Esp
There’s something about bounces
I’ve shared a version of this image repeatedly. I think it was only my Facebook friends that got the stick figure screaming in frustration, though.
Read MoreESP being phished is a Black Friday cataclysm
There is currently a phishing attack against a major ESP. The mail came through what I presume was a compromised account hosted at one of the providers. It’s just as possible this was a domain set up for the sole purpose of phishing, though.
Read MoreJuly 2017: The month in email
August is here, and as usual, we’re discussing spam, permissions, bots, filters, delivery challenges, and best practices.
One of the things we see over and over again, both with marketers and with companies that send us email, is that permission is rarely binary — companies want a fair amount of wiggle room, or “implied permission” to send. There are plenty of examples of how companies try to dance around clear permissions, such as this opt form from a company we used to do business with. But there are lots of questions here: can you legitimately mail to addresses you haven’t interacted with in 5 years? 10 years? What’s the best way to re-engage, if at all?
We frequently get questions about how to address deliverability challenges, and I wrote up a post about some of the steps we take as we help our clients with this. These are short-term fixes; for long-term success, the most effective strategy is sending email that people want and expect. Engagement is always at the core of a sustainable email program.
We’ve also discussed the rise of B2B spam, and the ways in which marketing technologies contribute to the problem. B2B marketers struggle to use social and email channels appropriately to reach customers and prospects, but still need to be thoughtful about how they do it. I also wrote about some of the ways that marketing automation plugins facilitate spam and how companies should step up to address the problem. Here’s an example of what happens when the automation plugins go awry.
I wrote a few posts about domain management and the implications for security and fraud. The first was about how cousin domain names can set users up for phishing and fraud, and the second was a useful checklist for looking at your company’s domain management. We also looked at abuse across online communities, which is an increasing problem and one we’re very committed to fighting.
I also highlighted a few best practices this month: guidelines for choosing a new ESP and active buttons in the subject line for Gmail.
And finally, we celebrated the 80th birthday of the original SPAM. If you’re a regular reader of this blog, you probably already know why unwanted email is called SPAM, but just in case, here’s a refresher….
Ongoing subscription attack
Brian Krebs posted a couple days ago about his experience with the subscription bomb over the weekend. He talks about just how bad it was over the weekend.
Read MoreSpamhaus comments on subscription attack
Steve Linford, CEO of Spamhaus commented on my blog post about the current listings. I’m promoting it here as there is valuable information in it.
Read MoreSubscription bombing, ESPs and Spamhaus
A number of ESPs woke up to a more-than-usually-bad Monday morning. Last night Spamhaus listed 10s of networks, including ESPs, on the SBL. The listings all contained the following note:
Read MorePolitician sends spam, experiences consequences, news at 11
Over the weekend I’ve been seeing a number of over the top, hyperbolic blog posts about the Trump Campaign’s agency getting suspended from their ESP for spamming. Adestra suspended the Donald Trump campaign for “for committing some of the most egregious spamming in the history of the Internet in an effort to save his broke campaign.”
That quote about “most egregious spamming” is from some partisan website that is all about making Trump look bad. I did actually laugh out loud reading most egregious. Let’s be real here. This incidence of spamming doesn’t even make it into the top 100 of the ones I know about. And it’s not like I’m particularly well up on who’s spamming what.
This really is business as usual in the email space and particularly the political email space. Political sender, be they special interest groups or politicians, are sloppy with permission and will send mail to any email address they get their hands on. I talked about this last week: Spam Filtering is Apolitical
The Trump campaign isn’t the first political campaign to send spam. It wasn’t huge news in 2012, but the Romney campaign was doing some bad stuff with their email marketing. They were working with snowshoe spammers. They were listed on the SBL. They got cut off by their ESP.
While Spamhaus doesn’t keep historic records, I found a post from 2012 on the “Mainsleaze” about the Romney campaign / supporters and their use of spam as a campaign tactic. In the comments on that post a representative of Spamhaus says, “Entirely too many political operatives and some of those who work with them at ESPs feel entitled to ignore the usual rules and send opt-out bulk email to anybody they wish.” This is true, and something I’ve repeatedly mentioned on this blog.
Bounce handling is hard
Sometimes I find it hard to find a new topic to write about. I decide I’m going to write about X and then realize I did, often more than once. Other times I think I can blog about some issue only to realize that it’s too complex to handle in a quick post. There are concepts or issues that need background or I have to work a little harder to explain them.
