Virus
Botnet activity warning
A bit of advice from the folks at the CBL, posted with permission and some light editing. I’ve been seeing some folks report longer connection times at some places, and this might explain some of it. It’s certainly possible, even likely, that the large ISPs are getting a lot of this kind of traffic.
A botnet, likely a variant of cutwail, has been for the past several years been specializing in using stolen credentials, doing port 25/587 SMTP AUTH connections to the spoof’d users server, and attempting to relay thru the connection to elsewhere. They will also, in some cases, attempt to log into the MX IP using a brute force attack against the email address. Other miscreants try the same thing with IMAP or POP or even SMTPS.
If they manage to compromise an email account, they use the account to send spam. For corporate accounts they can steal employee identities, request wire transfers, and send out corporately authenticated spam. If they get it, game over, the whole account is compromised and they can and do wreak havoc.
This has been going on for a couple of years, and now is the largest volume of spam from botnets. Cutwail is not the only botnet doing AUTH attacks, but appears to be the most prolific. Attacking POP and IMAP appears to be more recent, and is more related to spear-phishing (spamming executives) and other bad things.
In the last month or two, the behavior has changed a bit. The infections are trying to establish as many connections simultaneously as it can get away with. This is similar behavior to ancient or unpatched versions of qmail. This is swamping some servers by tying up a significant number (or even all) of the TCP sockets available.
The CBL is recommending that folks check their mail servers. If the mail server has a “simultaneous connection per IP limit”, it should be set to some limited number. If it’s not set then set it. Otherwise, your server is at risk for being unable to handle real mail. Make sure your IMAP and POP are secured as well as they are being targeted, too.
The XBL can also help with this. But securing your server is the first step.
Anatomy of a successful phishing attempt
Earlier this year the Exploratorium was the victim of a phishing attack. They’ve posted an article on what happened and how they discovered and dealt with the issue.
But they didn’t just report on the attack, they dissected it. And, as is appropriate for a organization with a mission of education, they mapped out what they discovered during the investigation.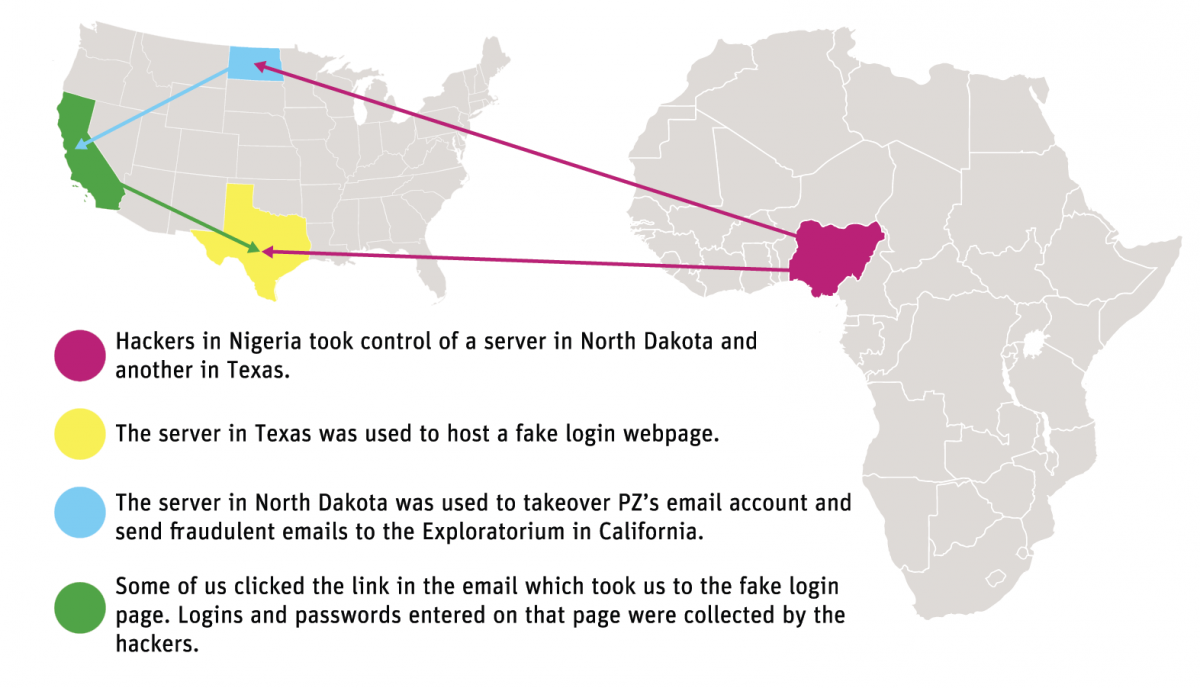
There are a couple of things that stand out to me about this attack. One is that of the more interesting pieces to me is that there was a delay between the compromise and the start of the attack. The Exploratorium calls it “the pivot” and describes it as the hacker deciding what to do next. The second is that the phisher actively interacted with the victim’s account. All new mail was sent to the trash automatically so she wouldn’t see incoming mail. Some mail was actively replied to so more people would click on the message. The phisher took steps to retain access to the account for as long as possible.
