tried many different ways to incentivize address collection at the point of sale. Some offer the benefit to the shopper, like offering discounts if they supply an email address. Some offer the benefits to the employee. Some offer punishments to the employee if they don’t collect addresses from a certain percentage of customers.
All of these types of incentive programs are problematic for email collection.
On the shopper side, if they want mail from a retailer, they’ll give an address simply because they want that mail. In fact, asking for an address without offering any incentive is way more likely to get their real address. If they don’t want mail but there is a financial incentive, they’re likely to give a made up address. Sometimes it will be deliverable, but belong to another person. Sometimes it will be undeliverable. And sometimes it will be a spamtrap. One of my delivery colleagues occasionally shares addresses she’s found in customer lists over on her FB page. It’s mostly fun stuff like “dont@wantyourmail.com” and “notonyour@life.com” and many addresses consisting of NSFW type words.
On the employee side there can also be abuses. Retailers have tried to tie employee evaluations, raises and promotions to the number of email addresses collected. Other retailers will actively demote or fire employees who don’t collect a certain number of addresses. In either case, the progression is the same. Employees know that most customers don’t want the mail, and they feel bad asking. But they’re expected to ask, so they do. But they don’t push, so they don’t get enough addresses. Eventually, to protect their jobs, they start putting in addresses they make up.
Either way, incentivizing point of sale collection of information leads to fraud. In a case I read about in the NY Times, it can lead to fraud much more serious than a little spam. In fact, Wells Fargo employees committed bank fraud because of the incentives related to selling additional banking products at the teller.
June 2016: The Month in Email
We’re officially halfway through 2016, and looking forward to a slightly less hectic month around here. I hope you’re enjoying your summer (or winter, for those of you in the Southern Hemisphere).
The source of deliverability problems
Most deliverability problems don’t start where many people think they do. So very often people call looking for deliverability help and tell me all about the things they’re doing to reach the inbox. They’ll tell me about content, they’ll tell me about bounces, they’ll talk about complaints, engagement, opens and clicks. Rarely will they bring up their list source without some prompting on my part.
The reality is, though, that list source is to root of deliverability success and deliverability problems. Where did those addresses come from and what do the people who gave them think you’re going to do with them?
Outsourcing collection to a third party can cause significant issues with delivery. Letting other people collect addresses on your behalf means you lack control over the process. And if you’re paying per address, then there monetary incentive for that company to pad the list with bogus addresses.
Sometimes there are even issues with having your own employees collect addresses from customers. For instance, a retailer requires sales associates collect a minimum percentage of addresses from customers. The company even ties the associates’ evaluations to that percentage. Associates have an incentive to submit addresses from other customers. Or a retailer will offer a discount for an address and customers want the discount but not the mail, so they give a fake address.
All of these things can affect deliverability.
Address collection is the key to delivery, but too many companies just don’t put enough attention to how they’re collecting addresses and entering into the relationship with subscribers. This is OK for a while, and delivery of small lists collected like this can be great. But as lists grow in size, they come under greater scrutiny at the ISPs and what used to work doesn’t anymore.
The first step to diagnosing any delivery problem is to look at the list. All of the things ISP use to measure reputation measure how well you’re collecting addresses. Changing IPs or domains or content doesn’t change the reason mail is being filtered. It just means the filters have to figure out something new to key on.
Want great deliverability? Start with how you’re collecting addresses.
Want to fix deliverability? Start with how you’ve collected addresses, how you’ve stored them and how you’ve maintained them.
5 Simple Tricks to Reach the Inbox
I saw a post over on LinkedIn today. It was from an ESP, talking about their simple tips and tricks for getting into the inbox. The laughable bit was half the “tricks” had nothing to do with getting to the inbox, but rather were about enticing people to open the mail once it’s gotten to the inbox.
There are no “tricks” to getting to the inbox. There used to be some tricks. But the ISPs figured them out and protect against them.
Dueling data
One of the things I miss about being in science is the regular discussions (sometimes heated) about data and experimental results. To be fair, I get some of that when talking about email stuff with Steve. We each have some strong view points and aren’t afraid to share them with each other and with other people. In fact, one of the things we hear most when meeting folks for the first time is, “I love it when you two disagree with each other on that mailing list!” Both of us have engineering and science backgrounds, so we can argue in that vein.
One of the challenges of seemingly contradictory data is figuring out why it seems to disagree. Of course, in science the first step is always to look at your experimental design and data collection. Did I do the experiment right? (Do it again. Always do it again.) Did I record the data correctly? Is the design right? So what did I do differently from what you did? For instance, at one of my labs we discovered that mixing a reagent in plastic tubes created a different outcome from mixing the reagent in glass vials. So many variables that you don’t even think of being variables that affect the outcome of an experiment.
Thoughts on Data Hygiene
 One of the big deliverability vs. marketing arguments has to do with data hygiene and dropping inactive users. Marketers hate that deliverability people tell them to let subscribers go after a long time of no activity from the subscriber.
One of the big deliverability vs. marketing arguments has to do with data hygiene and dropping inactive users. Marketers hate that deliverability people tell them to let subscribers go after a long time of no activity from the subscriber.
Data hygiene is good. Email is not permanent and not forever, and the requirements for data hygiene in the email space are very different than the requirements in the postal mail space. There is no such thing as “dear occupant” in email. I mean, you can sent to occupant, but the occupant can then hit the this is spam button. Too many emails to “occupant” and mail goes to bulk instead of the inbox. These are real risks.