One thing I haven’t blogged about before is bounce handling. That particular topic falls into the other category of posts that take a lot of time to write and need a significant amount of work to make sense. I was even joking with my fellow panel members at EEC a few months ago about how that’s a post that so needs to be written but I’m avoiding it because it’s so hard. There’s so much to be conceptualized and explained and I realize it’s not a blog post but multiple blog posts, or a white paper or even a book.
So let’s start with some simple definitions. Those of you who work at ISPs are probably thinking of bounces in terms of accept than reject, that’s not exactly what I’m talking about here. I’m writing these for senders, who usually call rejects during the SMTP transaction bounces.
Ugg, a spammer.
I’ve written before about how there is some (I’m sure lovely) woman in the UK who has been connected to my email address. I get a lot of mail for her. Mostly spam. She doesn’t seem to be using the address, but I regularly get mail addressed to MRS. LAURA CORBISHLEY (all caps, always). Typically these messages are advertising various UK stores and products. Sometimes they’re mortgage offers. A few have been sweepstakes only open to UK residents.
I generally forward these spams off to various blocklists with the note it’s my “UK spamtrap” and they take whatever actions seem appropriate to them. Today, though, I got my first US spam to Mrs. Laura Corbishly. From a Yesmail customer called sanuk.com. I’m getting a website error (they get smacked for spamming already?) but a little research tells me this is shoe company that owns a bunch of brands, including Ugg.
Today, though, I got my first US spam to Mrs. Laura Corbishly. From a Yesmail customer called sanuk.com. I’m getting a website error (they get smacked for spamming already?) but a little research tells me this is shoe company that owns a bunch of brands, including Ugg.
Yes, Ugg a Spammer. They even even have a disclaimer at the bottom of the email telling me they’re a spammer!
Not so much, no. It appears, though, that the data brokers selling Mrs. Corbishley’s name connected to my email address have figured out that no one ever actually acts on any of their UK offers. So now they’re selling into the US market in hopes that they might entice a purchase?
On a purely nosy level, I’d love to know who was selling the address. First off, I’d love to know where they got this info in the first place. Secondly, what horrible database are they using that keeps name data in all caps? (When I get email to this trap I think they’re shouting at me, as if I’m the one who is wrong about my name. Maybe they think if they yell at me loud enough will I decide I really am the happy wife of Mr. Corbishley of Swindon, UK. )
I do tell clients that it’s useful to remind customers that they signed up for mail, especially if they haven’t mailed for a while. So I know not every email with a “you opted in” reminder is spam, but I only notice those things when I haven’t opted in. It’s something I mostly gloss over if I really did opt-in. I wonder if this is how other folks react to “you opted in” notices, too.
I do recommend the reminder be much more specific than “you opted in at our website.” Give the user a date, a time, something that isn’t just something any company can, and many do, make up.
BlueHornet spun off from Digital River
Earlier this week, the investment firm Marlin Equity Partners announced they purchased BlueHornet Networks from Digital River. BlueHornet has been around for quite a while. In 2004 they were acquired by Digital River and run as a wholly owned subsidiary.
Congrats to the folks working at BlueHornet.
Dealing with blocklists, deliverability and abuse people
There are a lot of things all of us in the deliverability, abuse and blocklist space have heard, over and over and over again. They’re so common they’re running jokes in the industry. These phrases are used by spammers, but a lot of non-spammers seem to use them as well.
The most famous is probably “I’m sure they’ll unblock me if I can just explain my business model.” Trust me, the folks blocking your mail don’t want to hear about your business model. They just want you to stop doing whatever it is you’re doing. In fact, I’m one of the few people in the space who actually wants to hear about your business model – so I can help you reach your goals without doing things that get you blocked.
