Policies
Thoughts on policy
A particular blocklist, once again, listed a major ESP this week. Their justification is “this is our policy.” Which is true, it is their policy to list under these circumstances. That doesn’t make it a good policy, or even an effective policy. It’s simply a policy.
Read MorePolicy is hard
We’re back at work after a trip to M3AAWG. This conference was a little different for me than previous ones. I spent a lot of time just talking with people – about email, about abuse, about the industry, about the ecosystem. Sometimes when you’re in a position like mine, you get focused way too much on the trees.
Of course, it’s the focusing on the trees that makes me good for my clients. I follow what’s going on closely, so they don’t have to. I pay attention so I can distill things into useable chunks for them to implement. Sometimes, though, I need to remember to look around and appreciate the forest. That’s what I got to do last week. I got to talk with so many great people. I got to hear what they think about email. The different perspectives are invaluable. They serve to deepen my understanding of delivery, email and where the industry is going.
One of the things that really came into focus for me is how critical protecting messaging infrastructure is. I haven’t spoken very much here about the election and the consequences and the changes and challenges we’re facing. That doesn’t mean I’m not worried about them or I don’t have some significant reservations about the new administration. It just means I don’t know how to articulate it or even if there is a solution.
The conference gave me hope. Because there are people at a lot of places who are in a place to protect users and protect privacy and protect individuals. Many of those folks were at the conference. The collaboration is still there. The concern for how we can stop or minimize bad behavior and what the implications are. Some of the most difficult conversations around policy involve the question who will this affect. In big systems, simple policies that seem like a no-brainer… aren’t. We’re seeing the effects of this with some of the realities the new administration and the Republican leaders of congress are realizing. Health care is hard, and complex. Banning an entire religion may not be a great idea. Governing is not like running a business.
Talking with smart people, especially with smart people who disagree with me, is one of the things that lets me see the forest. And I am so grateful for the time I spend with them.
Censorship and free speech online
One of the things I discovered yesterday while looking at Krebs on Security was that Google Alphabet has a program to provide hosting and dDOS protection for journalists. Project Shield, as it’s called, is a free service for approved applicants that keeps up websites that might be taken down otherwise. Eligible organizations include those providing news, information on human rights and monitoring elections.
This is something I hadn’t heard of before and my only reaction is good for Google.
Look, we’ve gotten to the point where attackers have resources beyond the scope that most of us can imagine. It’s expensive even for large organizations to manage and pay for the level of protection they need.
Even more importantly a lot of very important work is done by individuals or small organizations. Brian is a prime example of that. He does an incredible job investigating online crime on his own time. His site and his information is an invaluable resource for many. Losing his site, and losing his information would leave a huge hole in the security community. There are other folks in other spaces who, like Brian, don’t have the resources to protect themselves but do have important things to say and share.
I’m glad to see Google committing their resources and skills to help organizations protect themselves. It’s so important that this work is done and we don’t lose voices just because they can’t afford hundreds of thousands of dollars a year.
There has been abuse and harassment online for as long as I’ve been here. But it seems recently the size and severity of attacks have increased. And a lot of service providers are struggling with how to manage it and what their responsibilities are.
A few weeks ago Facebook deleted an iconic photo from the Vietnam era due to child nudity in the photo. That decision was reversed and discussed in many, many different places. One of the most interesting discussion happened on a friend’s Facebook feed. Many of the participants work at various online providers. They have to make these kinds of decisions and create policy to do the right thing – whatever the right thing is. It was very interesting to be able to follow the discussion and see how many different issues FB and other online providers have to consider when creating these types of policies.
I thing the thing I have to confront the most about the internet is how big it is. And how crucial it’s become to all sorts of issues. Social media can be a cesspool of abuse, there’s no question. But it can also be a force for good. I’m glad companies like Google are stepping up to preserve the good parts of the internet.
How many blocklists do we need?
There’s been a discussion on the mailop list about the number of different blocklists out there. There are discussions about whether we need so many lists, and how difficult the different lists make it to run a small mail system (80K or so users). This discussion wandered around a little bit, but started me thinking about how we got to a place where there are hundreds of different blocklists, and why we need them.
There is a lot of history of blocklists, and it’s long, complicated and involves many strong and passionate personalities. Some of that history is quite personal to me. Not only do I remember email before spam, I was one of MAPS’ first few employees, albeit not handling listings. I’ve talked with folks creating lists, I’ve argued with folks running lists. For a while I was the voice behind a blocklist’s phone number.