With that being said, there are a lot of things to consider when putting together a data hygiene program. You’re looking to remove people who are no longer interested in your brand as much as they are no longer interested in your mail. You’re trying to suss out who might have abandoned the email address you have for them. It’s complicated.
I’ve worked with a lot of clients over the years to implement data hygiene programs. Sometimes those programs were to deal with a bulk foldering issue. Other times clients have been trying to address a SBL listing. Still other clients were just looking for better control over their email and delivery. In all cases, my goal is to identify and classify their recipients into 3 groups: addresses we know are good, addresses we know are bad, and then addresses we don’t know about.
Good addresses get mailed. Bad addresses get dumped. The challenging bit is what do we do with the unknown addresses? That’s when we start looking at other data the client may have. Purchases? Website visits? What do we have to work with and what else do we know about the people behind the addresses. Once we’ve looked at the data we design a program to take the addresses we don’t know about and drop them into either the good or the bad bucket. How we do that really depends on the specifics of the company, their program and their data. But we’ve had good success overall.
There’s been a lot of discussion on hygiene this week, after Mailchimp published a blog post looking at the value of inactive subscribers. They found something that I don’t find very surprising, based on my observations across hundreds of clients over the years.
Organizational security and doxxing
The security risks of organizational doxxing.
These are risks every email marketer needs to understand. As collectors of data they are a major target for hackers and other bad people. Even worse, many marketers don’t collect valid data and risk implicating the wrong people if their data is ever stolen. I have repeatedly talked about incidents where people get mail not intended for them. I’ve talked about this before, in a number of posts talking about misdirected email. Consumerist, as well, has documented many incidents of companies mailing the wrong person with PII. Many of these stories end with the company not allowing the recipient to remove the address on the account because the user can’t prove they own the account.
I generally focus on the benefits to the company to verify addresses. There are definite deliverability advantages to making sure email address belongs to the account owner. But there’s also the PR benefits of not revealing PII attached to the wrong email address. With Ashley Madison nearly every article mentioned that the email address was never confirmed. But how many other companies don’t verify email addresses and risk losing personally damaging data belonging to non customers.
Data verification is so important. So very, very important. We’ve gone beyond the point where any big sender should just believe that the addresses users give them are accurate. They need to do it for their own business reasons and they need to do it to prevent incorrect PII from being leaked and shared.
It's not about the spamtraps
I’ve talked about spamtraps in the past but they keep coming up in so many different discussions I have with people about delivery that I feel the need to write another blog post about them.
Spamtraps are …
… addresses that did not or could not sign up to receive mail from a sender.
… often mistakenly entered into signup forms (typos or people who don’t know their email addresses).
… often found on older lists.
… sometimes scraped off websites and sold by list brokers.
… sometimes caused by terrible bounce management.
… only a symptom …
August 2015: The month in review
It’s been a busy blogging month and we’ve all written about challenges and best practices. I found myself advocating that any company that does email marketing really must have a well-defined delivery strategy. Email is such vital part of how most companies communicate with customers and potential customers, and the delivery landscape continues to increase in complexity (see my post on pattern matching for a more abstract look at how people tend to think about filters and getting to the inbox). Successful email marketers are proactive about delivery strategy and are able to respond quickly as issues arise. Stay tuned for more from us on this topic.
I also wrote up some deliverability advice for the DNC, which I think is valuable for anyone looking at how to maintain engagement with a list over time. It’s also worth thinking about in the context of how to re-engage a list that may have been stagnant for a while. A comment on that post inspired a followup discussion about how delivery decisions get made, and whether an individual person in the process could impact something like an election through these delivery decisions. What do you think?
As we frequently point out, “best practices” in delivery evolve over time, and all too often, companies set up mail programs and never go back to check that things continue to run properly. We talked about how to check your tech, as well as what to monitor during and after a send. Josh wrote about utilizing all of your data across multiple mail streams, which is critical for understanding how you’re engaging with your recipients, as well as the importance of continuous testing to see what content and presentation strategies work best for those recipients.
Speaking of recipients, we wrote a bit about online identity and the implications of unverified email addresses in regards to the Ashley Madison hack and cautioned about false data and what might result from the release of that data.
Steve’s in-depth technical series for August was a two-part look at TXT records — what they are and how to use them — and he explains that the ways people use these, properly and improperly, can have a real impact on your sends.
In spam news, the self-proclaimed Spam King Sanford Wallace is still spamming, despite numerous judgments against him and his most recent guilty plea this month. For anyone else still confused about spam, the FTC answered some questions on the topic. It’s a good intro or refresher to share with colleagues. We also wrote about the impact of botnets on the inbox (TL;DR version: not much. The bulk of the problem for end users continues to be people making poor marketing decisions.) In other fraud news, we wrote about a significant spearphishing case and how DMARC may or may not help companies protect themselves.
Yes, Virginia, there is list churn
Yesterday I talked about how data collection, management, and maintenance play a crucial role in deliverability. I mentioned, briefly, the idea that bad data can accumulate on a list that isn’t well managed. Today I’d like to dig into that a little more and talk about the non-permanence of email addresses.
A common statistic used to describe list churn is that 30% of addresses become invalid in a year. This was research done by Return Path back in the early 2000’s. The actual research report is hard to find, but I found a couple articles and press releases discussing the info.
Data is the key to deliverability
Last week I had the pleasure of speaking to the Sendgrid Customer Advisory Board about email and deliverability. As usually happens when I give talks, I learned a bunch of new things that I’m now integrating into my mental model of email.
One thing that bubbled up to take over a lot of my thought processes is how important data collection and data maintenance is to deliverability. In fact, I’m reaching the conclusion that the vast majority of deliverability problems stem from data issues. How data is collected, how data is managed, how data is maintained all impact how well email is delivered.