A few months ago, after getting off yet another phone call where I talked clients down from explaining their business model to Spamhaus, I put together list of phrases that senders really shouldn’t use when talking to their ESP, a blocklist provider or an abuse desk. I posted it to a closed list and one of the participants put it together into a bingo card.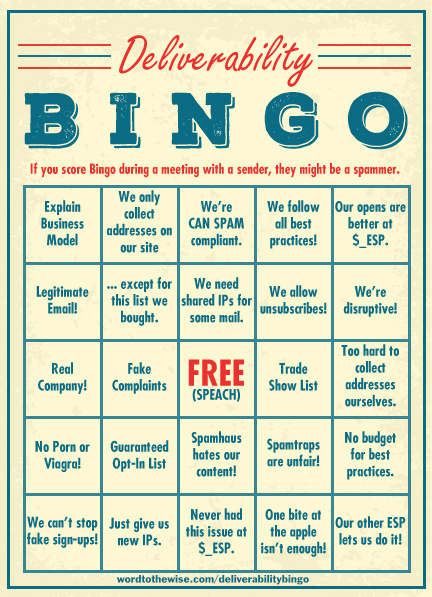
A lot of these statements are valid marketing and business statements. But the folks responsible for blocking mail don’t really care. They just want their users to be happy with the mail they receive.
VerticalResponse acquired
The acquisition of email service providers continues. Last week Deluxe (yes, the check printing people) acquired Vertical Response. This appears to be positioning themselves to improve their collection of business services to include email marketing.
Read MoreJust… make it stop
It used to be when I’d send in a complaint to an ESP, I’d want them to take it seriously. To actually fix their customer problems. To stop their customers from spamming. To fix the broken process that resulted in their customer thinking I asked for email.
These days? These days I just want the ESP to suppress my address and make the mail stop. Even better would be suppressing the address from their entire customer base – the only addresses I send in complaints for these days are traps.
Sadly, there are ESPs out there that can’t manage to stop customers from spamming people who have reported the spam. But, I am forever the optimist and keep sending the complaints when I think someone will care.
Spamming ESPs: the followup
Campaign Monitor contacted me about yesterday’s post. The phrasing I picked out of the spammers AUP matched their AUP quite closely. In fact, if you plug the AUP into Google, Campaign Monitor comes up as one of the first hits.
It was not Campaign Monitor I was talking about. In fact, the ESP I received the mail from is not on the first 8 pages of Google hits for the phrases I posted.
A similar thing happened when I posted about Dell spamming me. Dell has multiple ESPs, and one of their ESPs contacted me directly in case they were the ones Dell was spamming through. It was no surprise to me that they weren’t the ESP involved.
This is what good ESPs do. Good ESPs monitor their reputation and monitor what people are saying about them. Good ESPs notice when people claim they’re being spammed and effectively reach out to the complainers so they can investigate the claim.
Good ESPs don’t just rely on the complaint numbers to take action. They keep an eye out on social networks to see who might be receiving mail they never asked for.
Where do you accept reports?
One of the things that is most frustrating to me about sending in spam reports is that many ESPs and senders don’t actively monitor their abuse address. A few months ago I talked about getting spam from Dell to multiple email addresses of mine.
What I didn’t talk about was how badly broken the ESP was in handling my complaint. The ESP was, like many ESPs, an organization that grew organically and also purchased several smaller ESPs over the course of a few years. This means they have at least 5 or 6 different domains.
The problem is, they don’t effectively monitor abuse@ for those different domains. In fact, it took me blogging about it to get any response from the ESP. Unfortunately, that initial response was “why didn’t you tell us about it?”
I pointed out I’d tried abuse@domain1, abuse@domain2, abuse@domain3, and abuse@domain4. Some of the addresses were in the mail headers, others were in the ESP record at abuse.net. Three of those addresses bounced with “no such user.” In other words, I’d tried to tell them, but they weren’t accepting reports in a way I could access.
Every ESP should have active abuse addresses at domains that show up in their mail. This means the bounce address domain should have an abuse address. The reverse DNS domain should have an abuse address. The d= domain should have an abuse address.
And those addresses should be monitored. In the Dell case, the ESP did have an active abuse@ address but it was handled by corporate. Corporate dropped the ball and never forwarded the complaint to the ESP reps who could act on the spam issue.
ESPs and all senders should have abuse@ addresses that are monitored. They should also be tested on a regular basis. In the above case, addresses that used to work were disabled during some upgrade or another. No one thought to test to see if they were working after the change.
You should also test your process. If you send in a complaint, how does it get handled? What happens? Do you even have a complaint handling process outside of “count and forward”?
All large scale senders should have appropriate abuse@ addresses that are monitored. If you don’t, well, you look like a spammer.
Spear phishing
It’s been about a year since people started publicly talking about spear phishing attacks against ESPs and major emailers. There was a lot of energy put into talking about how to protect against future attacks. I have to wonder, though, how much of that talk translated into action?