One thing that the Exploratorium didn’t see was any actual access to Exploratorium files or information. That may be because the Exploratorium itself wasn’t the target. Once a phisher / hacker has access to the email account, they have access to almost everything in your online life: calendars, bank accounts, credit accounts, the list goes on. Email addresses are our online identity and getting access to the address can open access to so much more.
Quite frankly it can happen to any of us. Earlier this week we received a phishing message that looked very plausible. It came from a law firm, mentioned a subpoena and even had an attachment personalized to our company. The attachment wasn’t opened so we were fine, but I can see how that kind of email might trick someone into getting infected.
We all need to be careful online. Email is a wonderful thing, but it’s insecure. It’s a great way for criminals to get into our space and wreck havoc on our computers and our lives.
Ransomware email protected by DMARC
Virus bulletin has an interesting post about DMARC and how some criminals are protecting their emails with DMARC.
Read MoreEmail is inherently a malicious traffic stream
It’s something many people don’t think about, but the majority of the traffic coming into the SMTP port is malicious. Spam is passively malicious, in that it just uses resources and bothers people. But there is a lot of actively malicious traffic coming into the SMTP port. Email is used as a vector to spread viruses and other malware. Email is also used for phishing and scamming. Many of the major hacks we’ve heard about over the last few years, including those in the email space, started with a single user getting infected through email.
We talk a lot about delivery here with clients and primarily focus on making sure their mail looks as unlike malicious mail as possible. We focus on spam filters, but every piece of mail goes through filters that also look for viruses, phishes, malware and other malicious traffic.
Mail servers are under attack constantly. The only reason our inboxes are useful is through the hard work of many people to filter out the bad and keep users from seeing the bulk of the mess attacking them.
DNS Changer servers going offline
There are a whole host of different botnets. One botnet run by Rove Digital infected computers with viruses that changed their DNS settings, giving the botnet runners the ability to control how the infected computers viewed the Internet.
The criminals behind the DNS Changer virus were arrested in November of last year. The court ordered the Internet Systems Consortium (ISC) to operate replacement DNS servers for computers infected with the botnet viruses in order to give users a chance to clean and fix their computers.
That court order expires on Monday.
Anyone who is still infected with the DNS Changer malware will see their internet services greatly curtailed when the DNS servers go offline.
If you run Windows and you haven’t yet checked to see if you’re infected, you should do so soon. There are a number of websites you can visit that will tell you if you are actually infected with the DNS changer virus and if you are will give you information on how to fix your system.
Government and botnets
The US government is looking at telling ISPs how to deal with compromised customers and botnets.
They’re a bit late to the party, though. Most of the major commercial ISPs have been implementing significant botnet controls for many years now. Control involves a number of different techniques, but notification has been designed into the system from day 1.
Uptick in botnet spam
There’s been a heavy uptick in botnet spam over the last few days, judging by things I’m hearing and my own mailboxes. There are a few common subject lines, but all of them are trying to get recipients to either run programs or visit malicious web pages.
The first subject line I’m seeing a lot of is “<name> wants to be friends with you on facebook!” In my mailbox most of those names have not been common European names. The give away that this isn’t actually a Facebook invite is the Reply-To address pointing to Linkedin. The URLs in the message appear to be random strings of numbers, and may actually encode recipient information in them.
The second has a subject that that is a variation on “End of July Statement.” The spammers are mixing capitals, adding in “Re:” and “FWD:” and sometimes increasing the urgency by adding required or STAT!! to the mail. These mails contain a .zip file which probably contains some virus which will turn the recipient machine into the next spam spewing bot.
The third variation has the subject line “Uniform Traffic Ticket.” The content is a citation that tells the recipient they were speeding somewhere in New York (possibly other states, I have only done a spot check of the couple hundred copies I have). There is, however, a .zip attachment with a virus.
Most people probably aren’t seeing these. SpamAssassin is doing a reasonably good job here of catching the spam and filtering it. I’m sure that the bigger ISPs are also filtering it effectively. But one person did forward a copy of the spam to a mailing list and ask if anyone knew what was going on.
If you get any of these messages, you don’t need to ask. It’s virus spam. Don’t open it and don’t forward it.