Collecting Data
There are many pathways used to collect data for email: online purchases, in-store purchases, signups on websites, registration cards, trade shows, fishbowl drops, purchases, co-reg… the list goes on and on. In today’s world there is a big push to make data collection as frictionless as possible. Making collection processes frictionless (or low friction) often means limiting data checking and correction. In email this can result in mail going to people who never signed up. Filters are actually really good at identifying mail streams going to the wrong people.
The end result of poor data collection processes is poor delivery.
There are lots of way to collect data that incorporates some level of data checking and verifying the customer’s identity. There are ways to do this without adding any friction, even. About 8 years ago I was working with a major retailer that was dealing with a SBL listing due to bad addresses in their store signup program. What they ended up implementing was tagged coupons emailed to the user. When the user went to the store to redeem the coupons, the email address was confirmed as associated with the account. We took what the customers were doing anyway, and turned it into a way to do closed loop confirmation of their email address.
Managing Data
Data management is a major challenge for lots of senders. Data gets pulled out of the database of record and then put into silos for different marketing efforts. If the data flow isn’t managed well, the different streams can have different bounce or activity data. In a worst case scenario, bad addressees like spamtraps, can be reactivated and lead to blocking.
This isn’t theoretical. Last year I worked with a major political group that was dealing with a SBL issue directly related to poor data management. Multiple databases were used to store data and there was no central database. Because of this, unsubscribed and inactivated addresses were reactivated. This included a set of data that was inactivated to deal with a previous SBL listing. Eventually, spamtraps were mailed again and they were blocked. Working with the client data team, we clarified and improved the data flow so that inactive addresses could not get accidentally or unknowingly reactivated.
Maintaining Data
A dozen years ago few companies needed to think about any data maintenance processes other than “it bounces and we remove it.” Most mailbox accounts were tied into dialup or broadband accounts. Accounts lasted until the user stopped paying and then mail started bouncing. Additionally, mailbox accounts often had small limits on how much data they could hold. My first ISP account was limited to 10MB, and that included anything I published on my website. I would archive mail monthly to keep mail from bouncing due to a full mailbox.
But that’s not how email works today. Many people have migrated to free webmail providers for email. This means they can create (and abandon) addresses at any time. Free webmail providers have their own rules for bouncing mail, but generally accounts last for months or even years after the user has stopped logging into them. With the advent of multi gigabyte storage limits, accounts almost never fill up.
These days, companies need to address what they’re going to do with data if there’s no interaction with the recipient in a certain time period. Otherwise, bad data just keeps accumulating and lowering deliverability.
Deliverability is all about the data. Good data collection and good data management and good data maintenance results in good email delivery. Doing the wrong thing with data leads to delivery problems.
April 2015: The Month in Email
We started the month with some conversations about best practices, both generally looking at the sort of best practices people follow (or don’t) as well as some specific practices we wanted to look at in more depth. Three for this month:
Read MoreMythbusting deliverability and engagement
Yesterday I published an article talking about an engagement webinar hosted by the EEC and DMA. I made a couple predictions about what would be said.
Read MoreTarget "acquires data"
It was our priority to inform as many guests as quickly as possible. Relevant emails were pulled from a variety of sources.
Read More
@AskTarget
Target acquires email addresses, exposing more customers to data breaches
As most folks now know hackers broke into Target systems last December and stole financial and other data from 110 million customers. Target has been responding to this breach reasonably well. They’ve been notifying customers that were affected and they’re providing credit monitoring for affected individuals. They seem to be totally on top of protecting their customer’s data and privacy.
Mostly.
They seem to be purchasing or otherwise acquiring email addresses from at least one major retailer in order to send out notifications about the breach to customers that never gave them email addresses. Yes, even those of us who chose not to give Target email addresses are receiving email from them.
I understand Target’s drive to contact affected users. I even appreciate that. What I don’t appreciate is that Target appears to be compromising my security in order to notify me my security was compromised. The data of mine that was compromised at Target would be credit card and possibly address information. My email address was not part of the compromise. So what does Target do? They go and acquire my email address from a third party.
Their solution to the compromise is collecting more data that is vulnerable to compromise from unrelated third parties? I’m not sure this is the most consumer friendly thing Target could do. In my case, Target sent mail to an address I’ve only given to Amazon. That means I now need to worry about my Amazon account security, on top of everything else.
Ironically, the email sent by Target tells me that I can click a link and get free credit monitoring. Then the email goes on to tell me the following:
- Never share information with anyone over the phone, email or text, even if they claim to be someone you know or do business with. Instead, ask for a call-back number.
- Delete texts immediately from numbers or names you don’t recognize.
- Be wary of emails that ask for money or send you to suspicious websites. Don’t click links within emails you don’t recognize.
Don’t click links within emails I don’t recognize? You mean like the one you just sent me? With a link to a credit monitoring website?
I appreciate the notice. I don’t appreciate is that Target went out of their way to collect more information about me than I actually gave them. I am now worried about Amazon’s security as well. How did Target get an address only provided to Amazon? I don’t appreciate that my efforts to keep my information secure (not providing email address to Target) was undermined by Target themselves.
The full text of the email, with the relevant headers (munged slightly for privacy) is under the cut, if anyone is interested.
Misdirected email
While this does seem to be more common with gmail addresses, it’s not solely limited to gmail. I’ve written about this frequently.