What processes do you have in place to protect your company against attacks?
If you’re at an ESP, do you have the ability to scan your outgoing stream for keywords or domains?
If you’re a brand, have you implemented restrictions on which employees have access to your databases?
What have you done since the last set of attacks? Are you vulnerable if new attacks start?
More information on ESP attacks:
Be on the lookout
Time for a real security response
Email attacks
What's the best ESP?
I often get clients and potential clients asking me to tell them what the absolute best ESP is.
“You’re an expert in the field, which ESP will give me the best inbox delivery?”
The thing is, there isn’t an answer to that question.
ESPs have expertise in sending large amounts of mail. All have staff that manage and monitor MTAs. Most have staff that provide advice on delivery issues. Many have staff that handle abuse complaints, FBLs and blocks.
What they don’t have is magic delivery fairies or bat phones into postmaster desks.
Simply moving mail to an ESP won’t give you delivery. For the most part, delivery is the responsibility of the sender, whether they send mail through an in house system or through an ESP.
Delivery is primarily about how recipients react to a particular mail stream. Send mail recipients want, interact with and relate to and you usually see good delivery. The IP addresses or infrastructure contribute but do not dominate the equation. Sending from an ESP won’t fix poor content, irrelevant mail or unengaged recipients.
I can hear everyone now shouting at their screen “What about shared IPs!!!?!?!” Yes, yes, if you use an ESP with shared IP addresses and the ESP gets a bad customer you may see poor delivery for a time because one of their other customers was bad. It’s a fact, it happens. Plus, if you use an ESP with dedicated IPs and the ESP gets a bad customer you may see poor delivery for a time because one of the other customers was bad and their IP is near yours.
So clearly the answer is to bring email in house. That way no other company can affect your delivery, right? Yes. Kinda.
Are you willing to invest money in hiring email and DNS savvy sysadmins? Invest money in a MTA designed to handle bulk mail? Invest in an expert who not only understands bounce handling, but can explain to your developers what a good bounce handling system must do? Invest in someone who can manage authentication like DKIM? Who can handle delivery issues and understands how to talk to ISPs? Invest in development to write a FBL processor?
For some companies, the internal investment is the right answer, and bringing mail in house makes business sense.
For a lot of companies, though, they just want to use email to communicate with customers. They don’t want to have to invest in multiple staff members (as it’s very rare to find a single person with all the various skill sets needed) to just send a weekly newsletter, or daily sales email. They need a tool that works, they don’t need to know how to sign up for a FBL, they don’t need to know how to handle bounces. They can outsource that work and focus on the communication value.
Finding the best ESP starts with finding out how you want to use email.
Question 1: What role does email play in my business?
First spam to Epsilon leaked address
This morning I received the first two spams to the address of mine that was compromised during the Epsilon compromise back in April. Actually, I received two of them. One was the “standard” Adobe phish email. The other was similar but referenced Limewire instead of Adobe.
Read MoreESPs being targeted
There has been an ongoing, concerted attack against ESPs recently. Today ReturnPath published some of what is known about the attack.
Read MoreReturn Path Changes certification standards
Return Path recently announced changes to their certification program. They will no longer be certifying 3rd party mailers.
Read MoreProject Omnivore
Ben at Mailchimp has posted some information about Project Omnivore. This is a predictive system that not only predicts potential abuse, but can also be used to predict poor campaigns. Steve and I had a chance to see Omnivore in action when we were in Atlanta last fall, and were impressed by the accuracy for bad stuff. It seems, however, that Omnivore is useful to predict good behaviour as well.
Read MoreDelivery case study
Mailchimp published a case study looking at a customer moving from sending in house to using Mailchimp.
Read MoreYour delivery is yours, not your ESPs
Ken is right. As he almost always is.
I received a cold-call voicemail yesterday from a representative of an e-mail service provider looking to do a barter deal.
Read More
Never mind I’m not the person to approach for barter deals—or any other type of non-editorial issue, for that matter—the sales rep made one statement that made me cringe.
“Our delivery rates are very high,” she said.
That statement has no place in a pitch from an e-mail service provider.
Monitoring customers at ESPs
In the past I’ve talked about vetting clients, and what best effort encompasses when ESPS try to keep bad actors out of their systems. But what does an ESP do to monitor clients ongoing? Al Iverson from ExactTarget says that they:
Read More