The need, desire and demand for different lists has come up over the years. The answer is pretty simple: there are many different types of abuse. One list cannot effectively address all abusive traffic nor have policies that minimize false positives.
Lists need different policies and different delisting criteria. The SBL lists based on volume of email to addresses that are known to have not opted in to receive mail. The PBL lists IPs where the IP owner (usually an ISP) says that the IPs are not supposed to be sending mail by their policy. URIBL and SURBL list domains, not IPs. Some lists have delisting requirements, some let listees remove themselves.
The policies of listing and delisting are not one size fits all, nor should they be.
There are two widely used lists that have significantly different delisting policies: the SBL and the CBL.
The SBL focuses on IP addresses they believe are under the control of or supporting the services of spammers. They measure this by primarily relying on spamtraps, but they also accept forwarded mail from some trusted individuals. Getting delisted from the SBL means explaining to Spamhaus what steps were taken to stop the spam from coming. It’s a manual process with humans in the loop and can require significant business process changes for listees. (We’ve helped dozens of companies resolve SBL listings over the years, contact us if you need help.)
On the other hand, the CBL is a mostly automated list. It lists ources of mail that aren’t real mail servers sending real mail, but are sending a lot of stuff. As they describe it:
What to do when an important email bounces
Some emails are more important than others. I know, I know, all emails are important, but really, some are more important than others.
I’ve recently been decluttering by the simple expedient of enrolling in paperless statements for some of our accounts. We have a 1TB NAS, I’m not going to run out of storage space and I will have so much less paper to deal with. Plus, electronic searches are easier than digging through a file I’ve just shoved statements in for the whole year.
Some companies just let you sign up for statements online and don’t take any extra steps to verify your email address or tell you what happens if your email breaks. But at least one company has gone the extra mile to establish how they handle email bounces.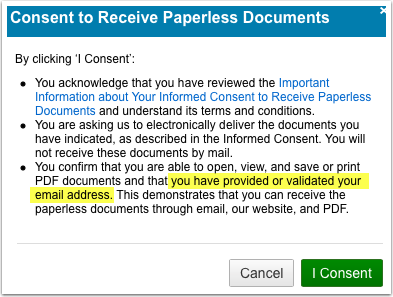
First, to sign up for paperless notifications I have to give my consent to receive docs. Even better, when I look at the important information it expressly details what happens if my email address bounces.
What she said
Jamie Tomasello on the Cloudmark Blog:
ESPs who require and enforce best permission practices should be applying peer and industry pressure within the ESP community to adopt these policies. Ultimately, ESPs need to take responsibility for their clients’ practices. If you are aware that your clients are engaging in questionable or bad practices, address those issues before contacting an ISP or anti-spam vendor to resolve the issue.
Read More
Unsubscribe policies
Our local brewpub has an email list. For various reasons I have multiple addresses on the list and finally decided that getting 4 copies of each mailing was silly. About a week ago, I sent in unsubscribe requests for 3 of the addresses. Today I get another 4 copies of their mailing. That’s not good. Luckily, I know one of the delivery folks at their ESP so I send her an email.
I know unusubscribes can take a few days to process, but it has been seven and CAN SPAM is pretty clear about the 10 day requirement. My first email to their delivery expert is just asking how long unsbs normally take. She responds they take 3 – 4 days. Uh Oh.
I tell her I unsubscribed these 3 addresses (with the unsub links) on 6/10 and received more email this morning. I did tell her that there were multiple subscriptions and they were all legit, but the reasons were really not important. Just that I didn’t want quite so many emails and their unsubscribe process seemed broken.
Now we get to the part where it all goes a wee bit pear shaped. The next email I get back from her explains why I am on so many lists. Fair enough. The more concerning bit is that they have not only gone through their database and unsubscribed all my addresses, but they have also found Steve’s addresses and unsubscribed those too. What the email does not contain is an explanation of why their unsubscribe process broke.
At this point I am a bit annoyed. I did not want all my addresses unsubscribed, just some of them. And the bit about unsubscribing Steve? That’s just silly and unnecessary. Another round of email ensued, pointing out this is bad and please put everything back how it was except please unsubscribe these three addresses I sent originally.
Things are back how they were, although the technical staff is still looking into how their unsubscribe process broke. The initial thought is that during a technology transition they lost some unsubscribe requests.
This whole process has bothered me for a number of reasons. One is the utterly cavalier attitude of the delivery people at the ESP. Their unsubscribe process broke. This is, to my mind, an emergency. ESPs have been fined for broken unsubscribe processes. Two is the process of unsubscribing addresses that belonged to a completely different person. The ESP did explain the policy behind that, sorta.