Growing your list carefully
Karl Murray wrote a great set of recommendations for growing an email marketing list. I really can’t think of anything I would have said differently. Touching customers and getting contact information from them is great, but there are situations where this gets bad addresses. Too many bad addresses can impact delivery.
So how do you grow your list without falling into a delivery trap? The specific recommendations, as always, depend on your specific situation. But knowing how bad addresses get onto your list will allow you to implement mitigation strategies that actually work.
Uploading your address book to social media
I am one of the moderators of a discussion list working on a document about getting off blocklists. If anyone not on the list attempts to post to the list I get a moderation request. One came through while I was gone. Now, I don’t really think Jim Mills wants to be friends with a mailing list. I think he probably gave LinkedIn his email password and LinkedIn went through and scraped addresses out of his address book and sent invitations to all those addresses.
Now, I don’t really think Jim Mills wants to be friends with a mailing list. I think he probably gave LinkedIn his email password and LinkedIn went through and scraped addresses out of his address book and sent invitations to all those addresses.
I don’t have any problem with connecting to people on social media. I do even understand that some people have no problem giving their passwords over to let social media sites plunder their address books and find connections. What I do have a problem with is social media sites that don’t do any pruning or editing of the scraped addresses before sending invitations.
In this case, the email address, like many mailing lists, has in the email address “mailman.” While it’s probably impossible to weed out every mailing list, support address and commercial sender, it doesn’t seem like it would be too difficult to run some minor word matching and filtering. It’s not even like those addresses have to be removed from invites. Instead they could be presented to the user for confirmation that these are real people and addresses.
Yes, it’s friction in the transaction and it costs money to do and do well. But those costs and friction are currently offloaded onto uninvolved third parties.
Data, data, elections and data
One of the interesting stories coming out of the recent US Presidential election is how much data the Obama Campaign collected about voters, volunteers and donors. Today Politico talks about how valuable that data is, and how many Democrats want to get their hands on it.
Read MoreHarvesting and forging email addresses
For the contact address on our website, Steve has set up a rotating set of addresses. This is to minimize the amount of spam we have to deal with coming from address harvesters. This has worked quite well. In fact it works so well I didn’t expect that publishing an email address for taking reader questions would generate a lot of spam.
Boy, was I wrong. That address has been on the website less than a month and I’m already getting lots of spam to it. Most of it is business related spam, but there’s a couple things that make me think that someone has been signing that address up to mailing lists.
One is the confirmation email I received from Yelp. I don’t actually believe Yelp harvested my address and tried to create me an email account. I was happy when I got the first mail from Yelp. It said “click here to confirm your account.” Yay! Yelp is actually using confirmations so I just have to ignore the mail and that will all go away.
At least I was happy about it, until I started getting Yelp newsletters to that address.
Yelp gets half a star for attempting to do COI, but loses half for sending newsletters to people who didn’t confirm their account.
I really didn’t believe that people would grab a clearly tagged address off the blog and subscribe it to mailing lists or networking sites. I simply didn’t believe this happened anymore. I know forge subscribing used to be common, but it does appear that someone forge signed me up for a Yelp account. Clearly there are more dumb idiots out there than I thought.
Of course, it’s not just malicious people signing the address up to lists. There are also spammers harvesting directly off the website.
I did expect that there would be some harvesting going on and that I would get spam to the address. I am very surprised at the volume and type of spam, though. I’m getting a lot of chinese language spam, a lot of “join our business organization” spam and mail claiming I subscribed to receive their offers.
Surprisingly, much of the spam to this address violates CAN SPAM in some way shape or form. And I can prove harvesting, which would net treble damages if I had the time or inclination to sue.
It’s been an interesting experience, putting an unfiltered address on the website. Unfortunately, I am at risk of losing your questions because of the amount of spam coming in. I don’t think I’ve missed any, yet, but losing real mail is always a risk when an address gets a lot of spam – whether or not the recipient runs filters.
I’m still pondering solutions, but for now the questions address will remain as it is.
Handling replies to bulk mail
This week’s Wednesday question comes from Ryan W.
I’ve been noticing a few e-mail accounts who reply to our e-mail sends with spammy type replies such as, “hey this is intense…..(link)” what do you think should we be removing those e-mails from our mailing?
Read More
Misdirected email
Al has another post about another company sending mail to a customer that gave an email address that didn’t belong to them. The person receiving the misdirected email has no effective way to make it stop, and is getting more and more frustrated with the ongoing spam. (Consumerist article)
Read MoreData Cleansing part 2
In an effort to get a blog post out yesterday before yet another doctor’s appointment I did not do nearly enough research on the company I mentioned selling list cleansing data. As Al correctly pointed out in the comments they are currently listed on the SBL. And when I actually did the research I should have done it was clear this company has a long term history of sending unsolicited email.
Poor research and a quickly written blog post led to me endorsing a company that I absolutely shouldn’t have. And I do apologize for that.
With all that being said, Justin had a great question in the comments of yesterday’s post about data cleansing.
Data Cleansing
According to Ken, Outward Media has productized a database of 300,000,000 email addresses that should never be mailed.
Read MoreMore than just getting past the filters
I’ve been feeling a little philosophical lately. My thoughts are meandering a lot around the whys and the deeper issues surrounding stuff, including email. It means I’m a bit more distracted and less focused than usual. And more prone to pose questions than usual. This was part of the introspection that led me to write the motivating people post last week. I’m trying to figure out how to motivate volunteers in two different realms. And there’s always the question of how do I present a solution to clients in a way that motivates them to take my advice. Sure, I get paid either way, but I really like it when clients take my advice and see success.
There are other places this mental meandering is taking me.
I’m currently working on a project for a client. This particular client is struggling to get mail delivered to a very mobile business audience. In the target field, people change jobs regularly and email addresses can change multiple times a year. One of the things I’m working on for them is how to get email to the right people, that is the people who opted in, when their addresses change so frequently.
This is delivery consulting, but this project really brings home how much more there is to delivery than avoiding filters. Filters are the least of this client’s problem. The real problem is the mobility of their audience. As I was thinking about how to address this issue of mobility, I realized that my job as a delivery expert has gone well beyond telling people how to get their mail past filters.
My job is much more about helping people succeed at what it is that they’re trying to do with email. How can email work for you and for your target audience?
Looking at the broader picture means I’m less likely to focus on the minutia of “spam words” and subject lines and best time of day to send. Sure, there are always tweaks to make in an email. There are always things to test. There are always changes to try. But the effect of those changes is not near as great as actually sending mail that meets the needs of the audience.
Often clients come to me so overwhelmed in the details they forget the bigger picture. I help them find that picture again. My job is much more than getting through the filters, it’s about finding success for clients.
Lasting effects from aggressive marketing
Return Path has an interesting post on the lasting effects of aggressive holiday marketing.
Read MoreData hygiene and bouncing zombies
There are a number of folks who tell me there can be no zombie addresses on their lists, they aggressively remove any address that bounces. The problem is that zombie addresses don’t bounce, at least not always. And even when ISPs say they have a policy to bounce email after a certain period of time with no access, that’s not always put into practice.
How do I know that ISPs don’t always deactivate addresses on the schedules they publish? Because I have seen addresses not be deactivated.
I have addresses in a lot of places that I go for long periods of time not checking. It’s rare that they’re taken from me or reject mail – most of the time they’re special test addresses I use when diagnosing issues. This post is based on my experiences with those addresses and how abandoned addresses are treated at some ISPs.
For Gmail I have two examples of addresses not being deactivated.
In July 2011, we set up a test address to look at how Gmail was handling authentication. We sent a matrix of different test emails to it, with valid and invalid SPF and DKIM signatures. We pulled the data from the account. I don’t know for certain when the last time I logged in, but it was August or September of last year. So we have an address that has been dormant since September 2011.
I just sent mail to the account and google happily accepted it.
Mar 2 07:03:22 misc postfix/smtp[11770]: 11CA12DED3: to=<wttwtestacct@gmail.com>, relay=gmail-smtp-in.l.google.com[74.125.127.27]:25, delay=1.8, delays=0.25/0.02/0.56/0.93, dsn=2.0.0, status=sent (250 2.0.0 OK 1330700602 x8si8608852pbi.66)
I have another google account (apparently) that my records show I set up sometime in 2010. The login info was saved October 2010. I don’t know when the last time I logged in was, but given I’d forgotten the existence of the account it’s a good bet that it has been more than a year. That account is also accepting mail as of today.
Mar 2 07:06:25 misc postfix/smtp[11836]: 8D90C2DED3: to=<phphendrie@gmail.com>, relay=gmail-smtp-in.l.google.com[74.125.127.27]:25, delay=1.6, delays=0.26/0.02/0.68/0.66, dsn=2.0.0, status=sent (250 2.0.0 OK 1330700785 a8si4075740icw.96)
For Hotmail I also have quite a bit of history and information. I signed up for my first Hotmail account in 1997. That was an account I used the address to post to usenet, but I didn’t actually use it for mail. I’d check it occasionally (usually when someone said in the newsgroup that they were going to email me) but it wasn’t an address I used regularly. As I moved from posting regularly in usenet, I started checking that account even less.
For a while, if I went more than 6 months checking my Hotmail account they would make me “re-claim” it. What would happen when I’d log in is I’d get a message along the lines of “well, we disabled this account due to inactivity, do you want it back?” I’d say yes, have to go through the setup process again and it would be my account. Mail was deleted during the disabling, and I am guessing they rejected anything new going to that account. I went through this dance for 4 or 5 years. I even had my calendar set to remind me to login every 6 months or so. There was some sentimental value to the address that kept me logging in. I have that same username at every major free ISP: Gmail, Hotmail, Yahoo and AOL, so it’s “my” address.
About 6 or 7 years ago, that behavior changed. I stopped getting the request to reclaim my account. Instead I could just log in. I’d still have mail (mostly spam as the address is on *lots* of lists and millions CDs). I still check it irregularly. I don’t have any idea when the last time I checked it was, but I think it’s been since at least November and probably longer back than that. Hotmail is still accepting mail for that address as well.
It’s anecdotal evidence, at best, but it ‘s the type of evidence that is acceptable even when it’s anecdotal. There are some addresses that are abandoned for long periods of time at the free mailbox providers and they’re are not all automatically pulled from the ranks of active addresses.
What does this mean for senders? It means that data hygiene has to go beyond just removing addresses that bounce. ISPs are not disabling addresses consistently enough for marketers to be able to trust that all addresses on their list are active just because they are accepting email.
This is the root of the recommendation to put in a hygiene program, this is why senders need to look at who is actually engaged with their brand and make some hard decisions about shooting zombies in the head.
Data hygiene
I talk about data hygiene with clients a lot. In my experience, poor data hygiene is the number one reason that legitimate, permission based marketing ends up in the junk folder. Too many marketers don’t remove abandoned addresses from their mailing lists. As the abandoned addresses build up, eventually the list accumulates enough zombie addresses that it looks similar to a spammer’s list.
I’ve talked in depth about zombie accounts previously (part 1, part 2, part 3, apocalypse) and they talk a lot more about why we have zombies accounts and why they’re just starting to be a bigger issue for marketers. Not only are we just starting to hit critical mass with zombie accounts, but ISPs are really starting to weigh engagement in their delivery decisions. Zombie accounts are not engaged with mail. Heck, they’re not even engaged with their own email addresses.
Many marketers, though, hate the idea of data hygiene. They hate thinking about losing a potential customer. They can show me numbers that say someone didn’t open an email for 18 months and then spent hundreds of dollars on a purchase. Or they can tell me that 10% of their revenue came from people who hadn’t opened an email in more than 12 months.
I don’t want to take those subscribers away from you, the ones who are engaged with your brand or your mail in some un-trackable way. But I do want to stop the zombies from eating your delivery.
Six best practices for every mailer
People get into all sorts of details when talking about best practices. But so much of email depends on the type of email and the target market and the goals of the sender. It’s difficult to come up with universal best practices.
I’ve said in the past that I think that best practices are primarily technical. I don’t believe there is a best frequency or a best time to send mail or a best image to text ratio.
My top 6 best practices every marketer should be doing (and too few are).
It would be nice…
It’d be nice to have a tool to uncover the zombie email addys, but until then, read this from @wise_laura: http://bit.ly/jxjZ9M Kelly Lorenz
Read More
Nothing is forever, even email
Yesterday I talked about how important it was to send welcome messages when you discover old email addresses. Today on the Return Path Blog, Tami Monahan Foreman shares an example email that does just that, but not as well as one might hope.
Read MoreBroken signup processes
DJ Waldow wrote a post on explicit permission over on Mediapost. I think he hit on some interesting bits and wanted to comment on them. In order to comment on a Mediapost blog, you have to register.
I’ve thought about it before, but every time I start the process I get to the page asking for detailed demographic information and decide no. This time, I was inspired enough by DJ to get to the second page of the signup process. This requires me to identify what type of marketing I’m interested in and won’t let me past the page until I click something. I’m not interested in anything, so I close the webpage. I can always write my own blog post responding to DJ.
I return to my inbox to discover a welcome message from Mediapost. It seems I am now a member and will be receiving email and specials and all the stuff I didn’t want from them.
This isn’t unusual. There are tons of websites on the net that don’t require you to complete a signup process in order to be added to their database. One of the worst I experienced was 1-800-Pet-Meds. They added me to their database when I abandoned a cart (what I wanted required a prescription from them, whereas I could just go into my vet’s and pick it up, so I’ll just pay the vet’s prices). They added me to their mailing list and couldn’t unsubscribe me because I was not in their customer database. Everything was done with the magic order number, which I didn’t have because I never ordered with them. That was fun to sort out.
It’s a bad idea to add people who don’t complete the signup or purchase process to your mailing lists. If you’re worried about losing a potential customer, then you can send mail reminding them to complete the process (or purchase). If you’re very into customer service, you can ask them if they are interested in future specials from you: would you like to opt-in to our mailing list anyway? Or you can give them the opportunity to remove their information from your database.
Would you buy a used car from that guy?
There are dozens of people and companies standing up and offering suggestions on best practices in email marketing. Unfortunately, many of those companies don’t actually practice what they preach in managing their own email accounts.
I got email today to an old work email address of mine from Strongmail. To be fair it was a technically correct email. Everything one would expect from a company handling large volumes of emails. It’s clear that time and energy was put into the technical setup of the send. If only they had put even half that effort into deciding who to send the email to. Sadly, they didn’t.
My first thought, upon receiving the mail, was that some new, eager employee bought a very old and crufty list somewhere. Because Strongmail has a reputation for being responsible mailers, I sent them a copy of the email to abuse@. I figured they’d want to know that they had a new sales / marketing person who was doing some bad stuff.
I know how frustrating handling abuse@ can be, so I try to be short and sweet in my complaints. For this one, I simply said, “Someone at Strongmail has appended, harvested or otherwise acquired an old email address of mine. This has been added to your mailing list and I’m now receiving spam from you. ”
They respond with an email that starts with:
“Thank you for your thoughtful response to our opt-in request. On occasion, we provide members of our database with the opportunity to opt-in to receive email marketing communications from us.”
Wait. What? Members of our database? How did this address get into your database?
“I can’t be sure from our records but it looks like someone from StrongMail reached out to you several years ago. It’s helpful that you let us know to unsubscribe you. Thank you again.”
There you have it. According to the person answering email at abuse@ Strongmail they sent me a message because they had sent mail to me in the past. Is that really what you did? Send mail to very old email addresses because someone, at some point in the past, sent mail to that address? And you don’t know when, don’t know where the address came from, don’t know how it was acquired, but decided to reach out to me?
How many bad practices can you mix into a single send, Strongmail? Sending mail to addresses where you don’t know how you got them? Sending mail to addresses that you got at least 6 years ago? Sending mail to addresses that were never opted-in to any of your mail? And when people point out, gently and subtly, that maybe this is a bad idea, you just add them to your global suppression list?
Oh. Wait. I know what you’re going to tell me. All of your bad practices don’t count because this was an ‘opt-in’ request. People who didn’t want the mail didn’t have to do anything, therefore there is no reason not to spam them! They ignore it and they are dropped from your list. Except it doesn’t work that way. Double opt-in requests to someone has asked to be subscribed or is an active customer or prospect is one thing. Requests sent to addresses of unknown provenance are still spam.
Just for the record, I have a good idea of where they got my address. Many years ago Strongmail approached Word to the Wise to explore a potential partnership. We would work with and through Strongmail to provide delivery consulting and best practices advice for their customers. As part of this process we did exchange business cards with a number of Strongmail employees. I suspect those cards were left in a desk when the employees moved on. Whoever got that desk, or cleaned it out, found those cards and added them to the ‘member database.’
But wait! It gets even better. Strongmail was sending me this mail, so that they could get permission to send me email about Email and Social Media Marketing Best Practices. I’m almost tempted to sign up to provide me unending blog fodder for my new series entitled “Don’t do this!”
Zombie Apocalypse
I hope my series on zombie addresses has convinced you that there are zombie addresses on your list and that you should be concerned about the effect they have on delivery and metrics. Today I’d like to talk about what you can do to get rid of zombie addresses without affecting too many actual subscribers.
One thing that many companies struggle with while dealing with zombie addresses is letting go of addresses. They are so tied up in the idea that a bigger list is better that they can’t let them go. Even if a particular address has not had any activity in 18 or 24 months, they insist that they can’t give it up, it might come back and the customer might make a giant purchase. No. It’s a zombie. It’s not coming back, except to eat your brains.
The first step to dealing with zombies is to acknowledge their existence. They are there, they are on your lists and they are dirtying up your lists. Pretending they’re not there does not make them go away. They are zombies. In no case is there a human inside. There is no potential sale lurking, waiting to jump out and act on that perfectly crafted offer.
The second thing to remember is that the humans that used to have the zombie addresses found you once and they are still interested in what you’re offering then they will find you again. They may even already be back on your list with their new email address.
While you can’t identify zombie addresses specifically, you can identify addresses that act like zombie addresses. These are addresses that have no activity over a long period of time, more than 12 months. For these addresses that haven’t had activity in 12 – 18 – 24 months, you want to confirm with the recipient that they are there and want to continue to receive mail from you.
The best way to notify them is to send an email asking if they want to remain on your list. If they fail to act, you will remove them from future mailings. Short, sweet and will let you drop off zombie addresses without much effort on your part.
I know, I know, you aren’t ready to let go so fast. After all, some people have come back after 24 months and made a purchase from the perfect offer. They’re not dead yet! OK. But you can’t get a response from them through email. They just don’t care enough about what you’re sending. That’s when you contact them through another channel.
For instance, if the email address is tied to a web account, say a social networking site or bank account or a web forum, you can also contact the user through your website. Next time they log in, send them a message that says their email address has been removed due to inactivity, but if they want to reactivate they can do so at the subscriber preference center or profile page. When they do, send them an email to confirm that this is the address where they want to receive mail. At this point you can give them a link or a magic cookie to past into the website to verify the address.
Or if you’re a bigger retailer you can send alerts to your customer service staff, so when the account holder contacts you by phone with a question or an order you can get an updated email address. If you have a loyalty program, have an alert come up at the point of sale and the clerk can ask for an updated email address.
I even know one company that would send postcards to their zombie accounts in an effort to re-engage them and get an active email address from them.
If the person never comes back, if they don’t ever interact with your business again, if none of the channels work to contact them and update the address then it really is best to just let the relationship go. It may not be you, or anything you’ve done. People move on, their interests change and that’s part of life. They may have moved outside of your service area, or they may have joined your list for a specific product that they don’t need or you don’t sell. They may have died and turned into a real zombie. In any case, they are not a viable prospect for your mail.
Email addresses and business relationships are not forever. Letting zombie addresses go is important for the health of any email marketing program.
Zombie email: Part 3
Last week, in Zombie email: part 1 and part 2 I talked a little about the history of email addresses and how changes in the ISP industry in the early to mid 2000’s brought about the rise of zombie email addresses. Today we’ll look at the effect zombie addresses have on email stats and why ISPs are starting to monitor zombie addresses.
A zombie address, despite the fervent belief of some email marketers, doesn’t come back to life. The person who initially registered that address has decided to stop using that email address. The defining factor of a zombie address is that there isn’t now and won’t be anyone in the future reading email sent to that address. There is no human there to read or react to any email sent to that address.
A zombie address does not represent an actual recipient, they’re just remnants of a recipient that once was present.
Having a list containing any significant number of zombie addresses can throw off metrics enough to mislead a sender about the effectiveness of their email marketing program. Sometimes, the zombie addresses make the metrics look worse, sometimes they make metrics look better. In either case, the metrics don’t accurately represent the performance of a marketing program.
Zombie email addresses do bulk out a mailing list, making lists look bigger. They’re not real addresses, so they don’t reflect quality, but they do impress marketers that think bigger is always better. But, in reality, you may as well add thousands of addresses at non-existent domains for the real value these addresses bring to your list.
Zombie email addresses on a list depresses any metric that use “number of emails sent” or “number of emails accepted” as a denominator. If 10% of a list is zombie addresses, then an open rate reported as 15% will actually be an open rate of 16.7%. The more zombie addresses on a list, the more the statistics will be depressed.
In addition to having lower open rates, lists with more zombie addresses also have a lower complaint rate. In fact, in the recent past spammers have padded their lists with zombie addresses as a way to artificially lower their complaint rates.
Spammers using addresses created just to bulk up the denominator and lower complaint rates have led ISPs to start monitoring the types of addresses on a particular list. I first heard about ISPs looking at recipient profiles at a meeting in 2006, so it is not, in any way, a new technique for ISPs. What is new is the number of zombie addresses on legitimate, well maintained lists, and the fact that they are present in high enough volume to affect reputation and delivery.
ISPs use zombie addresses to monitor the reputation of a sender because it is a more accurate way to measure what the recipients think about an email and that sender. Senders ignore zombie addresses because they make some stats look bigger (total list size) and better (lower complaint rates). Many senders also believe that addresses come back to life, despite all evidence to the contrary, and will not purge an address for any reason other than it bounces. They’d rather live with inaccurate and misleading metrics than removing non-performing addresses.
Tomorrow, in the final post of this series, we’ll examine how senders can identify potential zombie addresses and what steps they can take protect themselves from the negative reputation hit from zombie addresses. (Zombie Apocalypse)
Zombie email: Part 2
In zombie email: part 1 I talked about how email addresses were tightly tied to internet access in the very early years of the internet. We didn’t have to worry about zombie email addresses because when an account was shut down, or ignored for a long time then mail would start bouncing and a sender could stop sending to that account.
There were two major changes to email accounts in the early 2000’s that led to the rise of zombie emails.
People started decoupling their internet access from their email addresses. Free addresses were easy to get and could be checked from everywhere. No longer did they have to dial in to get email, they could access it from outside the office and outside the home. Mobile devices, including the first generation of smart phones and laptops, helped drive people to use email addresses that they could access from any network. The easy access to free mail accounts and the permanence led people to adopt those addresses as their primary address.
When people changed addresses, for whatever reason, they didn’t have to stop paying. There was no way to tell the free ISPs to stop accepting mail for that address. Free mail providers would let addresses linger for months or years after the user had stopped logging in. Sometimes those addresses would fill up and start bouncing email, but they were not often turned off by the ISPs.
The lack of purging of abandoned addresses was the start of dead addresses accumulating on mailing lists. But there weren’t that many addresses in this state, and eventually they would fill up with mail. When they were full the ISP would stop accepting new mail for that account, and the address would bounce off a mailing list.
Everything changed with the entrance of Gmail onto the scene. When Gmail launched in 2004 they were providing a whole GB of storage for email accounts a totally unheard of storage capacity. Within a year they were providing multiple gigabytes of storage. Other freemail systems followed Gmail’s lead and now all free accounts have nearly unlimited storage. Plus, any mail in the spam folder was purged after a few weeks and bulk mail doesn’t count against the users’ storage quota. Now, an abandoned email account will almost never fill up thus senders can’t use over quota bounces to identify abandoned accounts.
Now we’re stuck in a situation where SMTP replies can’t be used to identify that there is no one home inside a particular email account. Senders can’t distinguish between a quiet subscriber and an abandoned address. ISPs, however, can and are using zombie addresses as a measure of a senders reputation.
On Monday we’ll talk about why and how zombie addresses can affect delivery. (Zombie emails: part 3)
Tuesday, we’ll talk about strategies to protect your list from being taken over by zombies. (Zombie Apocalypse)
Zombie email: Part 1
Zombie email addresses: those email addresses that never really die, eat your brains and destroy your email delivery. To understand zombie addresses and why they’re just now becoming a problem, we really need to understand some of the history of email addresses.
In the early days of the net, people got an email address usually associated directly with their access to the Internet. Many of them ended with .edu or .gov. I even had one that ended in .BITNET for a while. The first ISPs followed this convention. Users signed up for an account at a local dialup and were assigned an email address, and that was their email address. It wasn’t until the late 1990’s where there was widespread access to multiple email addresses.
What this means is that when people left a job, or canceled their Internet access their email address went away. Addresses that were abandoned would, after a short period of time, start bouncing back with user unknown, giving everyone the opportunity to stop mailing that account.
Even with the advent of multiple addresses for a single account and the easy availability of free addresses from places like Hotmail addresses that had been abandoned would still bounce off a list. Why? Because accounts had limited storage. My first dialup account had, I think, 10MB of space. It may have been as much as 20MB, but it wasn’t very much. Accounts receiving a lot of mail that weren’t checked frequently would fill up and start bouncing mail. Senders would be able to remove abandoned accounts because they were full.
Tomorrow we’ll talk about two things happened in the early 2000’s that changed email and led to the rise of zombie email.
Zombie Email: Part 2
Zombie Email: Part 3
Zombie Apocalypse
The importance of data hygiene
Over the weekend, one of the major ISPs purged a lot of abandoned accounts from their system. This has resulted in a massive increase in 550 user unknown bounces at that ISP. This ISP is one of those that uses bounces to feed into their reputation system and the purge may cause otherwise good senders to be blocked temporarily.
Talking to clients and other industry folks, it looks like the addresses that have newly bounced off had zero activity for at least 6 months. Nothing. Nada. No clicks. No opens. No interaction.
This is why data hygiene is so critical. Just because the emails are being accepted at the ISP, and even showing inbox placement at the mailbox monitoring companies does not mean that there is actually someone reading your email. Failure to look at overall data means that when an ISP bulk deletes abandoned accounts then bounces will increase. While I don’t expect this to have any real, long term effect on sender reputation I do expect that some senders with a lot of cruft on their list will see some short term delivery problems.
Companies that run re-engagement campaigns saw a whole lot less bouncing and even less blocking as a result of the purge. They were removing addresses that were non-responsive all along and thus didn’t have major deadwood on their list.
Ongoing data hygiene shows you what your list really is, not your list plus abandoned accounts. The addresses that the ISP purged? They were not valuable anyway. No one was reading that mail for at least 6 months.
If you did see a spike in bounces this weekend at a major ISP, you should really look at engagement. If some percentage of recipients at one ISP are actually non-existent, then it’s likely that about that same number are non-existent at other major ISPs as well. What are you going to do to identify and remove those dead addresses from your lists?